2023 Other CTFS
Info
Other CTFs from various sources
Forensics
Keys to the kingdom
Info
https://ghosttown.deadface.io/
Objective
Extract image from pcap
Solve
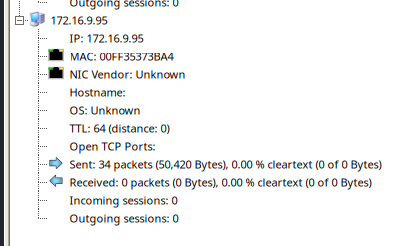
Get an insight via network miner
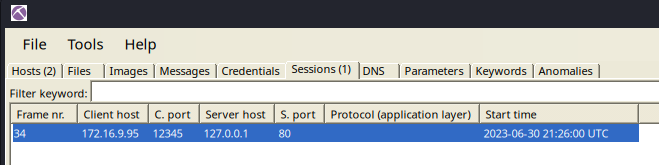
Image was transferred with multiple tcp streams
And it looks like a FJIF file
Lets grab the data from all tcp streams and merge to a file (can be better done via scrapy)
1
2
3
4
5
┌──(bravosec㉿fsociety)-[/tmp]
└─$ mkdir tcp_dumps
┌──(bravosec㉿fsociety)-[/tmp]
└─$ for i in $(seq 0 40); do tshark -q -r Thekeytothekingdom.pcap -z follow,tcp,raw,$i > tcp_dumps/$i; done
1
2
3
4
5
6
┌──(bravosec㉿fsociety)-[/tmp]
└─$ cd tcp_dumps
┌──(bravosec㉿fsociety)-[/tmp/tcp_dumps]
└─$ ls
0 1 10 11 12 13 14 15 16 17 18 19 2 20 21 22 23 24 25 26 27 28 29 3 30 31 32 33 34 35 36 37 38 39 4 40 5 6 7 8 9
1
2
┌──(bravosec㉿fsociety)-[/tmp]
└─$ xonsh
1
2
3
4
def get_data(content:str):
if len(content.split()) != 15:
return
return content.split()[-2]
1
datas=[get_data($(cat @(f))) for f in $(ls).splitlines()]
1
2
3
for d in datas:
if d:
$(echo @(d) >> result.raw)
1
bravosec@fsociety /tmp/tcp_dumps @ xxd -r -p result.raw result.out
Result :
Reversing
Challenge 1
Info
Unknown source, from DC user
Objective
Extract user password from a binary
Solve
Enum
1
2
3
┌──(bravosec㉿fsociety)-[/media/sf_kali-share]
└─$ file SuperBrowser-cli
SuperBrowser-cli: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=18409341e784ffa6662849dd9d139bb70e86e715, for GNU/Linux 3.2.0, not stripped
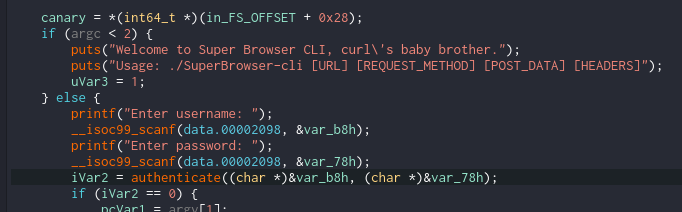
Using Cutter; It asks for a URL as argument
Then check if user input credentials matches encrypted hard coded credential
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
undefined8 authenticate(char *arg1, char *arg2)
{
int32_t iVar1;
undefined8 uVar2;
int64_t in_FS_OFFSET;
char *var_108h;
char *s1;
char *src;
int64_t var_e0h;
int64_t var_d8h;
int64_t var_d0h;
int64_t var_c8h;
char *dest;
char *s2;
int64_t canary;
canary = *(int64_t *)(in_FS_OFFSET + 0x28);
src._0_4_ = 0x6a72666f;
src._4_2_ = 0x78;
stack0xffffffffffffff18 = (char *)0x597a57665372404e;
var_e0h = 0x40685f7a30645f74;
var_d8h = 0x33617130785f7973;
var_d0h = 0x59685f786e6d595f;
var_c8h._0_4_ = 0x3839306b;
var_c8h._4_2_ = 0x37;
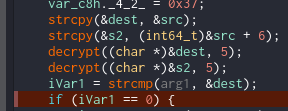
strcpy(&dest, &src);
strcpy(&s2, (int64_t)&src + 6);
decrypt((char *)&dest, 5);
decrypt((char *)&s2, 5);
iVar1 = strcmp(arg1, &dest);
if (iVar1 == 0) {
iVar1 = strcmp(arg2, &s2);
if (iVar1 == 0) {
uVar2 = 1;
goto code_r0x5615552d8814;
}
}
uVar2 = 0;
code_r0x5615552d8814:
if (canary != *(int64_t *)(in_FS_OFFSET + 0x28)) {
uVar2 = __stack_chk_fail();
}
return uVar2;
}
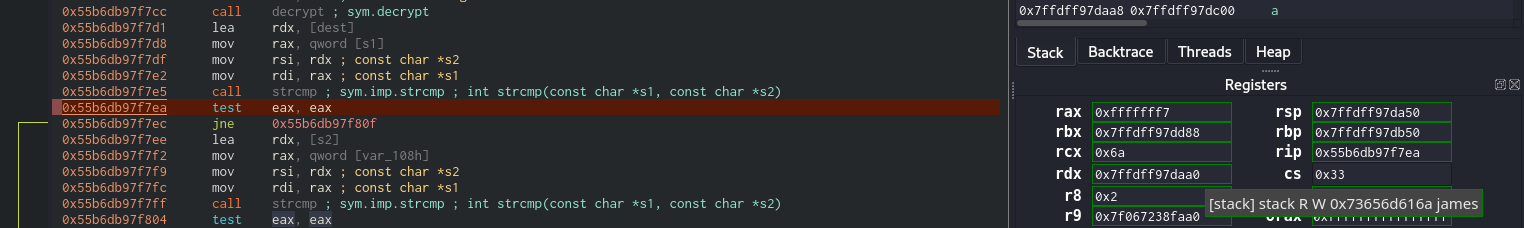
Debug program to get register values
Press F2 to set a breakpoint on if statement after username and password were decrypted
Press F9 to start debugger
Press CTRL + ` to open console
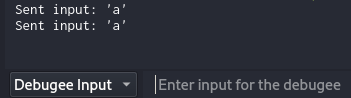
Send two inputs for username and password
Continue to the breakpoint
Now I can see the username james at rdx
Show in -> Hexdump
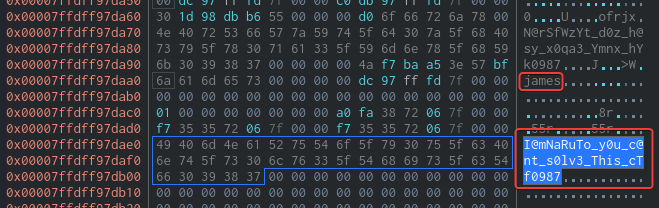
Now we get both username and password
james:I@mNaRuTo_y0u_c@nt_s0lv3_This_cTf0987